Exploit.SWF.bd „Virus“ Scam – Remove It
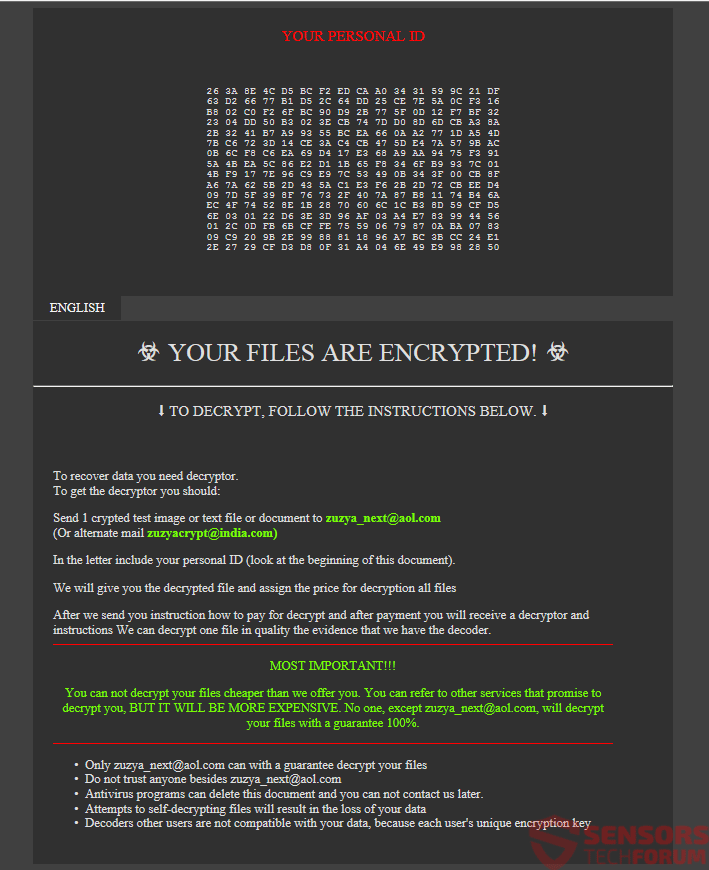
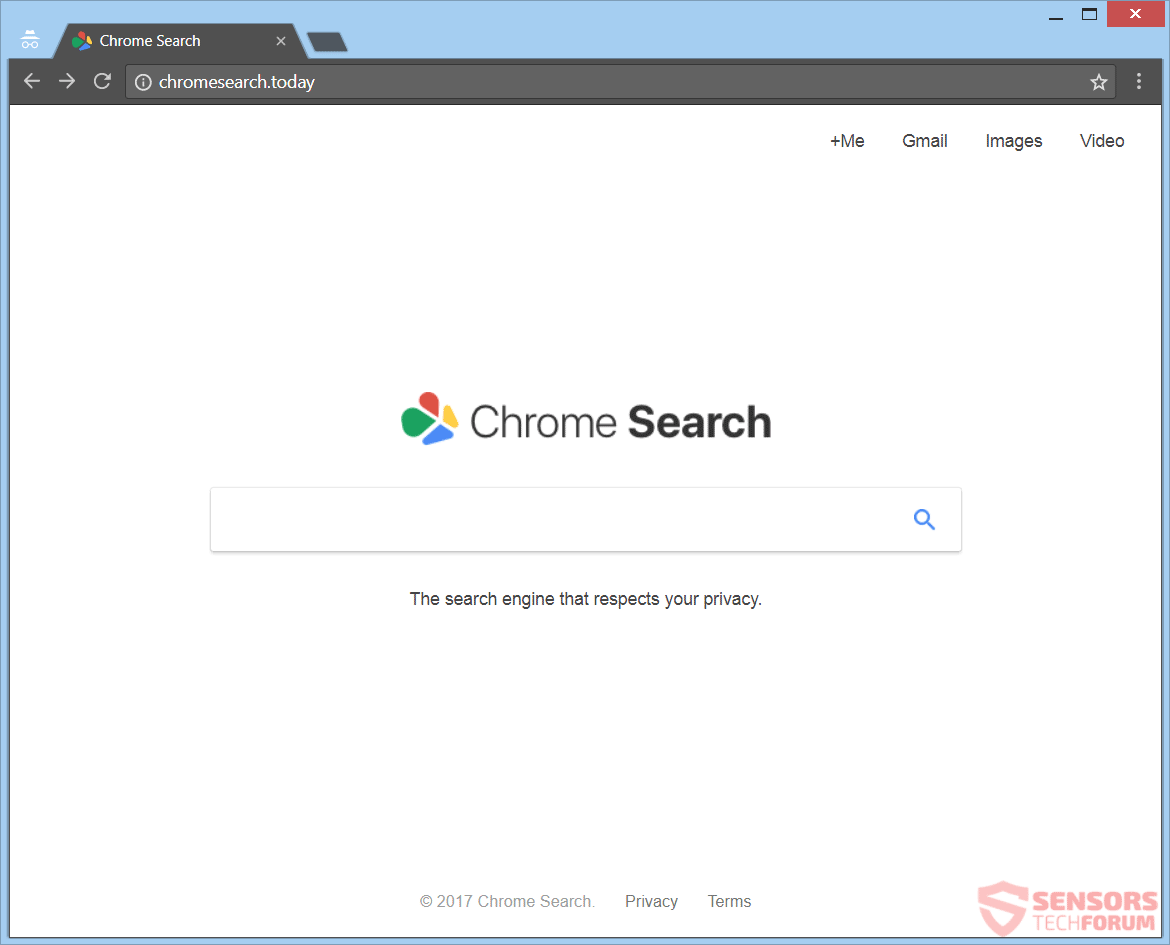
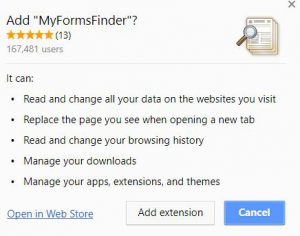
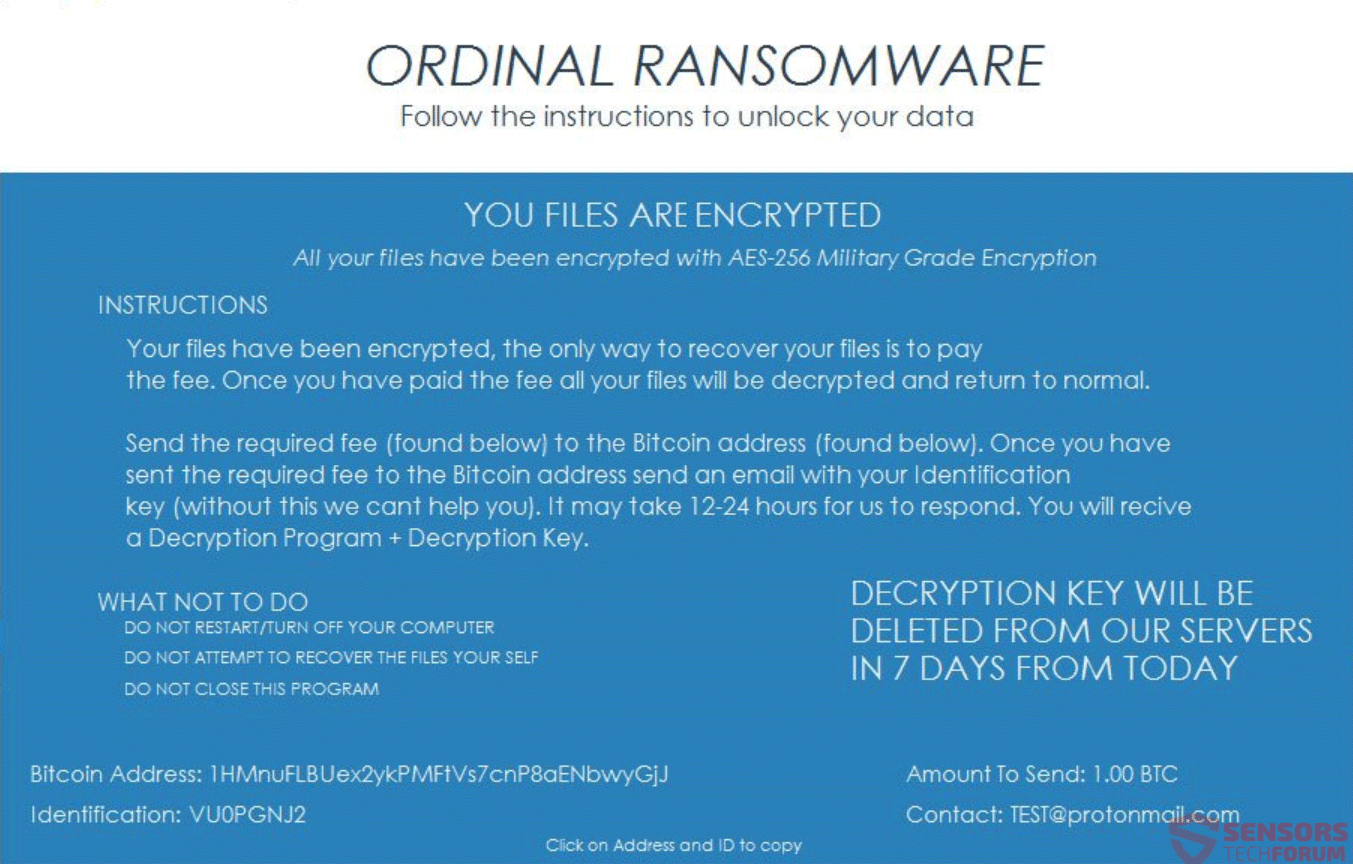
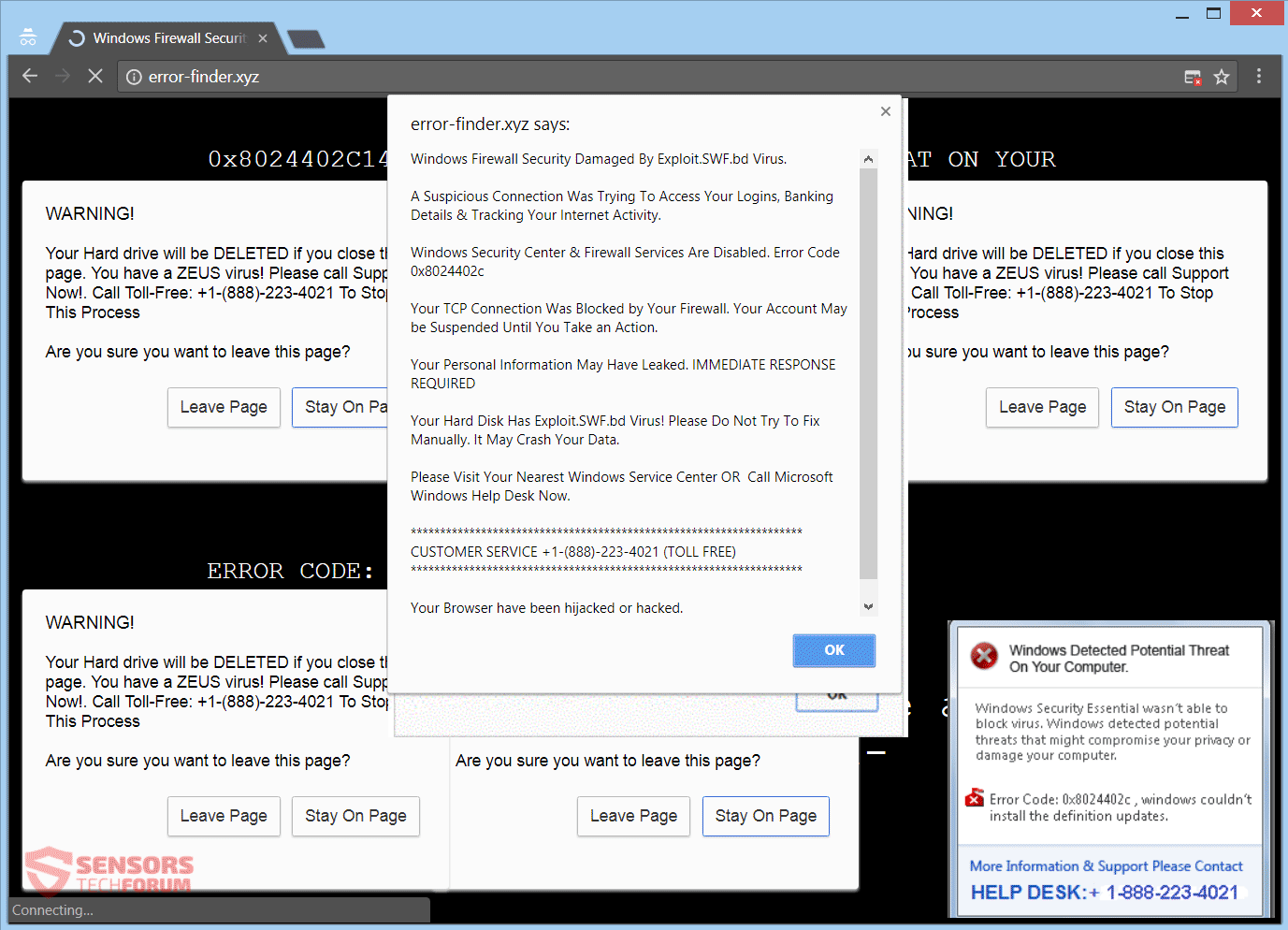
This article will aid you to remove the Exploit.SWF.bd „Virus“ scam totally. Follow the tech support scam removal instructions at the end of the article. Exploit.SWF.bd „Virus“ is seen in messages on various websites that host a tech support scam…