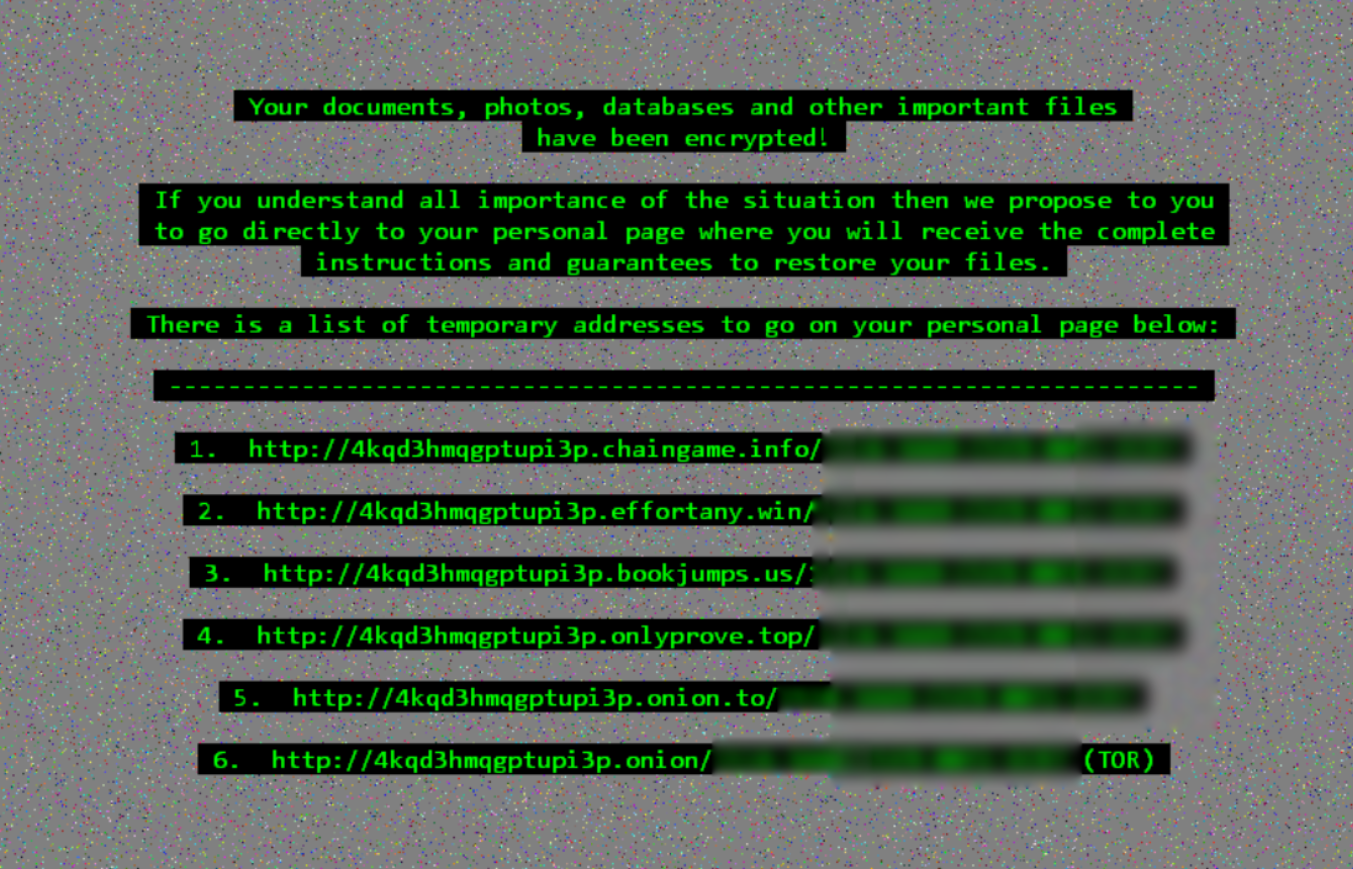
Remove Yayzap(.)com Gaming Adverts Absolutely
Yayzap(.)com is a website related to gaming online. The games on the website are mostly run on Flash, but some require HTML5 instead. The website can have a related application installed on your personal computer. Yayzap is considered adware due…