Win32/Delf.NRJ is a Trojan horse written in the Delphi programming language. The Trojan opens a backdoor on a compromised computer and may steal data, perform DDoS attacks or run executable files.

Threat Summary
| Name | Win32/Delf.NRJ |
| Type | Backdoor, Trojan |
| Short Description | The Trojan opens a backdoor. The backdoor can give unauthorized, remote access to a computer to a hacker. |
| Symptoms | Through the backdoor, a hacker may steal data, may perform Denial of Service attacks or run executables. |
| Distribution Method | Targeted Attacks, Email Attachments |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss Win32/Delf.NRJ. |
Win32/Delf.NRJ Trojan – Distribution Methods
One method of getting infected with the Win32/Delf.NRJ Trojan horse is by installing it manually as software pretending to be useful. So, without knowing, you are getting the Trojan injected into your computer, instead. Another distribution method spreading the infection is via browser exploits, such as plugins, extensions, or suspicious sites with malicious code inside them.
You may get infected with the Trojan from a targeted attack by downloading an attachment from an email. Files that can be used to distribute Trojans like Win32/Delf.NRJ, usually have these extensions: .bat, .exe, .vbs, .pif, .scr.
Win32/Delf.NRJ Trojan – In Detail
Win32/Delf.NRJ is classified as a Trojan horse. It is written in the Delphi programming language. It has the potential to infect your computer with more malware as it opens a backdoor on it. From that backdoor, a hacker gains access from a remote location.
According to researchers, once the Trojan is executed it starts searching for .exe files and when it finds any such files, it begins renaming them. It usually puts the letter G in front of those files:
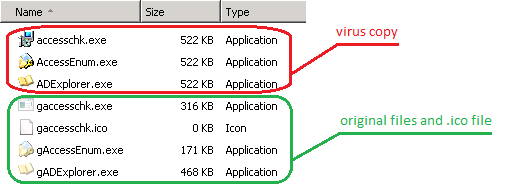
Image Source: Microsoft
After these operations, the Trojan will modify Windows Firewall settings, and connect remotely to a URL address. It uses the UDP, HTTP protocol to do so.
Via that backdoor, the Win32/Delf.NRJ Trojan may perform a number of malicious actions. Actions such as: moving, reading, executing, downloading, creating, deleting, and copying files; enumerating running processes. The Trojan can also perform DDoS attacks, open specific URLs in your browsers and also run various executable files which might contain malicious code.
The Win32/Delf.NRJ Trojan is dubbed like that by ESET researchers, and the name has gained popularity. But it also has the following other aliases:
- Backdoor.Win32.Delf.mrx (dubbed by Kaspersky)
- W32/Renamer-K (dubbed by Sophos)
- Backdoor.Win32/Grenam.A (dubbed by Microsoft)
Via the connection to the remote locations, the hacker behind the Trojan may also steal sensitive data and files.

Remove Win32/Delf.NRJ Trojan Completely
This Trojan can spy on you, access personal information on your PC and may infect you with different malware eventually. It may track your personal information and send all that to hackers, from which they can profit. To completely get rid of the Win32/Delf.NRJ Trojan horse from your PC, carefully follow the step-by-step removal instructions provided below.


Leave a Comment