A Spectre variant 4 vulnerability has been identified in the Linux kernel and represents a very dangerous threat to all affected machines. All system administrators are urged to apply the latest updates as soon as possible to mitigate any possible impact.
New Spectre Variant 4 Identified, Update Now! (CVE-2018-3639)
The newest Spectre vulnerability dubbed Variant 4 has been identified by security researchers Jann Horn and Ken Johnson. According to their findings this new attack gives potential hackers induce powerful intrusions into target systems. Its interesting to note that the two experts discovered the threat independently of each other and have published information about the vulnerability. This new Spectre version is also tracked with a unique identifier called CVE-2018-3639 that is assigned to the affected packages. It also allows specialists to track how the Linux distributions are amending the threat by responding in a timely manner with kernel updates.
The main reason why the bug is rated severe is the fact that it uses the microprocessors code itself. As a result of improper handling it allows for speculative execution of a Linux kernel memory read operation. This is done before the addresses of prior memory actions are fully complete. As a result criminals can reveal sensitive information about the machine. Practically all Linux kernels are affected including special images, a partial list taken from several major distributions reveals the following examples:
- Linux Kernel for Desktop users
- Linux kernel for Amazon Web Services (AWS) systems
- Linux kernel for Microsoft Azure Cloud systems
- Linux kernel for Google Cloud Platform (GCP) systems
- Linux kernel for cloud environments
- Linux kernel for OEM processors
- Linux kernel for Virtualization servers
- Linux kernel for SAP solutions
- Linux kernel for various servers
Warning! System administrators are advised to update virtualization systems (QEMU and others) and Microcode packages as well due to the fact that the attack can be performed against these services as well. At the moment Intel is working with the Linux community to release patches as soon as possible. In the meantime affected users can access updated microcode via OEM firmware updates.
Related Story: Meltdown and Spectre Exploits Endanger Generations of Computers
How To Check if You are protected from Spectre Variant 4 (CVE-2018-3639)
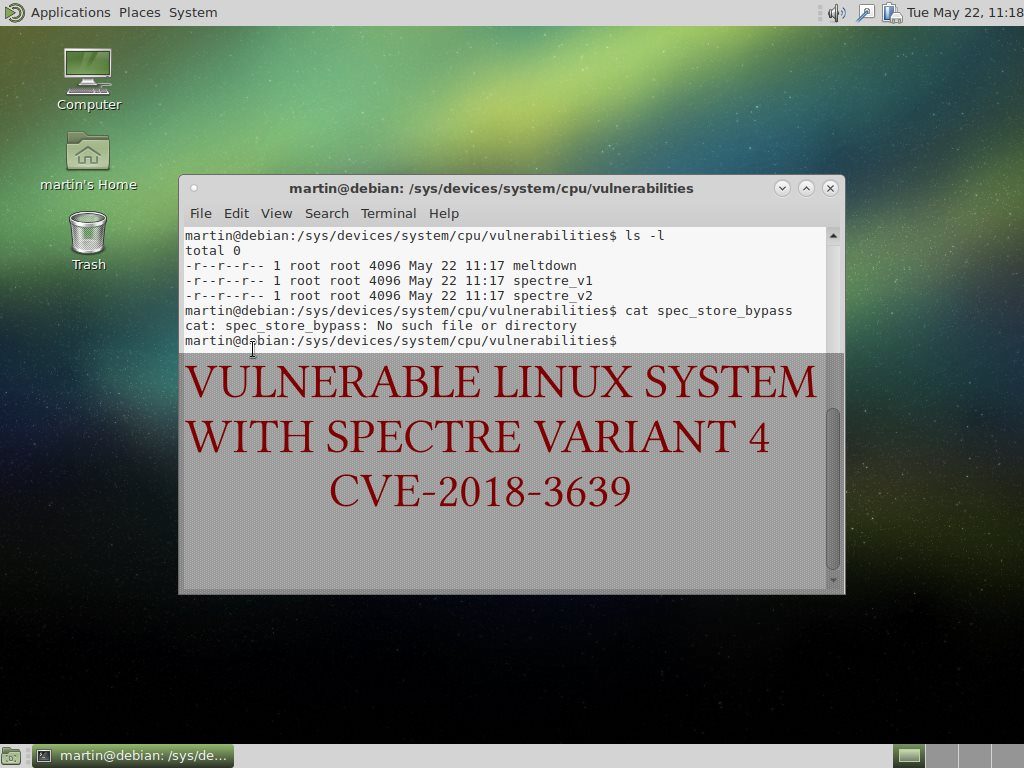
The updated packages released by the distributions and the hardware vendors when applied will protect the affected machines. The system administrators can check this by running a simple command:
$ cat /sys/devices/system/cpu/vulnerabilities/spec_store_bypass
There are three possible outputs that signal the state of the machine:
- Mitigation: Speculative Store Bypass disabled via prctl and seccomp — This means that the system is protected.
- No such file or directory — The system is vulnerable to the Spectre 4 variant.
- Vulnerable — The system does not feature updated microcode or an updated virtual machine hypervisor.
It has been found that some of the mitigation steps used in the Spectre v2 type can help to protect the Variant 4 machines to a certain extent. As this issue is also known as Speculative Store Bypass system administrators can attempt to manually set certain kernel values if they have not yet received an appropriate update. They will need to recompile their kernels with the following value turned on Speculative Store Bypass Disable (SSBD) in the IA32_SPEC_CTRL Model-Specific Register (MSR) section of x86 processors. Support for this however does require updated microcode for Intel processors.
By default in Ubuntu this is turned off by default as it is not needed by most applications and services and carries a notable performance impact. A certain PR_SPEC_STORE_BYPASS string enables developers to opt into the mitigation on a per process basis. However those applications that use a security filter (seccomp) will be implicitly opted in automatically. Examples include LXD containers, sandboxes and processes of the Firefox and Chromium browsers.
System-wide SSBD mitigation can be enabled by booting with the spec_store_bypass_disable=on boot parameter.


