After the initial discovery of a few Cisco routers being infected with a new type of malware, new scans indicate that almost 200 Cisco devices across the globe have a malicious IOS image put in place of the legitimate one. In this way, a backdoor is set, granting attackers access to a targeted network.
Infection Timeline
It all started last week, on the 15th of September, with the discovery made by FireEye researchers that 14 Cisco routers were infected with malware, which was only a theoretical threat up until that point. The devices were located in different enterprises, in four countries: India, Mexico, Philippines and Ukraine.
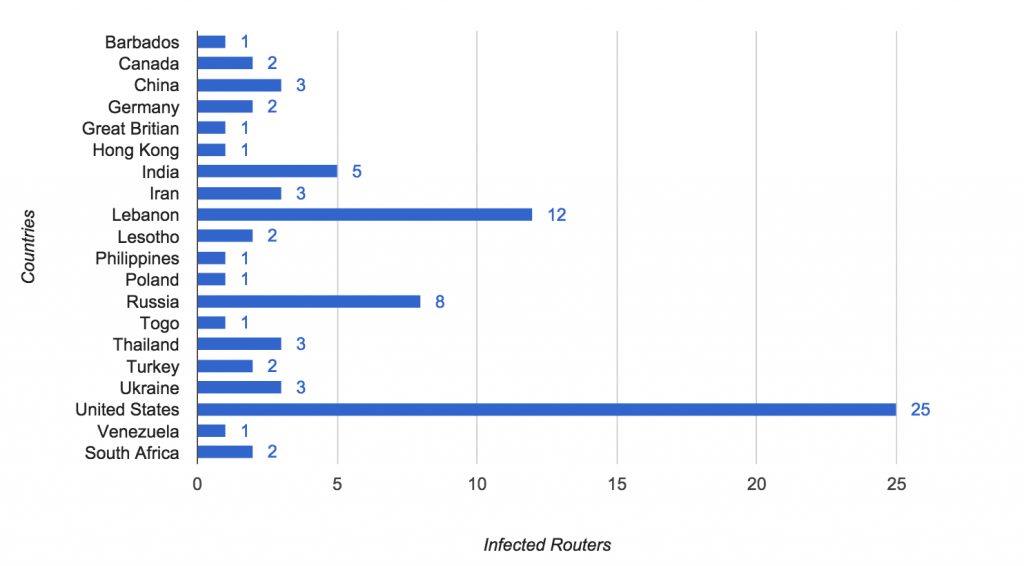
On the following day, ZMap researchers posted results from their scan of the public IPv4 address space with special TCP SYN packets. They have found “79 hosts displaying behavior consistent with the SYNful Knock implant”. They state that “these routers belong to a range of institutions in 19 countries.” And “25 hosts in the United States belong to a single service provider on the East Coast, and that the
hosts in both Germany and Lebanon belong to a single satellite provider that provides coverage to Africa”.
Image Source: Zmap
Two days ago, the Shadowserver foundation posted their own results from making a scan with collaboration with Cisco systems. Statistics on the Shadowserver site state that the infected hosts are a relative number as they have “identified 199 unique IP addresses that match the SYNful Knock behavior” and “163 unique systems”.
The numbers are growing and businesses from over 30 countries are affected. There is no telling how many more infected devices will be found in the future.
What is SYNful Knock?
The malware was given the name “The SYNful Knock Implant” due to the way it takes control over a lot of router’s modules and functions. The implant consists of a modified Cisco IOS Image that allows attackers to execute various functional modules.
Those modules are enabled via the HTTP protocol using TCP packets sent to the interface of the router. This particular process consists of a three-way handshake to be initiated and then completed. A uniquely crafted TCP SYN packet is sent to the targeted device, then the malware responds with a TCP SYN-ACK acknowledgement message of its own, which is answered by a third message to complete the counterfeit three-way handshake process.
The implant also provides unrestricted access with the help of a hidden backdoor password through the console and Telnet. The Cisco router models currently affected are 1841, 2811, and 3825.
Must Read
200,000 Devices Threatened by Heartbleed Bug
Backdoor.ATM.Suceful Severe ATM Malware
The SYNful Knock malware is a very severe threat that is very difficult to detect. It can be updated, utilize up to 100 various modules and remain functional even after restarting the infected devices. Cisco Systems have created a related Event Page for their customers.
There is no reason to conclude, however, that only Cisco’s routers are being targeted. There can very much be other devices with modified images around the globe.