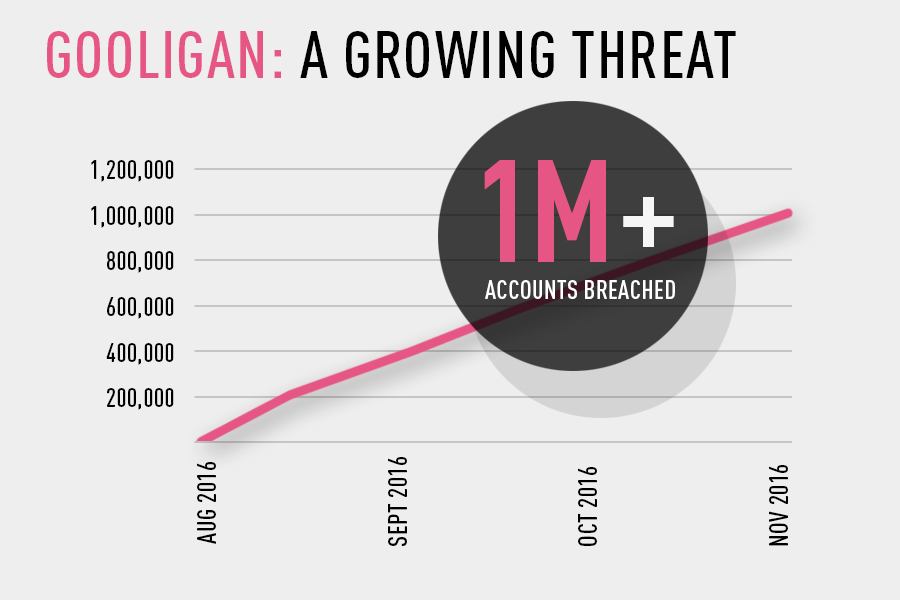
A new very dangerous malicious campaign was just discovered by researchers at Check Point. The attack campaign is dubbed Gooligan and succeeded to breach the security of more than one million Google accounts. Researchers say that this huge number continues to grow every day, with 13,000 breached devices on a daily basis.
Related: New Android Malware Targets 15 German Banks
The malware roots infected devices and steals authentication tokens. These tokens can be used to access data from Google Play, Gmail, Google Photos, Google Docs, G Suite, Google Drive, etc. This is in fact the same malware discovered last year in the SnapPea app. The Check Point team already contacted Google with their findings. The giant is currently investing Gooligan.
Adrian Ludwig from Google has already released a statement, saying that:
Several Ghost Push variants use publicly known vulnerabilities that are unpatched on older devices to gain privileges that allow them to install applications without user consent. In the last few weeks, we’ve worked closely with Check Point, a cyber security company, to investigate and protect users from one of these variants. Nicknamed ‘Gooligan’, this variant used Google credentials on older versions of Android to generate fraudulent installs of other apps. This morning, Check Point detailed those findings on their blog.
As visible, the malware in question is indeed a Ghost Push variant that is currently plaguing older versions of Android.
Who Is Affected by Gooligan?
According to the research, the malware is targeting devices running Android 4 (Jelly Bean, KitKat) and 5 (Lollipop). These versions of the operating system represent at least 74% of today’s in-market devices. 40% of these devices are found in Asia and 12% – in Europe. Numerous fake applications were discovered to have been infected with Gooligan. A list of apps that may have infected users with the malware can be found here.
Related: Would You Take a Selfie for Acecard Android Trojan?
If you have downloaded any of them, you may be infected. Researchers encourage users to review their application list in Settings-Apps to make sure they are safe… or not safe. In case of infection, an anti-virus product for mobile should be used as soon as possible.
Furthermore, users can also check whether their Google accounts have been breached by accessing a website created by the security company for the occasion.
If a user’s account has been breached, follow these steps:
1.A clean installation of an operating system on your mobile device is required (a process called “flashing”). As this is a complex process, we recommend powering off your device and approaching a certified technician, or your mobile service provider, to request that your device be “re-flashed.”
2.Change your Google account passwords immediately after this process.