 Ransomware infections have caused losses on an unimaginable global scale. For example, CryptoWall, just one virus has generated more than 180 million dollars in losses to individuals and organizations worldwide. And this was last year (2015). Now, ransomware infections have shown a rapid rise, leaving defenseless at the hands of cyber-criminals. But is there really a way to protect yourself by this crypto-malware. According to researchers who deal with reverse engineering of malware on a daily basis, there is a way out for most viruses and this way is known as network sniffing. In this article we aim to show you how to use network sniffing to discover the keys to unlock files encrypted by malware. But, be advised that there are many factors involved and this method may not work 100% for everyone.
Ransomware infections have caused losses on an unimaginable global scale. For example, CryptoWall, just one virus has generated more than 180 million dollars in losses to individuals and organizations worldwide. And this was last year (2015). Now, ransomware infections have shown a rapid rise, leaving defenseless at the hands of cyber-criminals. But is there really a way to protect yourself by this crypto-malware. According to researchers who deal with reverse engineering of malware on a daily basis, there is a way out for most viruses and this way is known as network sniffing. In this article we aim to show you how to use network sniffing to discover the keys to unlock files encrypted by malware. But, be advised that there are many factors involved and this method may not work 100% for everyone.

How Does Ransomware Work?
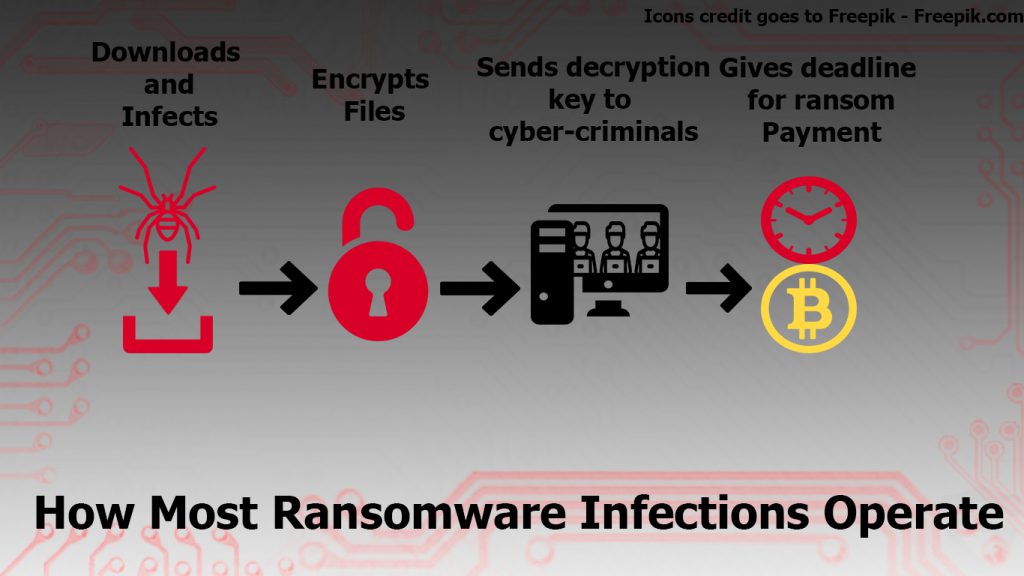
To demonstrate to you how to use a network sniffer, bear In mind that we first need to discover the process behind ransomware. Most crypto-viruses operate in a standard manner. They infect your computer, encrypt your files changing the extension and using AES or RSA cyphers to generate a public and private keys.
Related Article: Ransomware Encryption Explained – Understand How It Works and Why Is It So Effective
After it does that, the ransomware sends the unlock information (Private Key or Public Key or both) to the C&C command and control center of the cyber criminals along with other system information and then it places a ransom note that aims to drive you into paying. Most ransom notes, set a deadline.
Here is how most ransom viruses operate in a simple illustration:

How to “Get” the Encryption Information?
How to Decrypt Ransomware Files?
Since these keys are information which is sent out, there is a very simple method to get them. This is why we will focus on the following aspect of the ransomware operation sequence – the transfer of information:
Researchers have established that by using a network sniffer, such as Wireshark, you may trace the packets being transferred to the cyber-criminals’ IP address which is connected to your computer. This is why we have decided to create an instructive tutorial to assist you with catching ransomware on and “breaking its neck”(theoretically). Of course, different ransomware viruses operate in different ways (some may lock your screen, for example) and this is why this method may not be 100% effective. But for some malware such as SNS Locker, it works.
IMPORTANT:For the instructions below to work, you mustn’t remove the ransomware from your computer.
Network sniffing with Wireshark can be performed if you follow these steps:
Step 1: Download and Install Wireshark
For this tutorial to work, you will require Wireshark to be installed on your computer. It is a widely used network sniffer, and you can download it for free by clicking on the “Download Now” button below. By entering their official website via the link below you can choose the download pack for your operating system and version (Windows 32-bit, Windows 64-bit, macOS).
Enter Wireshark Official Download Page
Step 2: Run Wireshark and start analyzing packets.
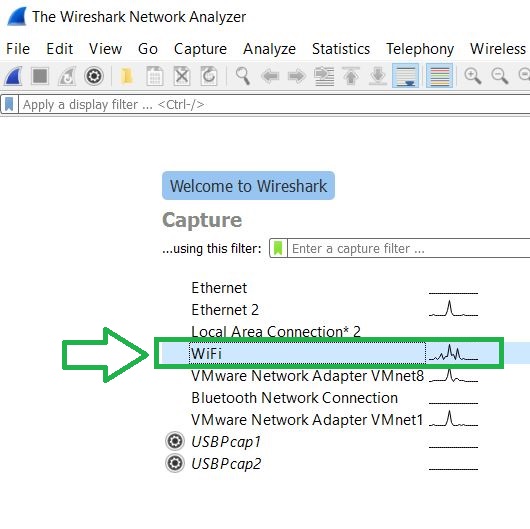
To begin the sniffing process, simply open Wireshark after installing it, after which make sure to click on the type of connection you want to sniff from. In other words, this would be your active connection mode with the internet. In our case, this is the Wi-Fi connection:
Step 3: Find the packet you are looking for.
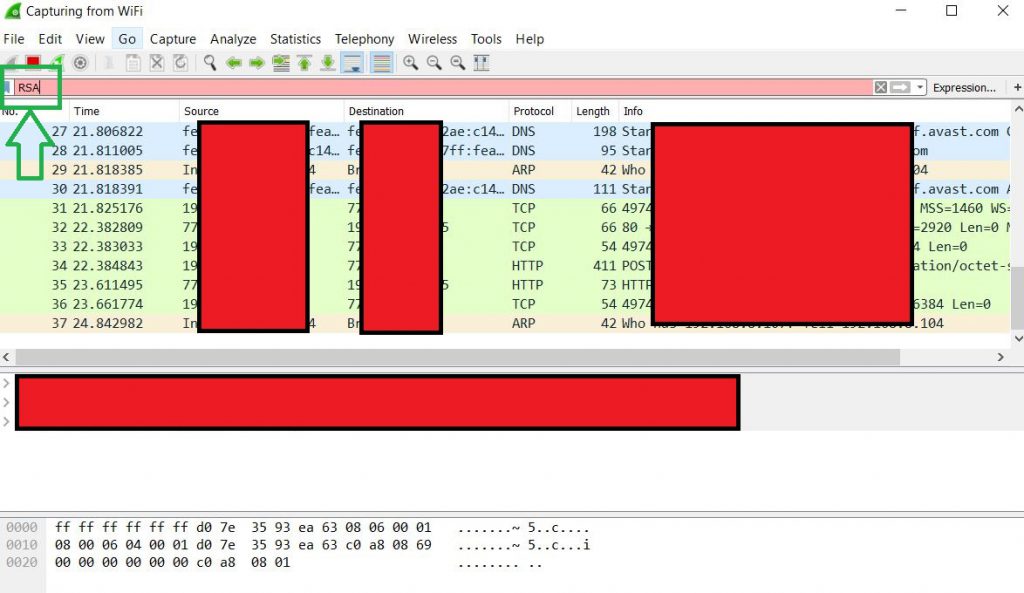
This is the tricky part because you will surely not know the IP address of the cyber-criminals. However, you may want to filter out the packets by typing different information in the filter above(Method 1). For example, we have typed RSA, in case there is information related to RSA encryption in the packets:
The most effective method, however(Method 2) is to watch the IP addresses and if they are not from your network, analyze all the traffic sent out to them by filtering them out based on different protocols. Here is how to find your network:
If you are using an IPV4 address, the first three octets or digits which are the same as your IP address are your network. If you do not know your IP address, to check your network simply open Command Prompt by typing cmd in Windows Search and then type the “ipconfig /all”. After it does that, go to your active connection (in our case Wi-Fi) and check your Gateway. The Gateway address is basically your network. The principle with IPV6 addresses is rather similar.
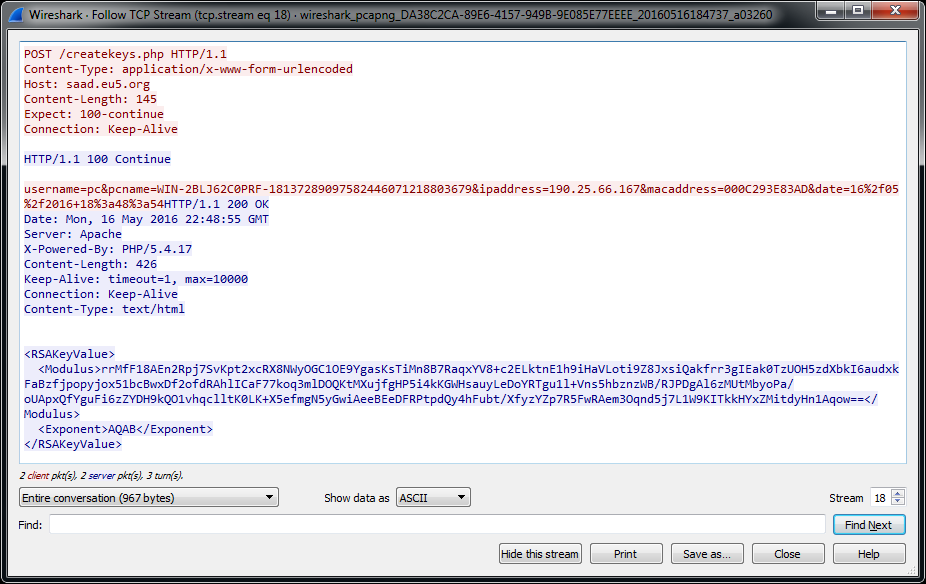
Step 3: Find the key:
After you have located the IP address of the cyber-criminals and you have discovered any information sent out from the virus to them, you may find a packet containing the encryption key. It may look like the picture, provided by Nyxcode below:

Does This Work In Real Life
Yes, this is a very effective method, but to do it, you need to be able to catch the malware in time. Most malware usually does those processes before the user even notices. This is why, if you are running a network, we recommend keeping Wireshark running at all times from another device, so that even if you get infected with the ransomware, you catch the information in time and decrypt your files.
There is also an option to deliberately use the malicious executable and infect another computer, to establish the decryption key and send it to malware researchers so that they can further develop decryptors and help you and other users as well.
Otherwise, you may still try it, since most ransomware viruses actively exchange information with C&C servers, but you need to be very careful since if you are watching the cyber-criminals, there is a good chance they are watching you if the ransomware is still active on your computer. We hope this is useful, and we wish you best of luck while network sniffing.




Will this work for cerber ?
Do you have any new info over it ?
Hello, Bilal Inamdar
Wireshark simply captures data segments transferred from your end device(PC) to other hosts it is connected with. So to answer your question, it will be best to say that Cerber has to have active connection with the host which is basically the C&C(Command and Control) center of the cyber criminals. Most ransomware viruses send out different information to such servers. If you use a network sniffer, you may get lucky and intercept the fragment of information which is your private key. This private key can then be used via a decryption software to decode your files. However, the bad news is that most ransomware viruses send the key immediately after encrypting your data. But most ransomware viruses also modify the registry key that runs the encryptor every time you start Windows. So if the ransomware uses different encryption keys every time it runs its encryptor it will send them every time you restart Windows and it encrypts new added files. If you are fast enough or use another PC with wireshark to capture the packets while the ransomware has still infected your computer, you may have a chance of sniffing out an encryption key. But then again, this encryption key may not be the same as the key before that. But this is how most ransomware viruses operate. Some viruses may use other strategy. So, as you can see there are a lot of factors, but all things considered, it is worth a try. : )
What is the best software to decrypt files if we know both public and private keys?
Hello Luccha,
It depends on the ransomware. Usually if the ransomware has its own decryptor it is best to use it. Otherwise, EmsiSoft have a variety of decryptors which can be tried via the trial/error method. Just keep in mind that there is no universal decryptor.
Keep in touch,
STF
the ransomware is cerber which I wanted to decrypt. I have sniffed some packets and found the public key. I found some more data which might be the private key. I would like to check it with a decrypter. Please recommend something that can work.
is very useful this info. Thanks. I was attcked by Crysis.E and still working in decryption
That is good to know. Thanks for the feedback.
Hi, thank you for this article
My computer is already infected with Locky and all my docx filed are crypted in .thor
On each folder, there is a file wich explain the method to uncrypt with a specific uncrypt code
Is there a way to uncrypt my files without to pay ?
Thank you for your help,
Romain
Hello, Romain, unfortunately for Locky ransomware, there has not been a breaktrough, allowing free decryption so far. But you are welcome to try alternative solutions, like Data Recovery tools, for example. sensorstechforum.com/top-5-data-recovery-software-which-program-suits-me-best/
Thank you for your responses
Unfortunaly, there is not shadow version of my files
I won’t pay for that for sure
I was wondering if there is a service who can brut force to uncrypt a small file with a matrice of computer ?
For exemple, if everybody who have been infected with Locky could share the power of his computer it could be possible to uncrypt the private key
Bye
Romain