It has now been discovered that even after a year of patching the cryptographic software library OpenSSL, changing passwords, and other security measures applied, the Heartbleed bug still poses a big threat. Thousands of devices are still prone to the vulnerability.
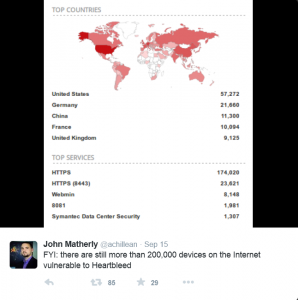
The discovery was made with the help of the IoT (“Internet of Things”) search engine Shodan. A couple of days ago, Shodan’s founder John Matherly made a tweet post with the staggering results of 200 thousands devices that are still exposed to the Heartbleed vulnerability.
The post also has a map illustration and more specific information as to where the majority of the liable devices are located. More than one-quarter of those devices are in the territory of the United States, a little more than twenty thousand in Germany, and around ten thousand in China, France and the United Kingdom.
In What Ways Can Shodan Help?
The search engine also provides regional and other more technical information. It gathers that kind of data among devices connected to the Internet, including such ones that other popular search engines usually discard. More specifically – everything that might be connected to the Web, such as servers, switches, routers, webcams, traffic lights, heart monitor implants, sensor systems (all in all, everything with an IP address that can transfer data over a network).
The in-depth statistics of Shodan should be able to aid administrators around the globe to track down which are the vulnerable devices, and get them fixed. Various security checks, server HTTP tests and making sure if a device is visible for outside networks are some of the useful tools of the search engine, which companies can use. In that way, they can effectively ensure they have the needed protection from the Heartbleed bug.
Will Administrators Make Their Networks Heartbleed-Free, Now?
This new, public information can also be a trigger for attackers to target the devices in question. In an official Venafi report a few months ago, it has been stated that in Global 2000 companies, somewhere around three-quarters of the devices that were affected by Heartbleed have not been fully “remediated”. Which means that most of those companies have not made their utmost best to secure their network devices from such a big threat, and until that is done, there may never be an end to the Heartbleed vulnerability.
What do you think about this? Should OpenSSL be patched once again? Should people make a bigger effort to ensure their devices are Heartbleed-free this time around? Or both of these things? What would you do?