This article is about a recent ransomware threat that has hit thousands of Hewlett-Packard Enterprise Integrated Lights-Out 4 interfaces or HPE iLO 4 for short. These interfaces provide access to HP Enterprise servers and their remote control. The ransomware threat is encrypting the hard drives of the servers and then demanding Bitcoins as a ransom to restore the files within the drives. A security researcher that goes by the twitter handle @M_Shahpasandi has been the first to make the discovery of the attack.
What Is Hewlett-Packard Enterprise iLO and Related Interface?
iLO is a remote server management processor embedded on the system boards of Hewlett-Packard Enterprise ProLiant servers and Synergy compute modules. The management processor enables the monitoring and controlling of servers from remote locations. HPE iLO management is a powerful tool that provides multiple ways to configure, update, monitor, and repair servers remotely.
The iLO web interface groups similar tasks for easy navigation and workflow. The interface is organized in a navigational tree view. The top-level branches are Information, iLO Federation, Remote Console, Virtual Media, Power Management, Network, Remote Support, and Administration. In a nutshell, these interfaces provide administrative access to all servers which are under the command of the interface.
More Information About the Attacks Targeting HPE iLO 4
It seems that for now HPE iLO interfaces that have been hit by the ransomware threat are publicly accessible. Over 5,000 iLO-4 have been found to be exposed publicly as Shodan statistics show.
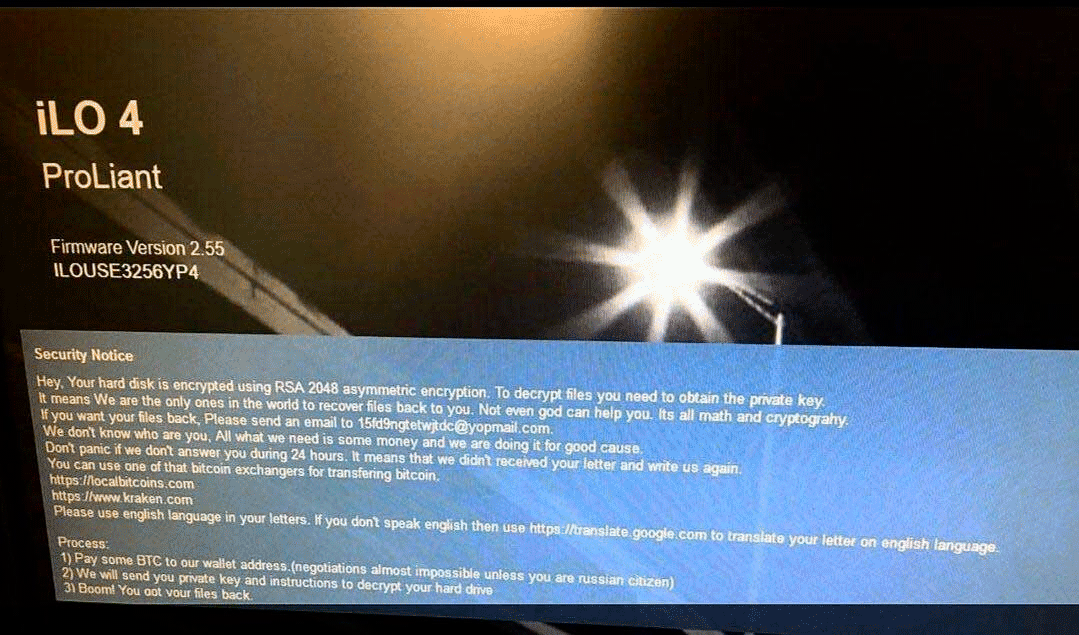
If HPE iLO interface is hit by the ransomware, the security banner will be changed. The altered Login security banner added by attackers states the following:
Security Notice
Hey. Your hard disk is encrypted using RSA 2048 asymmetric encryption. To decrypt files you need to obtain the private key.
It means We are the only ones in the world to recover files back to you. Not even god can help you. Its all math and cryptography .
If you want your files back, Please send an email to 15fd9ngtetwjtdc@yopmail.com.
We don’t know who are you, All what we need is some money and we are doing it for good cause.
Don’t panic if we don’t answer you during 24 hours. It means that we didn’t received your letter and write us again.
You can use of that bitcoin exchangers for transfering bitcoin.
https://localbitcoins.com
https://www.kraken.com
Please use english language in your letters. If you don’t speak english then use https://translate.google.com to translate your letter on english language.Process:
1) Pay some BTC to our wallet address.(negotations almost impossible unless you are a russian citizen)
2) We will send you private key and instructions to decrypt your hard drive
3) Boom! You got your files back.
Here is an image depicting the security banner shared by @M_Shahpasandi on Twitter:

Victims report that the attack indeed encrypts or wipes the hard drives that were targeted. The chronological order of the attack is the following:
- Access is gained to the Integrated Lights-Out interface
- The Security Login Banner has been enabled
- A remote ISO has been mounted
- Scripts or programs are run from the ISO
- The server is rebooted
It is speculated that the attackers used to gain access by either executing the CVE-2013-4786 vulnerability, which allows an offline brute force attack for a password hash of a valid iLO user or via the CVE-2017-12542 vulnerability, which allows an authentication bypass, solved by updating to iLO version 2.53.
Many security researchers advise that HPE iLO 4 or any other similar remote control interface for servers should never be connected to the public Internet. Secure VPNs should be used for access and you should have the latest firmware installed which is available at all times.

