The intensity of malicious attacks that have applied exploit kits (EKs) has increased during the last couple of years. In fact, by having a look at quarter three of 2015, one will notice at once that the exploitation of exploit kits has escalated seemingly. As many researchers have pointed out, the downfall of the infamous Blackhole EK in October 2013 has brought other exploit kits into the light.
Exploit Kits Threat Landscape
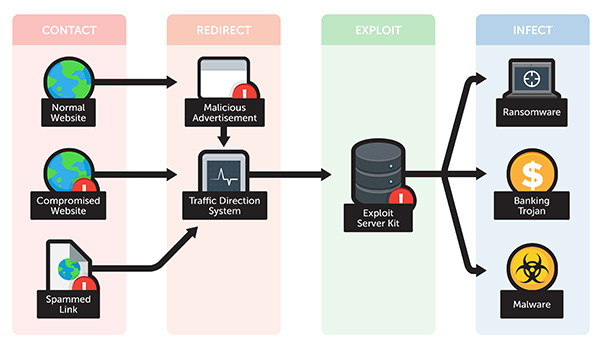
Exploit kits are typically used in malicious operations known as drive-by downloads. Once such a download takes place, the user is redirected to an attacker’s website hosting an EK.
The growth in intensity and effectiveness of EK attacks is due to the successful creation of criminal DNS infrastructure. The latter has jumped to 75% in the last quarter of 2015, in comparison with the third quarter of 2014. The statistics are part of a vast research by Infoblox.
Why should we care? Exploit kits are malware that represents automated attacks and should be of great concern to both security geeks and users. Exploit kits are definitely crafted by cyber criminals with sophisticated skills. They can be described as packages for delivering a particular payload (for instance ransomware) that are up for sale or rent. The way the different types of malicious software are being distributed on underground forums (malware-as-a-service) is quite alarming. Practically, any cyber crook, even those with little technical knowledge, can go after individuals, enterprises and public organizations.
Most of the EK activity is traced back to four well-known exploit pieces:
- Angler Exploit Kit;
- Magnitude EK;
- Neutrino EK;
- Nuclear EK.
The four of them have been used in 96% of all exploit kit activity in the last three months of 2015.
Angler Exploit Kit
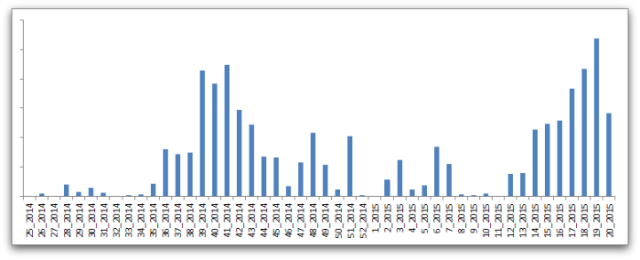
Research indicates that Angler has first appeared on the malware horizon in the end of 2013. Since its first appearance, Angler has grown in popularity and maliciousness. It is considered one of the most aggressive exploit kits in the wild that successfully evades detection and has various components. It’s for sure one of the most prevalent exploit tools out there. For example, researchers at Sophos had reported a large number of Angler-infected landing pages in the spring of 2015.
Here’s a graph that represents Angler’s activity through recent years:
Read more about Angler EK:
Exploit:HTML/Axpergle.N – Angler Exploit Kit Component
Hundreds of GoDaddy Domains Exposed to Angler
Magnitude EK
The magnitude exploit package became famous in October 2013 when it was applied in an attack on visitors to PHP.net. Typically, visitors were redirected to the kit with the help of a compromised JavaScript file. Later, Magnitude made the headlines once again when it became public that it was used in a malvertising attack on Yahoo. The crooks bought ad space on Yahoo and then used the advertisements to link visitors to malicious domains hosting Magnitude. The kit is well-known to exploit vulnerabilities in Java and Flash.
Read More about Magnitude EK:
CryptoWall and Magnitude EK
Neutrino EK
Neutrino was recently reported to attack websites using the the eBay’s Magento commerce platform. Google has blocked thousands of website (more than 8000) that were associated with the Neutrino attack. Researchers warn that users running vulnerable, unpatched versions of Flash can become victims by being infected with Neutrino’s malicious payload. The attack’s payloads are most likely Andromeda and Gamarue malware.
Read More about Neutrino-related malware:
Remove BKDR_KASIDET.FD a.k.a. Backdoor.Neutrino
Nuclear EK
The Nuclear pack is defined as one of the most widely-spread exploit kits out there that first appeared in 2009. The kit is quite effective, being capable of carrying out a number of malicious activities such as Flash, Silverlight, PDF, and Internet Explorer exploits, to dropping payloads of advanced malware and ransomware.
Read More about Nuclear EK:
Crowti Ransomware distributed via EKs
Exploit Kits can bring forth a variety of threats
Because of their many-sided character, EKs are often used as a vehicle to perform zero-day attacks and take advantage of software vulnerabilities. They are also often used in data exfiltration operations. Many businesses have been affected not only by the EKs listed in this article but by many others.
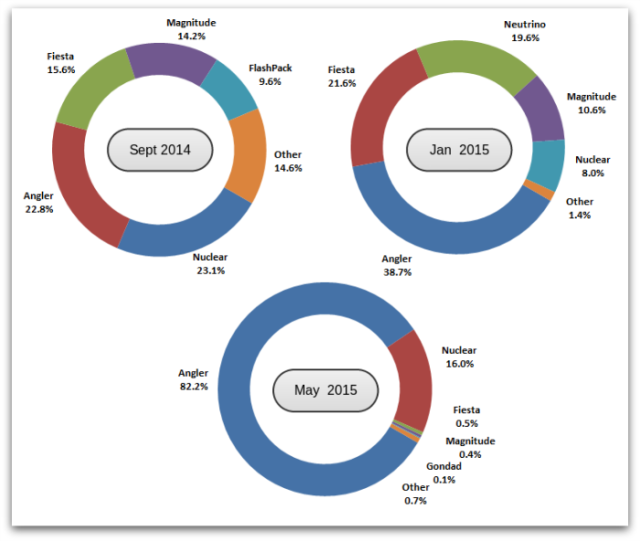
Image Source: Sophos
How to stay protected against Exploit Kits
What everybody should keep in mind is that most EK attacks are initiated via spam email campaigns and compromised websites. They can also be embedded in online ads. Millions of users can become victims of EKs, crimeware and their malicious payloads. The question is how to stay protected against them.
Being protected against exploit attacks definitely requires the right set of tools and knowledge. Regular patching is badly needed, to begin with. Endpoint protection with an integrated patch management is a must for organizations. The good news is that even exploits designed to evade AV detection can be nullified when the targeted systems are thoroughly patched.