According to the FBI, a BEC scam, or a Business Email Compromise scam, is a sophisticated online fraud that targets businesses working with foreign suppliers and regularly performing wire transfer payments. Also known as a Man-in-the-Email scam, BEC has turned into one of the major cyber threats endangering both a business’s finances and online security.
In the period between October 2013 and August 2015, BEC scams have caused US companies losses in the amount of $750 million dollars, leaving more than 7,000 victims in despair. Another report indicates that cybercriminals have gained approximately $50 million dollars from victims worldwide.
What’s the Magnitude of BEC Scams in 2016?
One of the most recent BEC scams has caused quite the havoc overseas, as it lead to an investment fund losing $6 million to such a fraud. The case has literally turned into a battle, as a lawsuit was filed several days ago by Tillage Commodities Fund. The lawsuit alleges that SS&C Technology showed an egregious lack of diligence and care, when they were tricked by an email scam that ultimately led to hackers in China obtaining $5.9 million.
According to Tillage, SS&C not only didn’t comply with their own policies but also assisted the crooks by fixing transfer orders that had failed initially. The documents were posted online for everyone to see.
It’s clear that the case is not only about the theft itself but also about a disintegration of corporate policy and disregard of data and asset security.
SS&C has internal guidelines focused specifically on detecting and protecting against Business Email Compromise scams. Employees are instructed to inspect all email fields (such as To:, CC:, From:) for signs of fraud or spoofing.
SS&C also required four people to sign-off on a transfer requests from the Tillage fund, and asked Tillage to verify disbursements by either appending an invoice to support the expense or in the case of redemption, provide redemption letters and instructions from fund investors, SCMagazine writes.
Had the policies been followed, the BEC could have been prevented, documents show. On March 3, 2016, something went terribly wrong and those didn’t deliver. This is when scammers were targeting Tillage’s bank account and started requesting transfers to the Hong Kong bank account of a “vaguely identified” technology firm. The lawsuit claims that the whole scheme was carried out by inexperienced fraudsters and even spelled the Tillage name wrong. This should have served as a clear indication of fraud attempts. Moreover, the emails contained “awkward syntax and grammatical errors – which were wholly inconsistent with prior Tillage communications – and which were entirely unclear in substance.”
What is worse is that this is definitely not the first BEC scam that has caused millions of dollars in business losses. But it is indeed a case that has drawn the attention of international media and it should serve as a warning.
The Tillage case aside, how exactly is a BEC carried out? How is a BEC scam initiated?
BEC often begins with a fraudster compromising a business executive’s email account. A publicly listed email could also be targeted. To do so, the fraudster would employ a keylogger and phishing tricks. A domain would be created that is strikingly similar to the one of the targeted company. Or a spoofed email would be sent that would push the target into providing account details. Then, the fraudster would try to figure out who initiates wire transfers and who requests them. In many cases, the fraudster would spend lots of hours and research to locate a company that has had a change in leadership in the finance department. Another preferred target would be a company where the executives are traveling a lot.
TrendMicro research illustrates three basic types of BEC scams:
The Bogus Invoice BEC Scam
This BEC type usually involves a business that has an established relationship with a supplier. The fraudster asks to wire funds for invoice payment to an alternate, fraudulent account via spoofed email, telephone, or facsimile.
The Business Executive BEC Scam
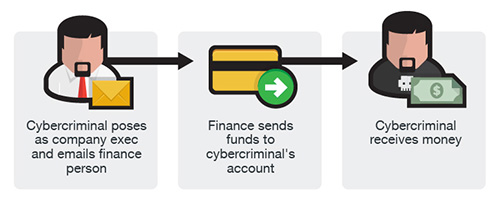
Fraudsters identify themselves as high-level executives (CFO, CEO, CTO, etc.), lawyers, or other types of legal representatives and purport to be handling confidential or time-sensitive matters and initiate a wire transfer to an account they control. In some cases, the fraudulent request for wire transfer is sent directly to the financial institution with instructions to urgently send funds to a bank.
The Multiple Vendor BEC Scam
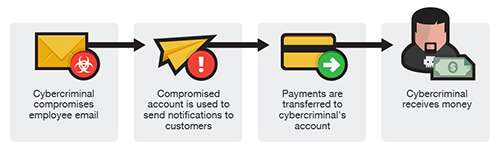
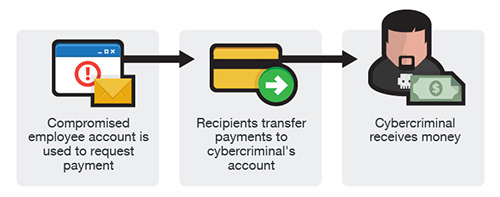
Similar to the two other versions, an email account of an employee is hacked and then used to make requests for invoice payments to fraudster-controlled bank accounts. Messages are sent to multiple vendors identified from the employee’s contact list. The business may not become aware of the scheme until their vendors follow up to check for the status of the invoice payment.
BEC and Ransomware Attacks Growth – Emails Are the Number One Attack Vector
According to multiple cybersecyrity reports, emails have turned into the number one infection vector. That being said, BEC scams and ransomware infections have been a major threat to businesses worldwide.
In recent cases, ransomware infections usually start via email, with many ransomware families choosing spam as the delivery method of their malware. But BEC scams have already proven to be very profitable, as visible by the Tillage case. Both users and businesses are being targeted on multiple levels, draining finances and extorting money.
We have already written plenty of articles on ransomware prevention and protection.
What about BEC Scam Prevention?
In general, security solutions search for malicious documents or known blacklisted URLs to determine whether an email is suspicious. BEC scam emails, however, often lack any signs that would give away malicious intentions. BEC scams mostly rely on social engineering and exploit employees’ weaknesses, and are highly targeted. However, the fact that BEC and phishing share some similarities gives users (and employees) the chance to monitor for particular signs in the contents of such emails, as pointed out by Proofpoint researchers:
- High-level executives asking for unusual information;
- Requests to not communicate with others,
- Requests that bypass normal channels;
- Language issues and unusual date formats;
- “Reply To” addresses that do not match sender addresses;
Also, besides educating their employees (CEOs included!), companies should look into email protection services and apps provided by security vendors. Email protection is “the now” of online security.b