Instead of being stopped, a powerful kit of different types of malware, primarily Trojan horses still continues to infect Android users on a daily basis. Reports by TrendLabs at Trend Micro indicate that some apps have even managed to generate around 500 000 downloads. This massive spreading of malicious apps had raised some concerns since they continue to spread with a rate similar to the rate back in spring 2016 when the DressCode malware was initially detected. Researchers also report that there are several types of threats that are very real when DressCode is involved.
Instead of being stopped, a powerful kit of different types of malware, primarily Trojan horses still continues to infect Android users on a daily basis. Reports by TrendLabs at Trend Micro indicate that some apps have even managed to generate around 500 000 downloads. This massive spreading of malicious apps had raised some concerns since they continue to spread with a rate similar to the rate back in spring 2016 when the DressCode malware was initially detected. Researchers also report that there are several types of threats that are very real when DressCode is involved.

How Does a DressCode Infection Process Work
Initially, the Trojan replicates via a malicious app pretending to be a legitimate one. To generate a higher download rate, the cyber-criminals have chosen a very specific strategy – they either resemble applications as if they were legitimate widely download app additions, like a mod for Pokemon Go or Minecraft add-on. This makes those apps more desirable and increases the chance of victims becoming infected.
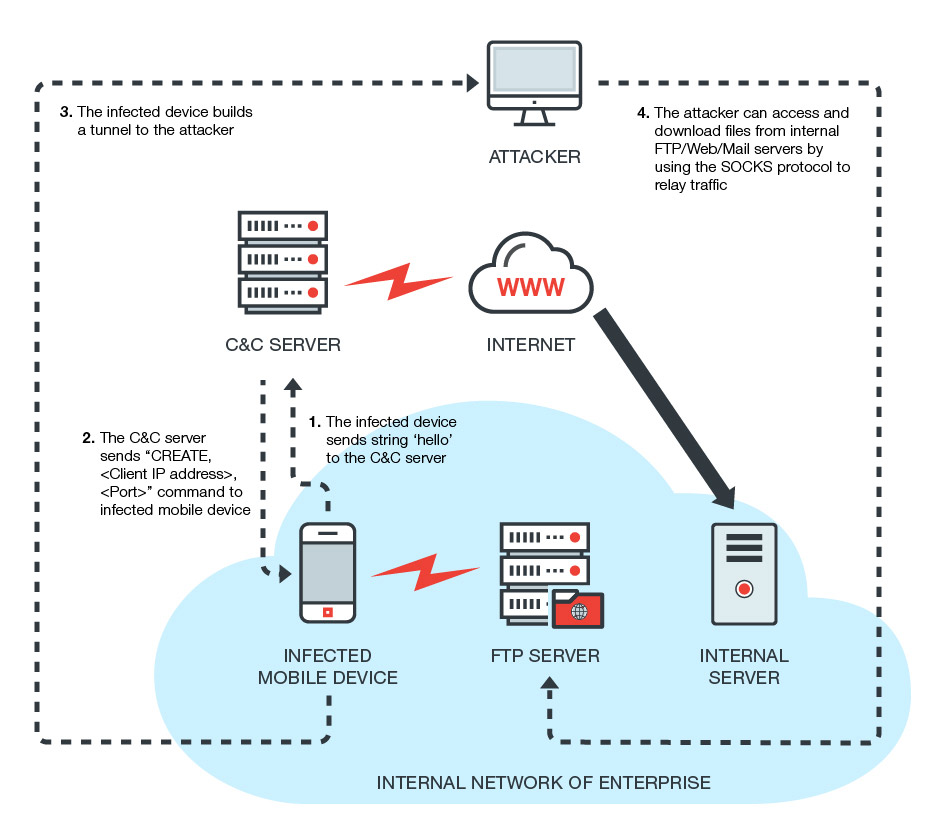
Once such suspicious applications are set up on an Android device, the virus connects to the command and control server which is currently a remote host in the cloud. After being connected and identified in the server, the server sends requests to open unsecured port and hence create a connection based on the TCP protocol.
Once already compromised the device can be used in different ways.
Trend Micro malware researchers have managed to research the virus’s connection in details only to establish a mind map of how exactly it communicates from the attacker to the infected device.
In their research, the investigators have established that the virus can take advantage of the connection the compromised device has established with the sole purpose to skip the device and focus on the connection with internal servers only to steal crucial information, using the device as an intermediary for MiTM attack. With the latest trend of BYOD or bringing your device to a business environments, this virus may cause quite the issues for organizations.
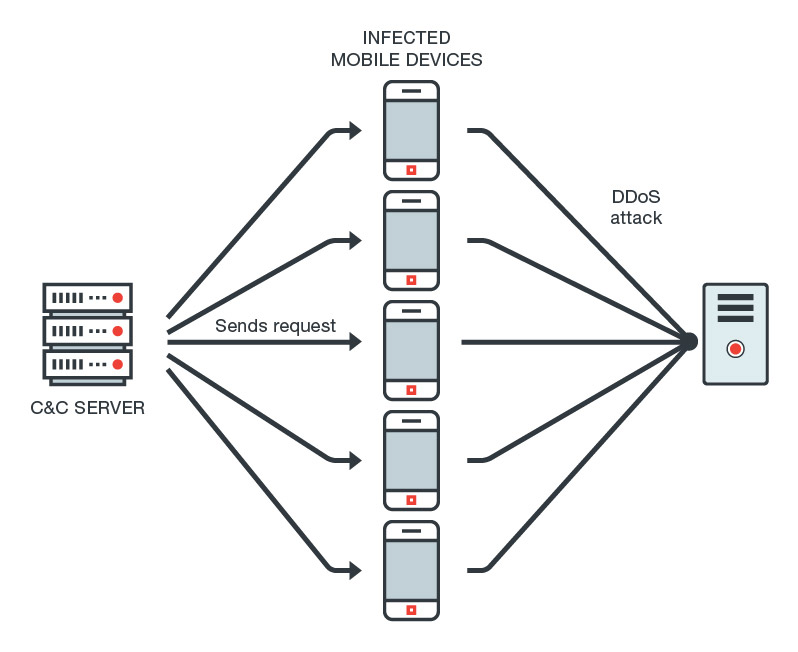
One possible scenario is that DressCode malware situates a SOCKS protocol proxy on devices it has already compromised. If the malware has infected one device, this is not an issue, however, the virus may have a botnet of devices via this protocol and this is a real threat to any organization running a network. One usage of such botnets could be to cause a malicious DDoS attack to a targeted server, rendering it temporarily useless.
Besides those real world consequences, the malware may also install clicker malware that can automatically connect devices to various third-party hosts and URLs that are part of a pay-per-click and other affiliate schemes, automatically generating revenue for the attacker by driving hoax traffic via the infected devices.
Another real scenario is if a device that has already been infected to be used to infect more devices using a worm-like infection strategy. This is particularly dangerous because all it requires is for two devices to be interconnected in a way and one of them to be infected. To put this in perspective, imagine that there is a mobile device of a senior executive in which there is secret company information. An infected device can potentially take advantage and hack the executive device, allowing hackers to upload data to their servers via the infected device. This also applies to all types of devices, not just smartphones, but security computers, routers, wireless cameras, and others. And if a building is “smart” and interconnected, the hackers may even gain access to crucial elements inside the building such as elevators, automatic doors, and RFID or code secured doors.

Summary and Protecting Yourself
DressCode is not a new threat, and it has been around for quite some time now. Bear in mind that there are multiple types of threats spreading in the Google Play store that can perform rooting of your device and many other activities, including infecting the whole botnet of devices with mobile ransomware simultaneously.
This is why to protect yourself from mobile threats you do not just need some software. It is almost imperative to have a solution consisting of a set of activities and tools to increase your protection because usually, the human factor is one of the most crucial reasons for infections.
We have suggested some tips to protect your device that you can combine below:
- Use an Android mobile app protection software that also tracks privacy violation of every app.
- Update your device as soon as updates are available.
- Do not use unsecured Wi-Fi networks and always prefer LTE connections.