A new Android miner called “HiddenMiner” has been discovered by security researchers. It is a dangerous malware that has the potential to cause imminent device failure.
Discovery of the HiddenMiner Android Miner
A team of security experts uncovered a dangerous Android-based malware called HiddenMiner. As derived from its name it is a dangerous cryptocurrency miner that takes advantage of the available system resources to perform complex calculations and generate income for the criminal operators. What is distinct to it is the fact that it contains advanced infection algorithms that can bypass some of the security measures that the Android platform provides.
It is delivered mainly through payloads. The hackers use the well-known strategy of creating malware apps that are spread on the Google Play repository. The hackers tend to create applications with false developer credentials and user reviews that appear as useful applications. Usually such software is also uploaded to various hacker sites, P2P networks (like BitTorrent) and third-party repositories. At the moment some of the main targets are India and China.
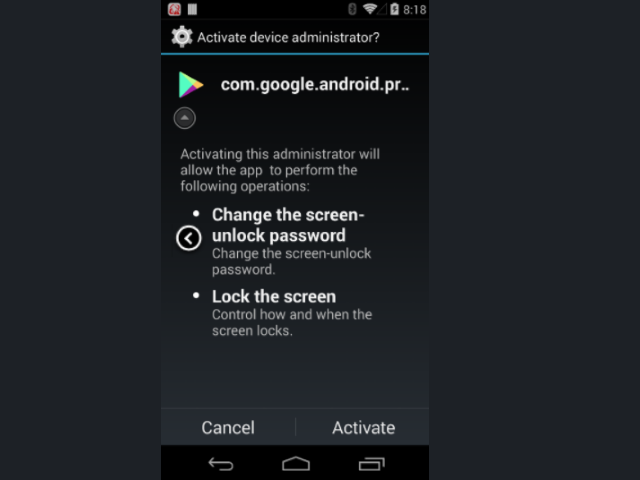
The acquired malware samples were seen as posing as the legitimate Google Play update app having the name com.google.android.provider along with the relevant icon. Once the application is installed on the victim Android device it will persistently ask the users to activate it as a “device administrator” which grants it a lot of permissions. The notification asks for the following permissions:
- Change the screen unlock-password — Change the screen-unlock password.
- Lock the screen — Control how and when the screen locks.
HiddenMiner Android Miner Technical Details
Once the malware has been installed onto the victim devices it starts the built-in Monero miner. The HiddenMiner uses the available CPU power and memory resources to constantly “mine” the Monero cryptocurrency. It is one of the most popular alternatives to Bitcoin and its miners can be obtained in various forms — software, mobile apps and web scripts. The fact that the miner is integrated deeply into the app and provides no control of the dangerous instance. As a result the devices can overheat and cause the devices to fail.
What’s more interesting is the fact that the HiddenMiner malware uses several techniques to hide itself from the Android system and the relevant security software. One of the ways is to empty the app label and uses a transparent icon after installation. Once the device has been given the relevant permissions it will hide the app from the launcher by modifying the Android launcher display settings.
In addition, it has built-in stealth protection capabilities which can bypass any installed security software. The virus engine scans for signatures belonging to anti-virus programs, emulators, virtual machine hosts or sandbox environments. Once it has infiltrated the system it can no longer be uninstalled as the hackers have used a technique that locks the device’s screen if the users want to deactivate its privileges. This is an exploit found with Android 7.0 (Nougat) and later versions.