
Account takeover (ATO) continues to be a “ubiquitous problem”, at the heart of which are compromised user credentials. According to a detailed paper by Digital Shadows Photon Research, currently approximately 15 billion credentials are circulating on hacker forums, enabling account takeover, identity theft, and other types of attacks.
“The average person uses some 191 services that require them to enter passwords or other credentials,” researchers say. This presents a huge problem in case of any account compromise, especially if the individual uses the same credentials across multiple services.
To examine the risks of compromised accounts, the research team examined the approaches to account takeovers. The report is based on data taken from the database of Digital Shadows SearchLightTM service, which maintains a database of breached credentials and thoroughly searches criminal forums for attackers’ trends, data dumps, advertisements and tools.
Related Story: 25 Malicious Android Apps in Play Store Were Stealing Facebook Logins
Account Takeover and User Credentials. Some Statistics
Security researchers have observed more than 15 billion user credentials for sale on underground forums. These credentials originate from more than 100,000 data breached. At least 5 billion of them are unique.
Where do these account details come from?
Some of them are login pairs from various services such as social media, streaming, VPN. File sharing, video games, and adult. These appear to be the cheapest for sale, with a price of $15.43, and are quickly being distributed.
One in four advertisements on hacker forums offers accounts related to banking and financial services. However, these are more expensive – $70.91 for each login pair. This price can be much higher in case of a confirmed balance for an online banking account and availability of PII. In such a case, the price can be up to $500.
Banking credentials are favored among cybercriminals:
Many credential harvesters target banking credentials, in large volumes―they can be highly lucrative and are in high demand on underground marketplace sites. Credential harvesters use a combination of techniques to acquire victim’s details, including man-in-the-browser attacks, which use code injection techniques to inject form fields into the user’s banking website. These fields intercept the victim’s credentials directly from their online banking portal. They’re sent to the attackers, who monetize them directly (via fraudulent transactions) or, more commonly, sell them to other threat actors seeking freshly stolen credentials.
The most valuable credentials, however, are related to privileged accounts, according to Digital Shadow’s report:
Privileged accounts, like administrator accounts, are considered extremely valuable in the criminal underworld. Not only do they give access to a network, but they feature the highest levels of control and trust, and their permissions are nigh unlimited. A person using a privileged account could change system configuration settings, read and modify sensitive data, or give other users access to critical assets.
Account Listings
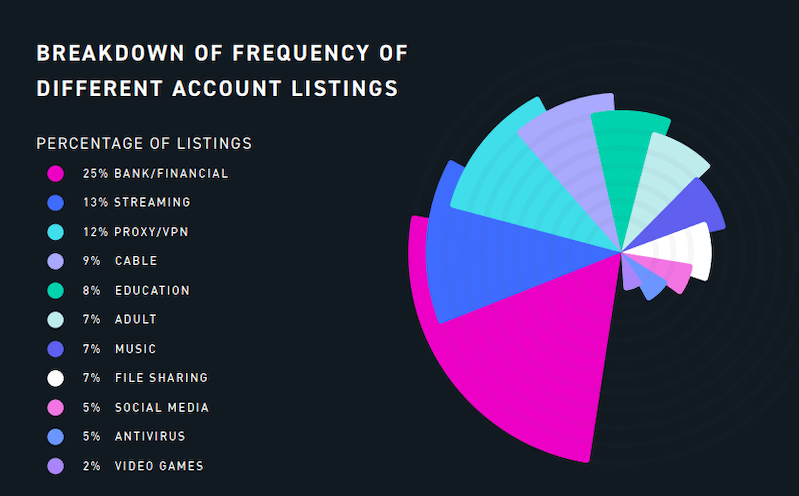
Image Source: Digital Shadows
It should be noted that many of the categories are for services that can be quite expensive if purchased legitimately. In addition, accounts for adult websites offer more benefits, since buyers may not want their real names or financial information associated with these services, the report notes.
Underground Markets for Stolen Credentials
Renting account access is indeed a service. The researchers have been following the emergence and rise of certain markets offering this service. A great example is the so-called Genesis Market, first identified in April 2018.
What is noteworthy is that such markets use their own injects and botnets for harvesting credentials. However, instead of buying a credential, you can rent an identity for a specific period, and this can be done for less than $10. This price would depend of the type of access you are demanding.
This market is also interested in collecting browser fingerprint data, including cookies, IP addresses, and time zones. These details actually make it easier to carry out account takeovers and transactions without being noticed.


