Remember the Astaroth Trojan? Considered to be one of the stealthiest pieces of info-stealing malware, Astaroth continues to evolve in its latest attacks.
According to a new report released by Cisco Talos, the malware has obtained two major updates.
This is bad news, as the Astaroth Trojan is already capable of anti-analysis and anti-sandbox to prevent detection and analysis by cybersecurity researchers.
Astaroth has been known to target Brazilian users, and apparently, it continues to do so in the latest detected attacks. The Trojan has been using the COVID-19 pandemic as a lure. The new additions to its malicious code include:
- Complex maze of obfuscation and anti-analysis/evasion techniques implemented by Astaroth inhibit both detection and analysis of the malware family.
- Creative use of YouTube channel descriptions for encoded and encrypted command and control communications (C2) implemented by Astaroth.
How are the new Astaroth attacks carried out?
The Trojan’s distribution is based on sending out malicious email messages (phishing). The latest campaigns are using the coronavirus (COVID-19) pandemic as a trick to lure users into opening the email message. Since the malware is targeting Brazilian users, the emails are written in Portuguese.
Here’s an example of such an email:
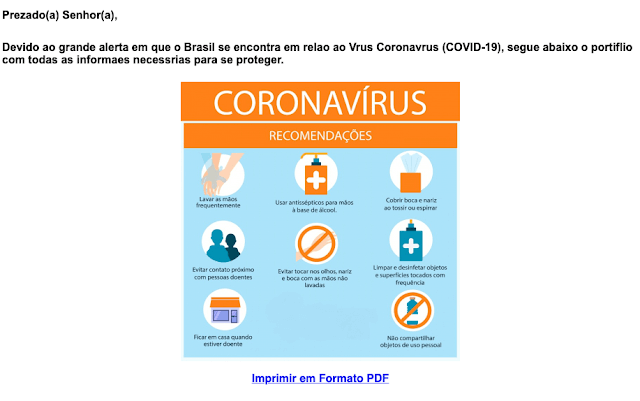
What does the email say? The announcement is about distribution of respirators needed to treat coronavirus patients. The email also includes a series of recommendations in the form of a linked PDF file. Of course, these links are only there to redirect potential victims to hacker-controlled servers.
Once the user clicks on the malicious link included in the email, they will be redirected to a server controlled by the threat actors. The initial payload of the operation is a ZIP file with LNK link from Google infrastructure, reveals Cisco Talos analysis.
Other details of the latest Astaroth campaign include:
- Multiple tiers of obfuscation implemented before LoLBins (ExtExport/Bitsadmin) used to further infection.
- Extensive anti-analysis/evasion checks done before Astaroth payload delivered.
- Encoded and encrypted C2 domains pulled from YouTube channel descriptions.
Astaroth Uses YouTube Channel Descriptions
As already noted, one of the more interesting additions to the latest Astaroth campaign is the use of YouTube channel descriptions. This trick is part of “a redundant C2 mechanism with both primary and secondary C2 infrastructure”:
The primary way that the malware communicates with C2 servers is through the retrieval of C2 domains using Youtube channel descriptions. The attackers have established a series of YouTube channels and are leveraging the channel descriptions to establish and communicate a list of C2 domains the nodes in the botnet should communicate with to obtain additional instructions and updates.
In conclusion…
By design, Astaroth is “painful to analyze,” Cisco Talos says. The malware is getting more sophisticated, adding services such as YouTube to hide its command and control infrastructure.