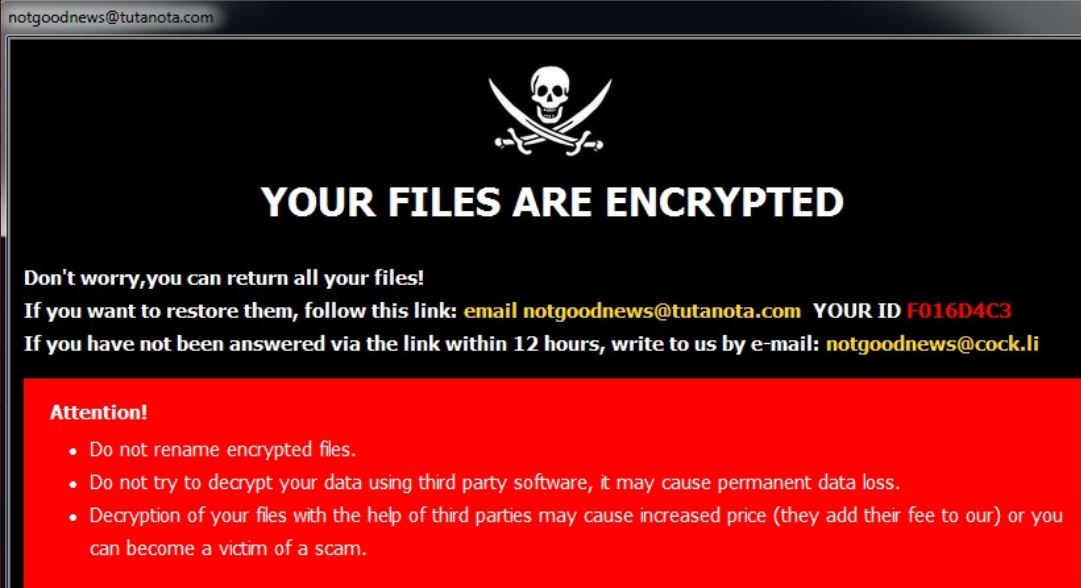
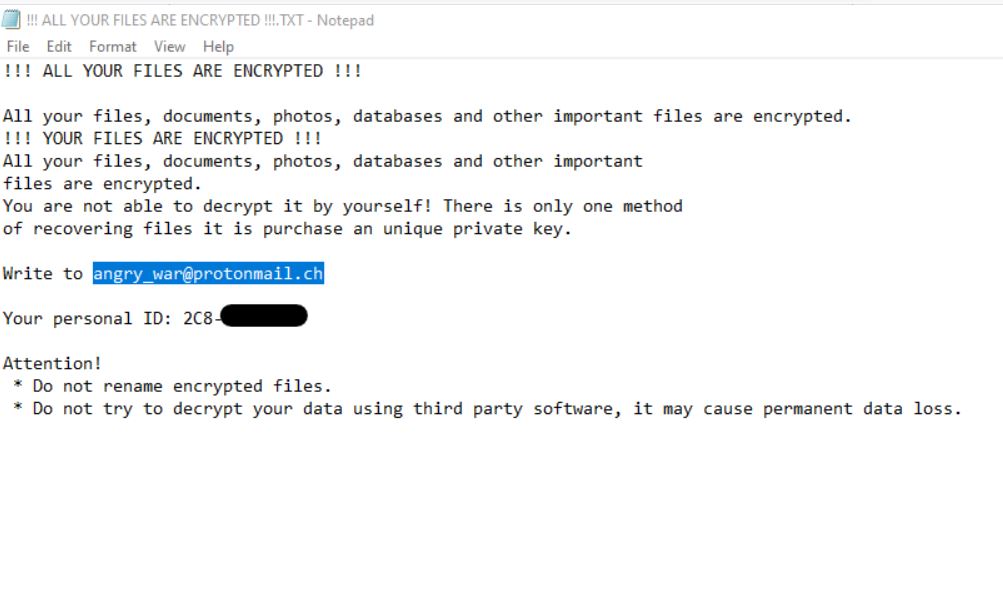
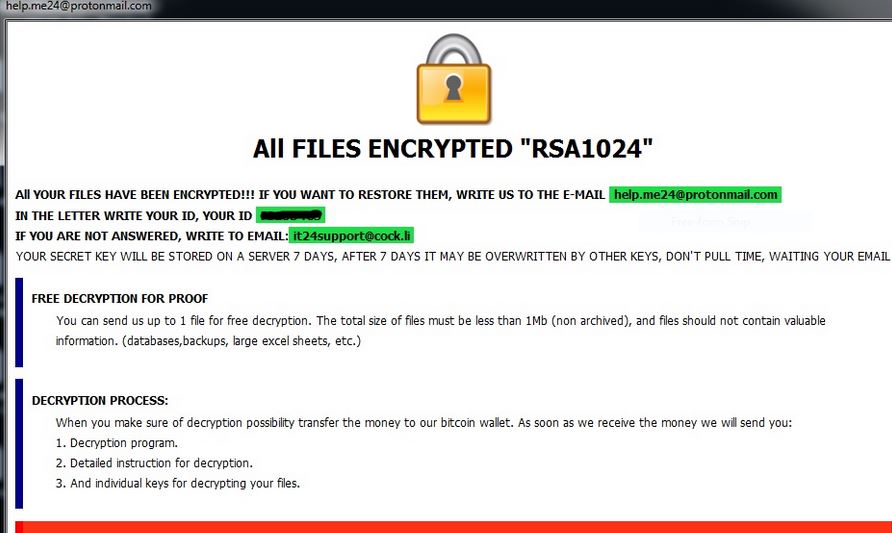
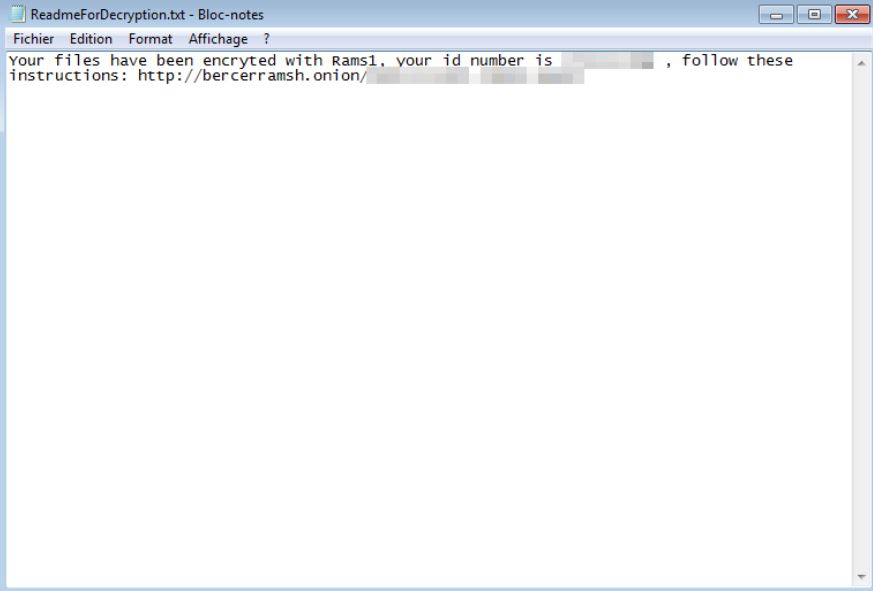
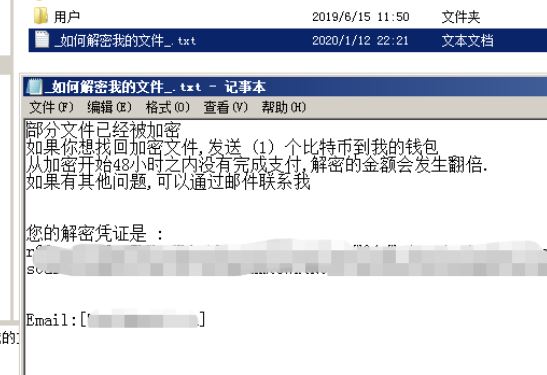
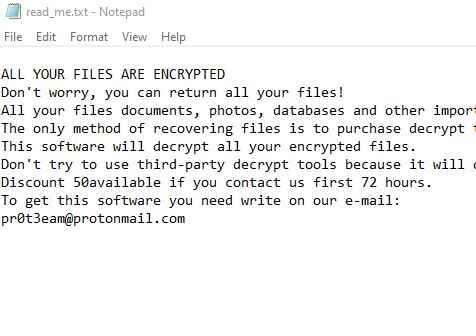
Remove Jhone Trojan From Your PC
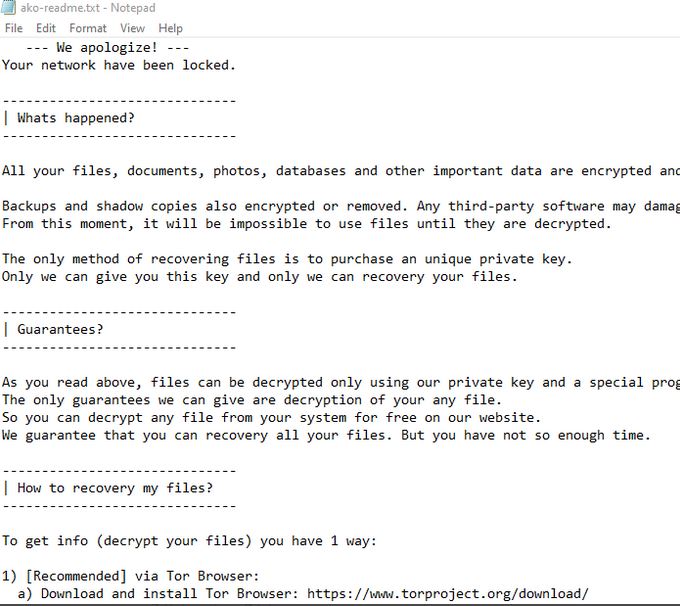
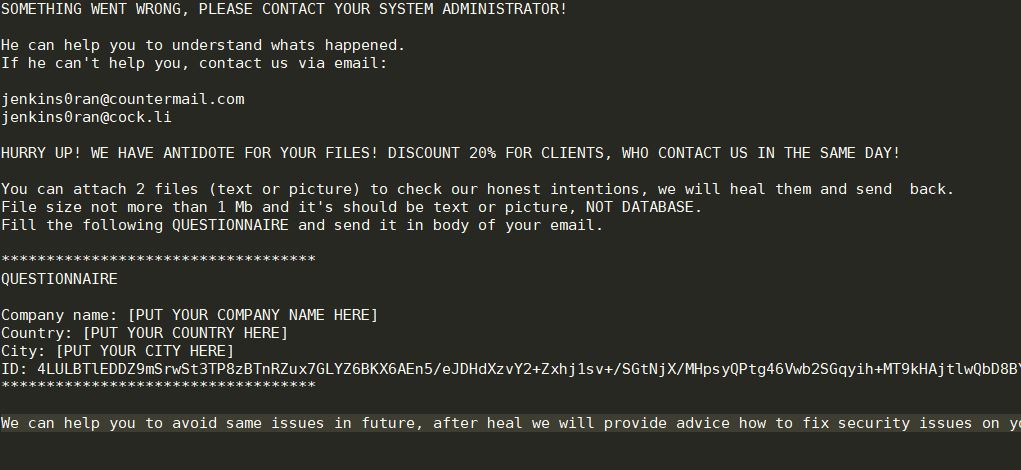
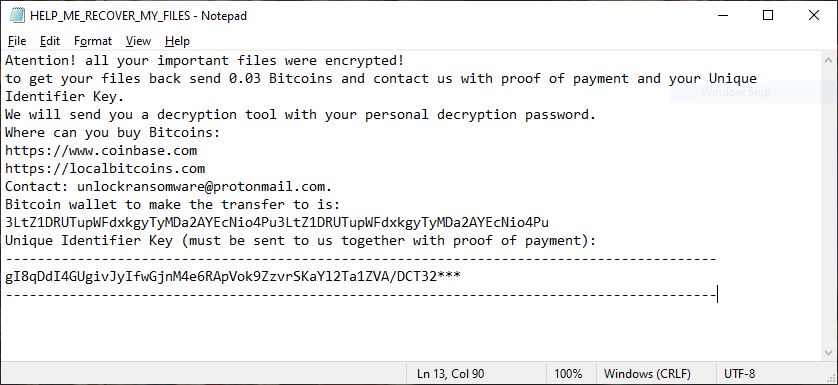
What is Jhone? How to remove Jhone Trojan from your PC or Mac? The Jhone Trojan is a dangerous Trojan that takes advantage of multiple cloud infrastructure to operate. It is being launched in a targeted attack campaign against targets…