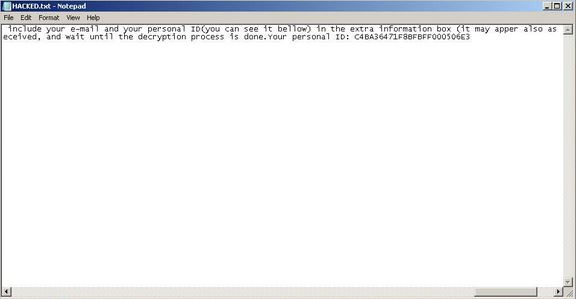
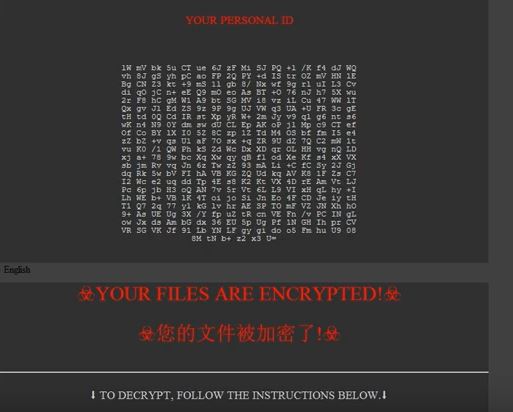
Windows Update Abused To Deliver The Stealth Falcon Malware
The Windows Update mechanisms through the Windows Background Intelligent Transfer Service (BITS) has been found to deliver the dangerous Stealth Falcon malware. This is the default any of applying updates to the Microsoft Windows operating system. A complex strategy is…