ZipperDown Vulnerability Affects About 10% of iOS Apps
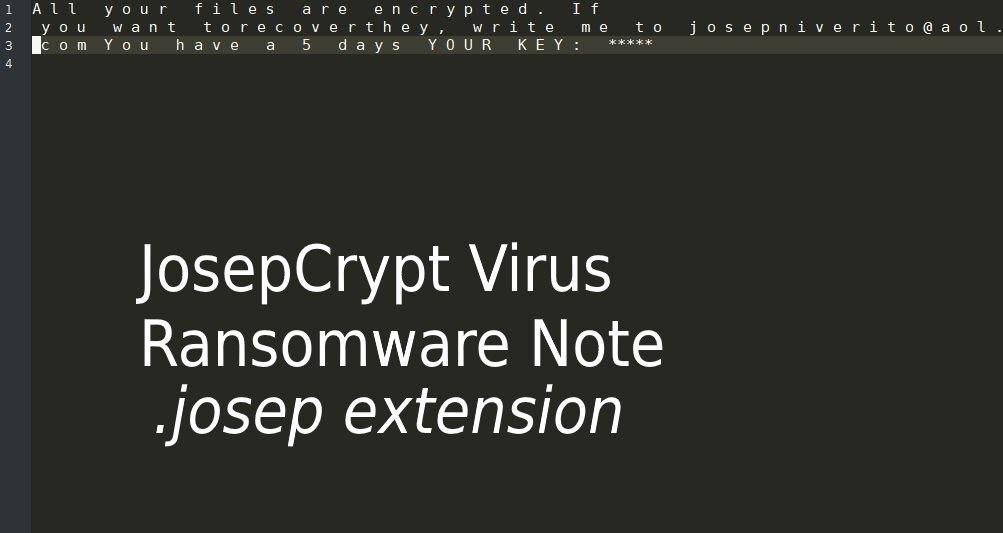
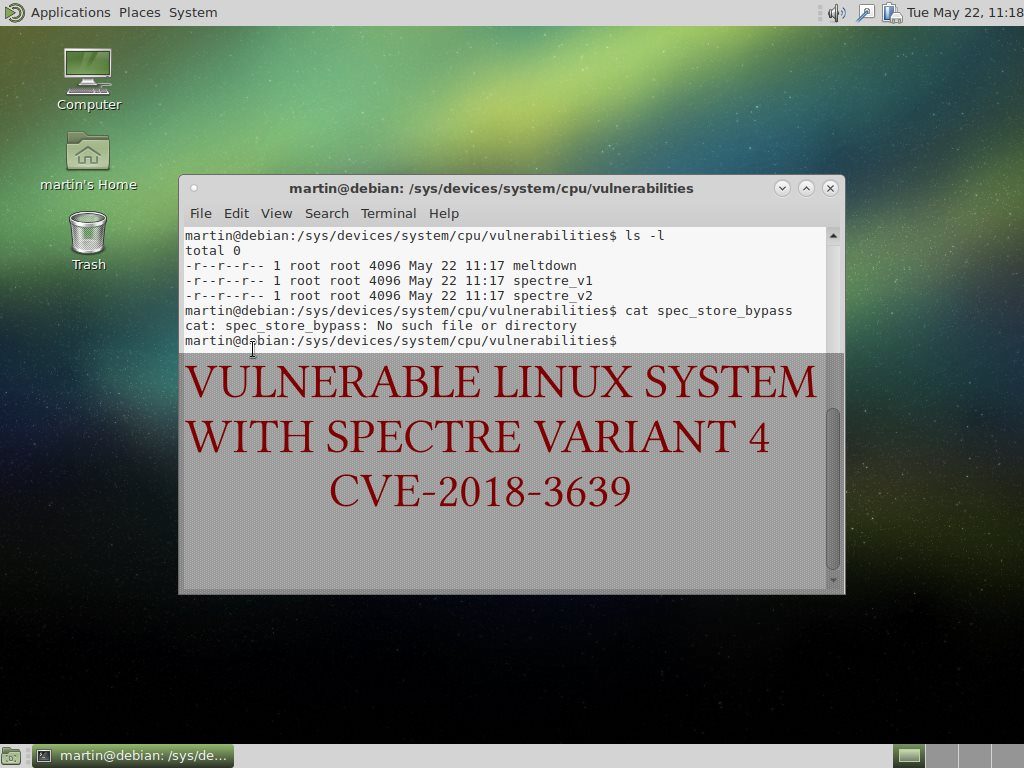
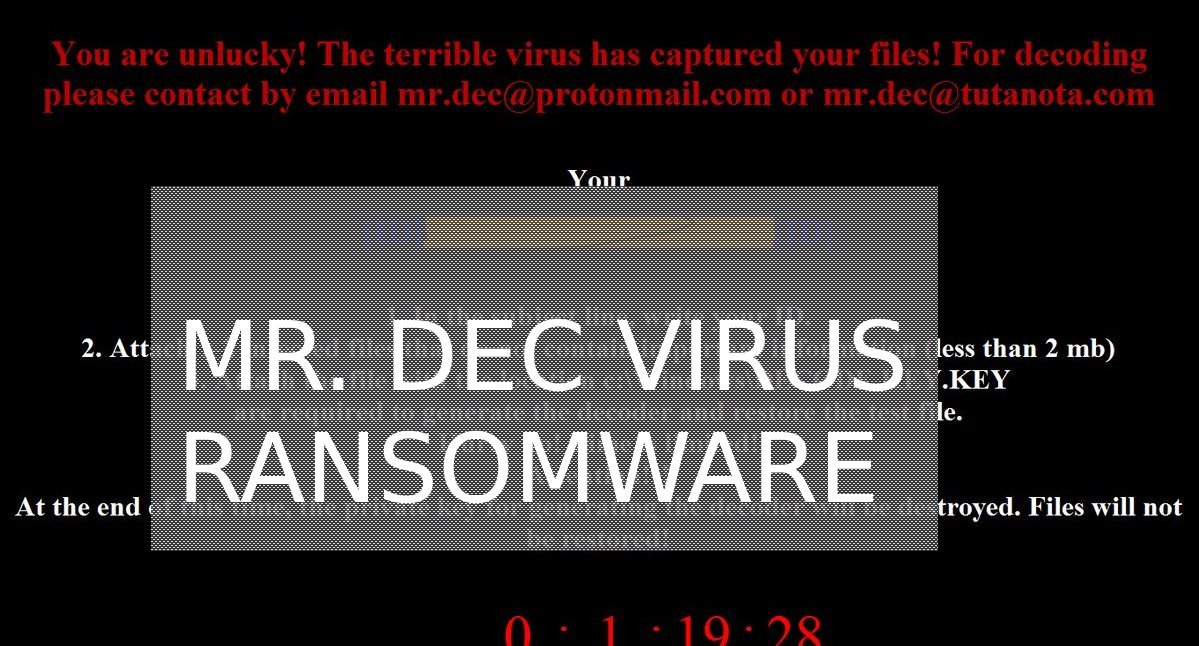
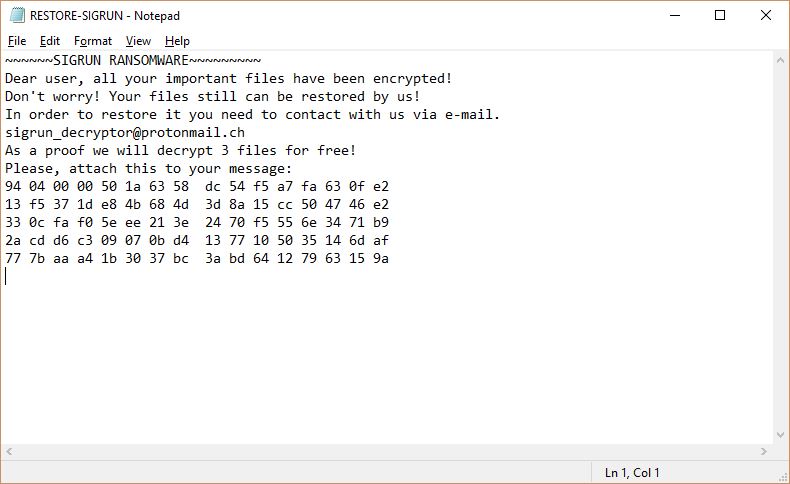
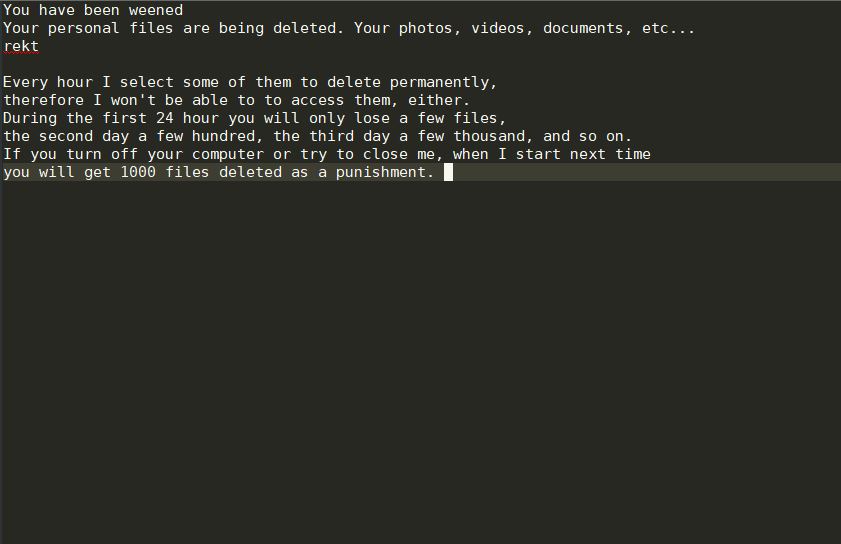
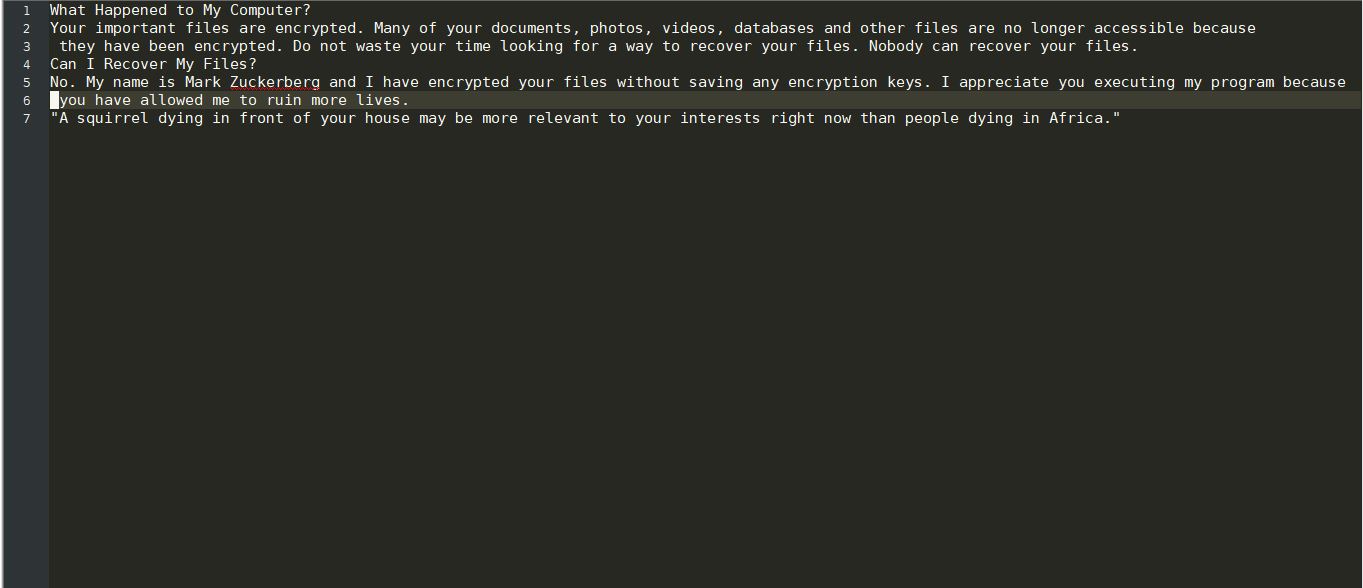
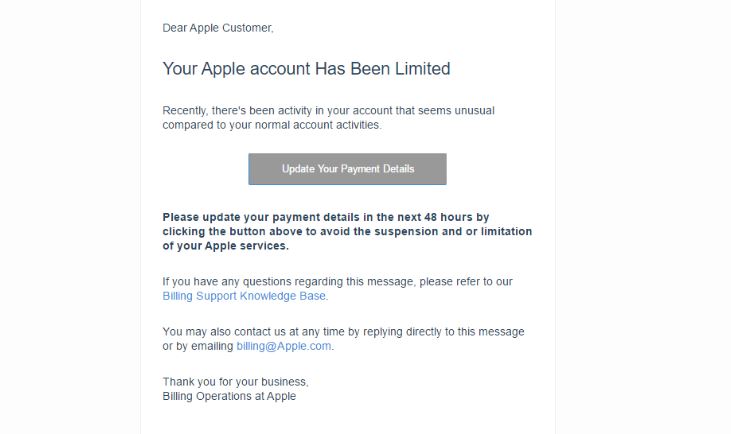
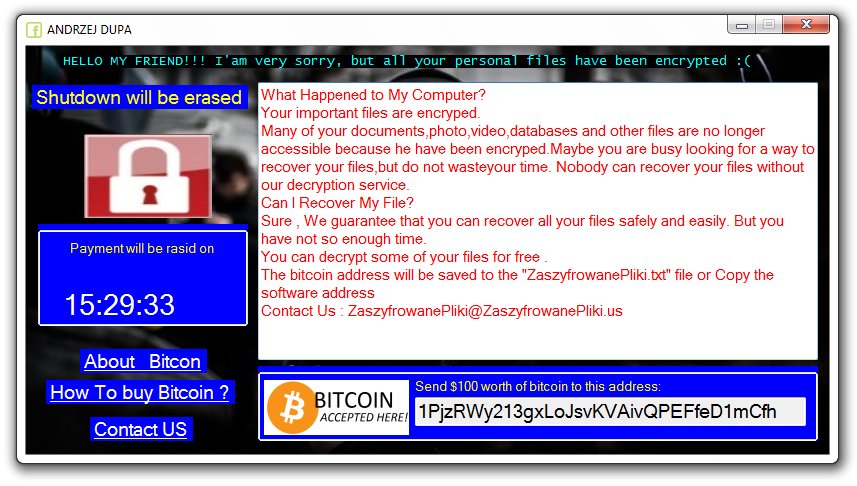
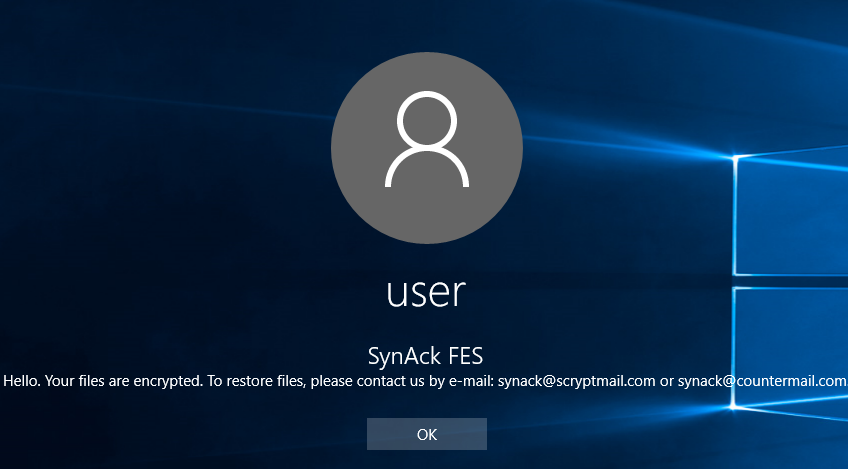
Security experts discovered a dangerous bug that affects applications built for Apple’s mobile software infrastructure. According to the published information the ZipperDown vulnerability affects around 10% of all iOS apps released publicly. It is possible that this bug can function…