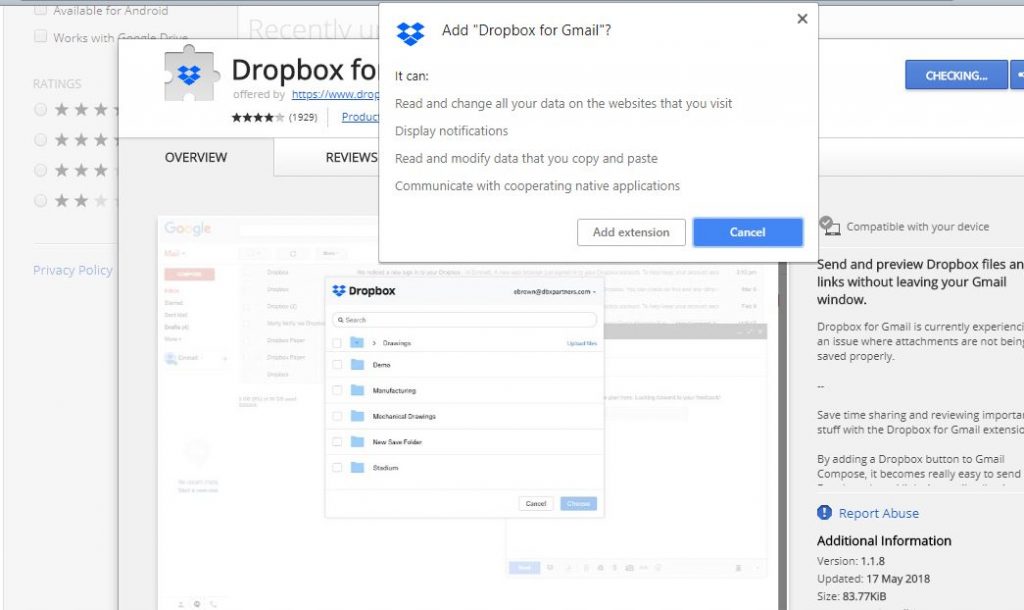
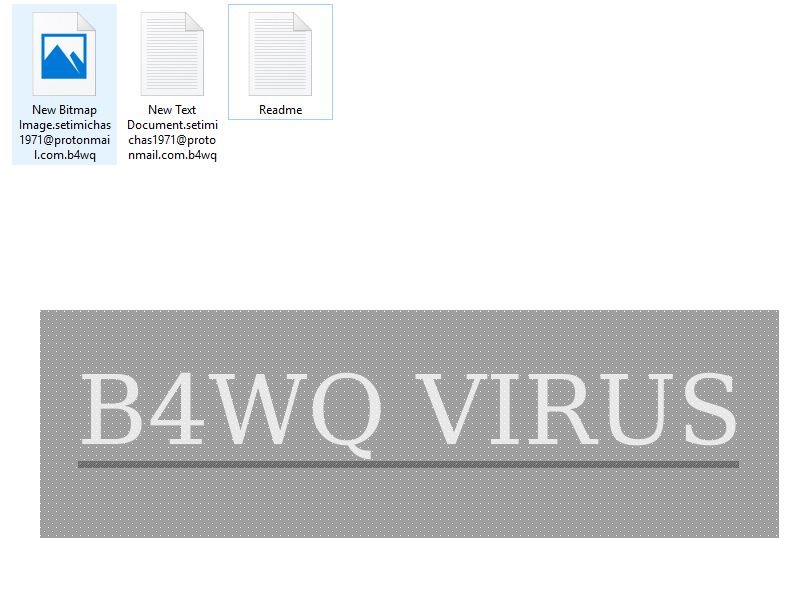
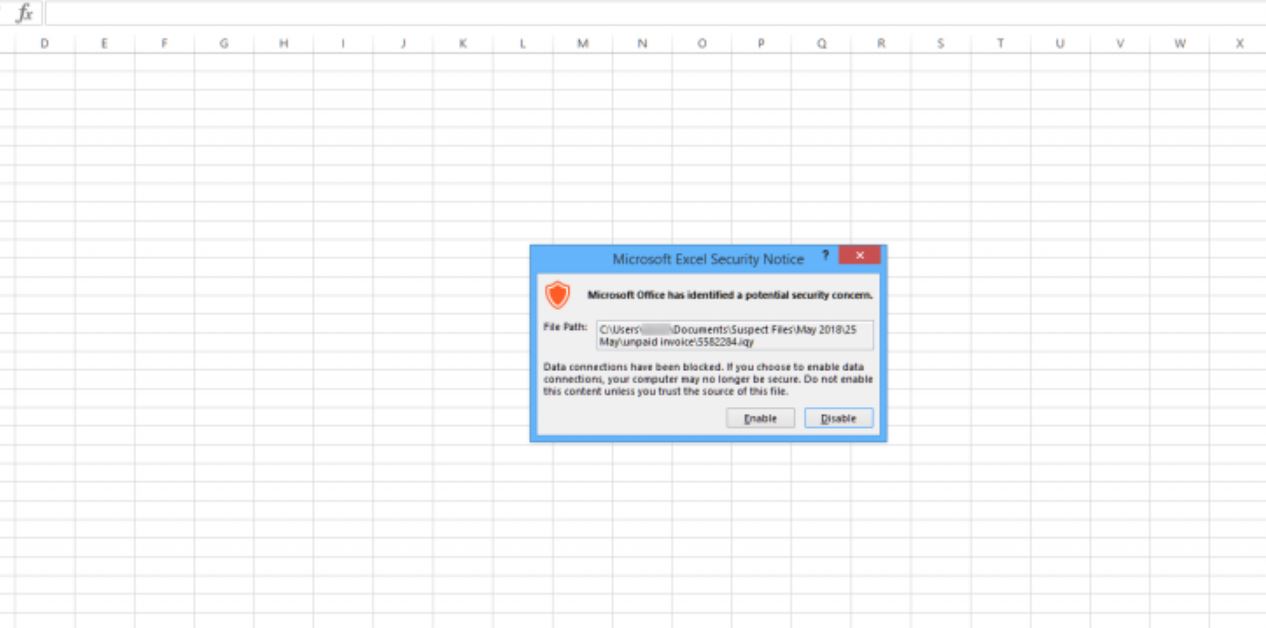
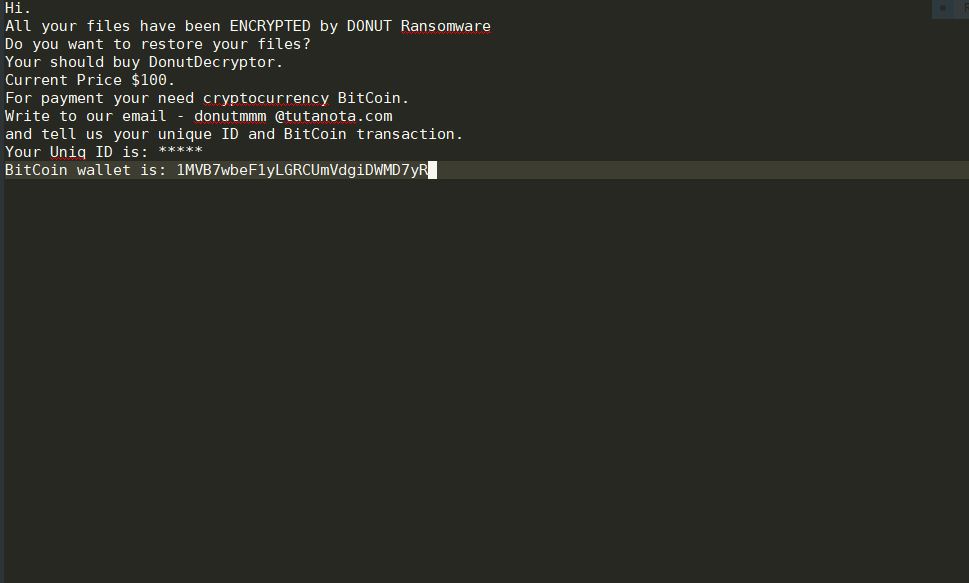
Reports Indicate Growth of DNS Amplification Attacks In Q1 2018
A security report reveals that the number of DNS Amplification attacks done in the first quarter (Q1) of 2018 have doubled. By definition they are a type of DDOS (Distributed denial of service) attacks which are among the most common…