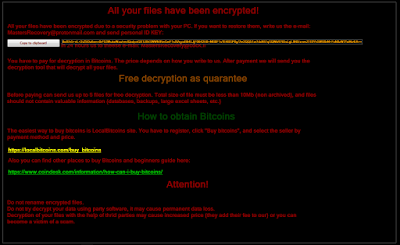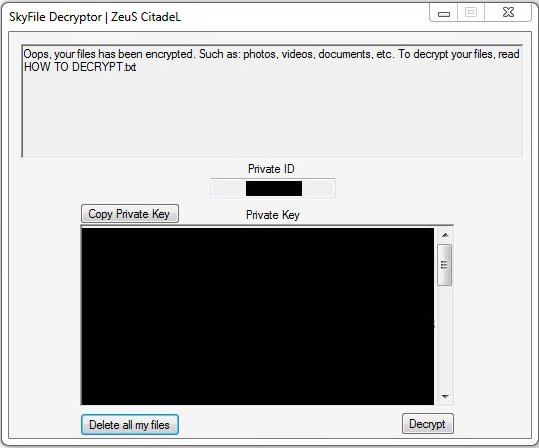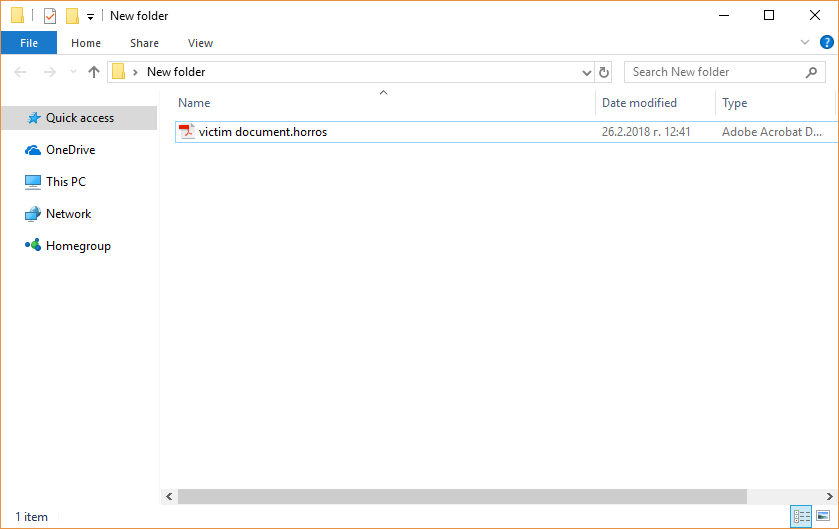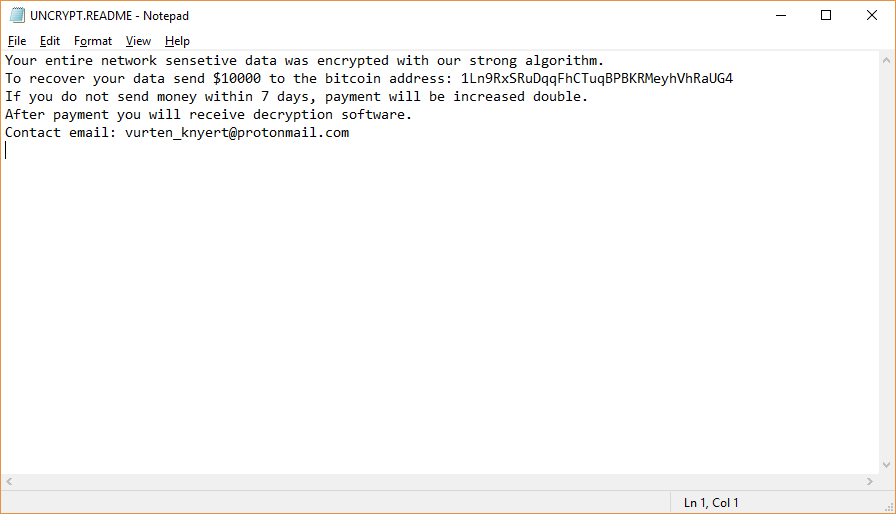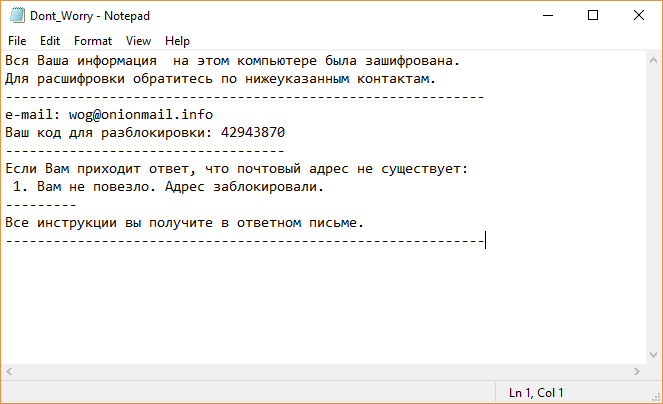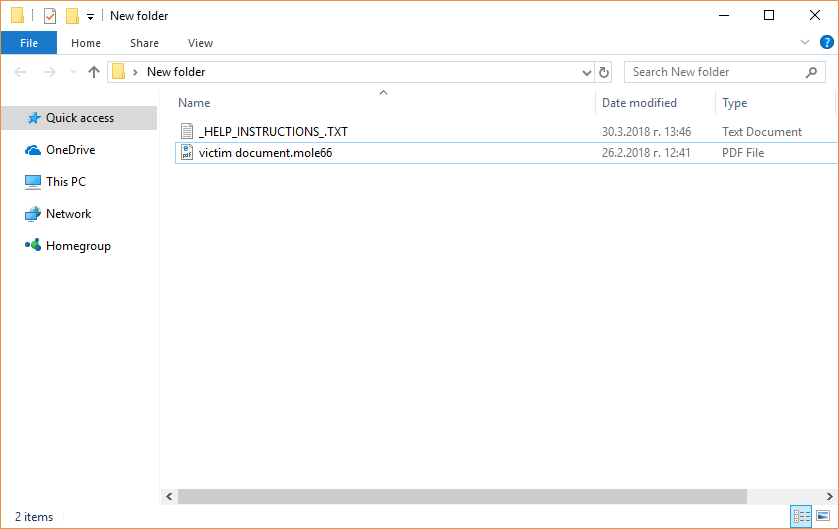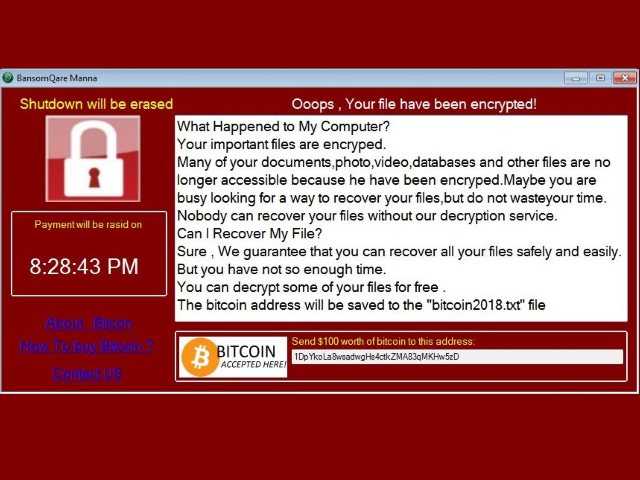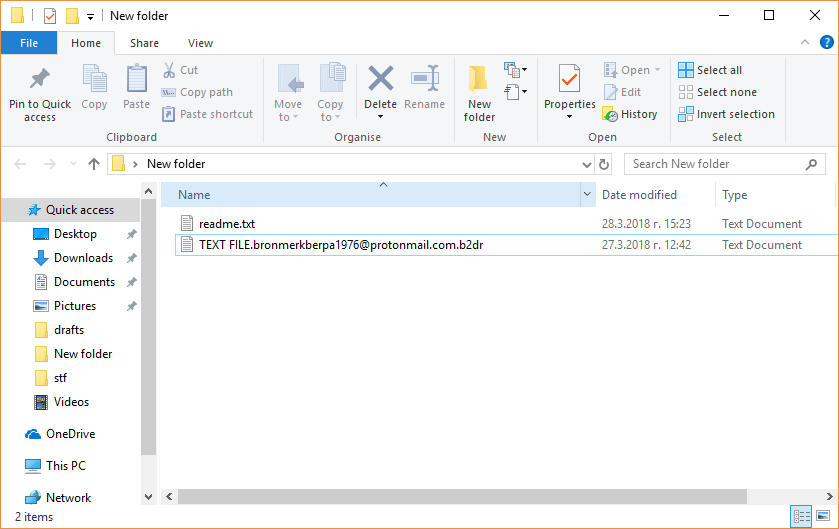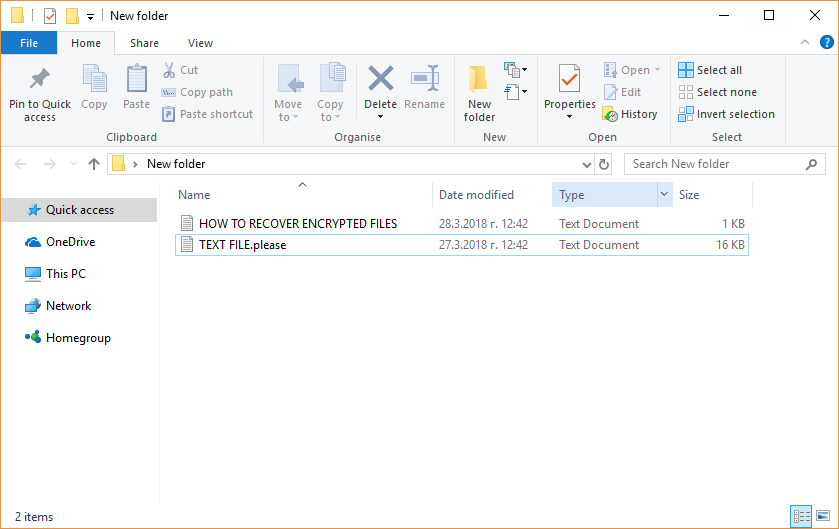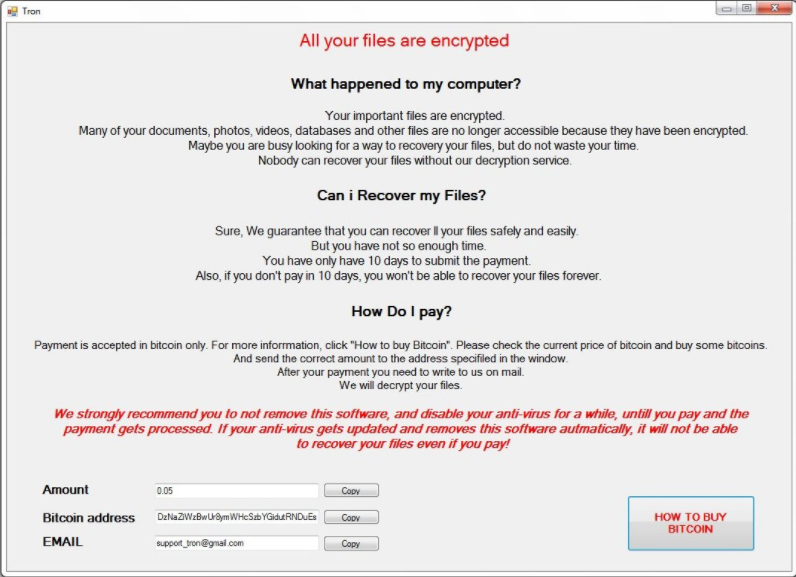
.Tron Virus (Tron Ransomware) – Remove + Restore Files
Tron Virus is a newly discovered malware instance that appears to be made by an unknown hacker or criminal group. The security researchers propose that future attacks might implement newer versions of the malware engine. Tron virus – Infection Spread…