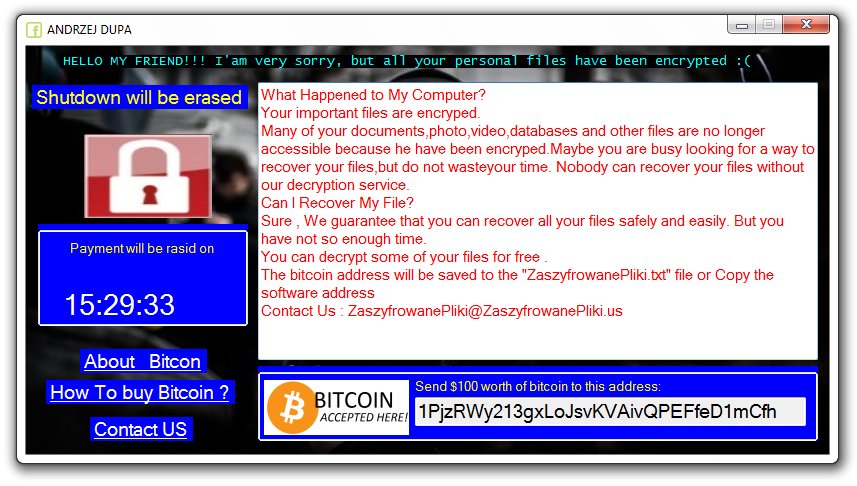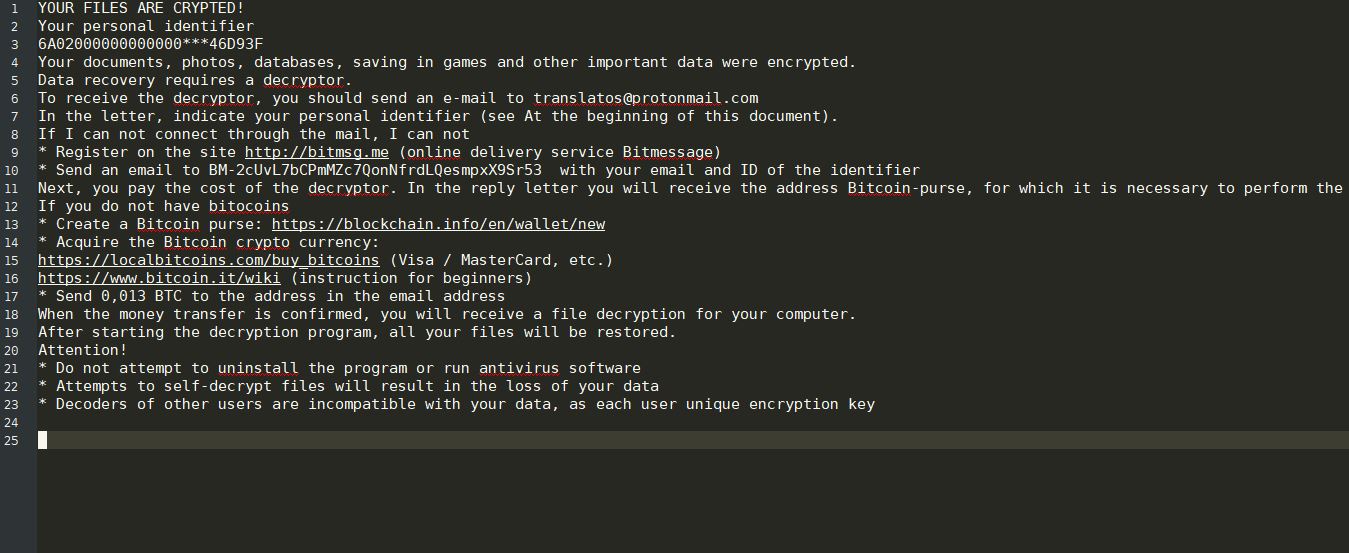
Scarab-Osk Virus (Scarab Ransomware) – Remove and Restore .osk Files
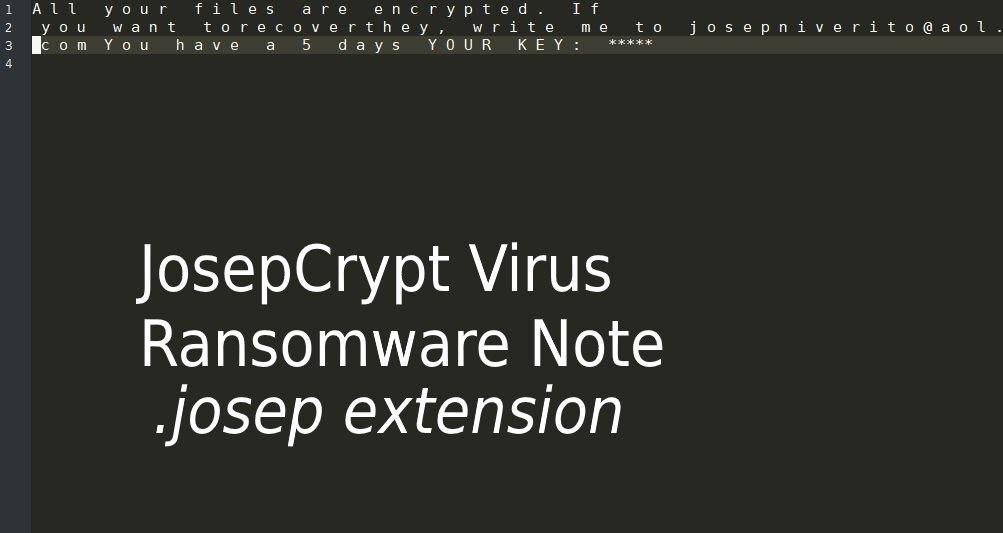
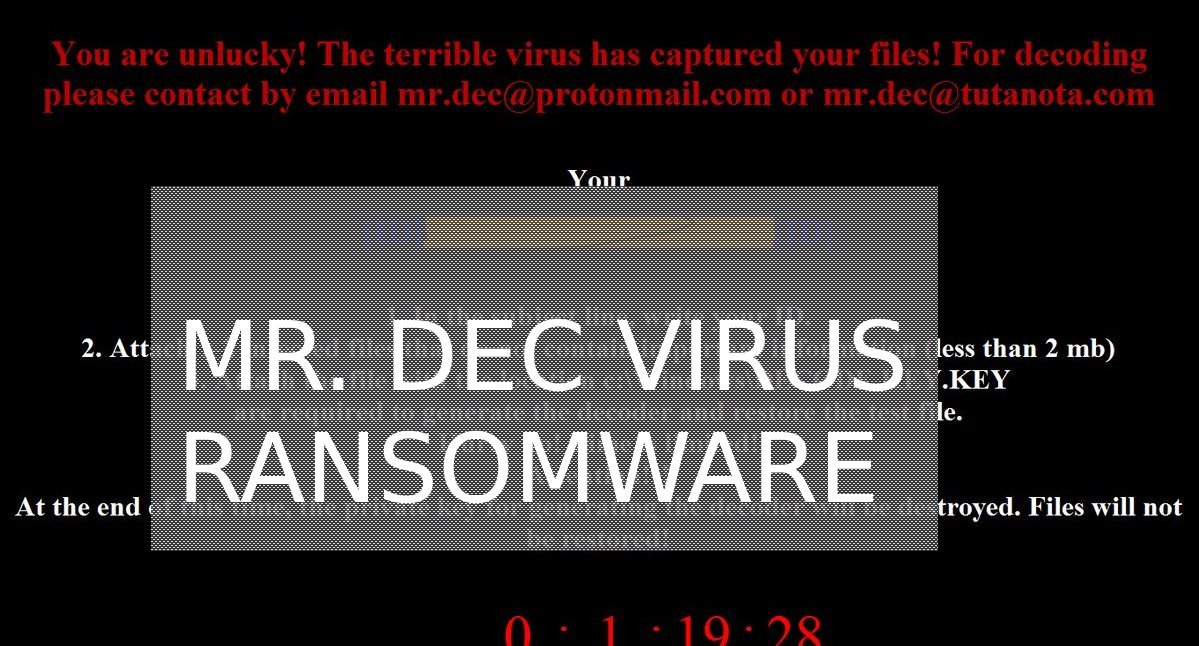
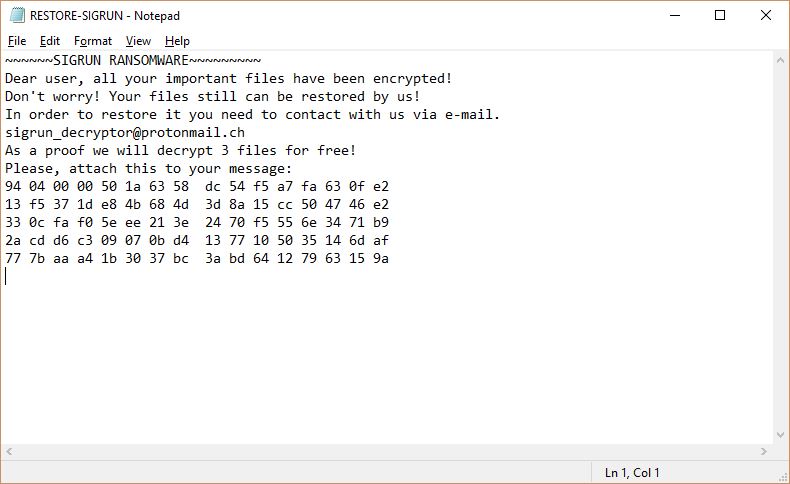
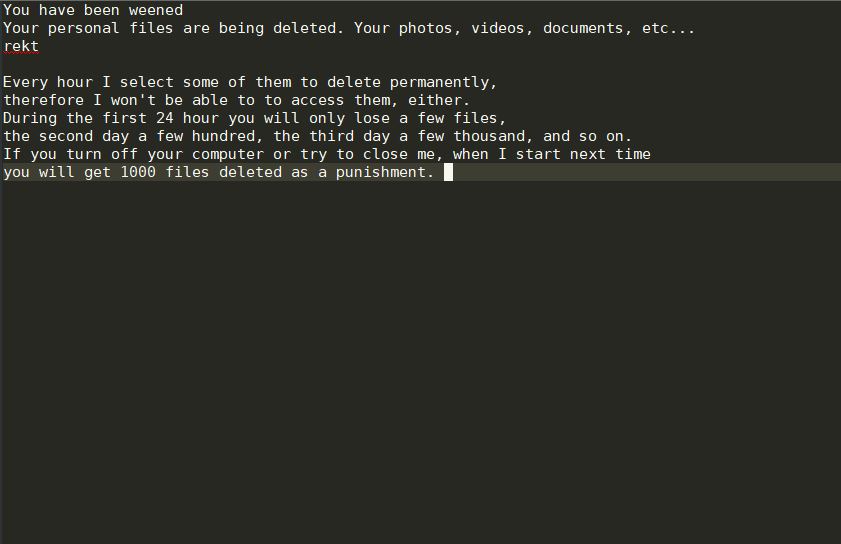
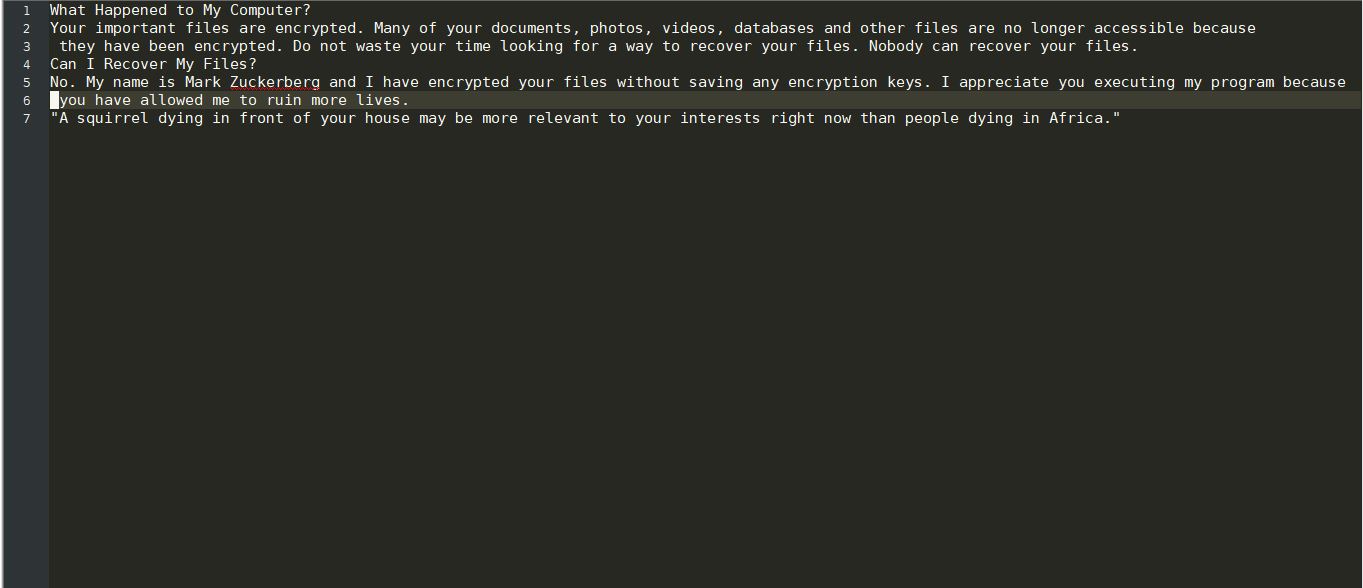
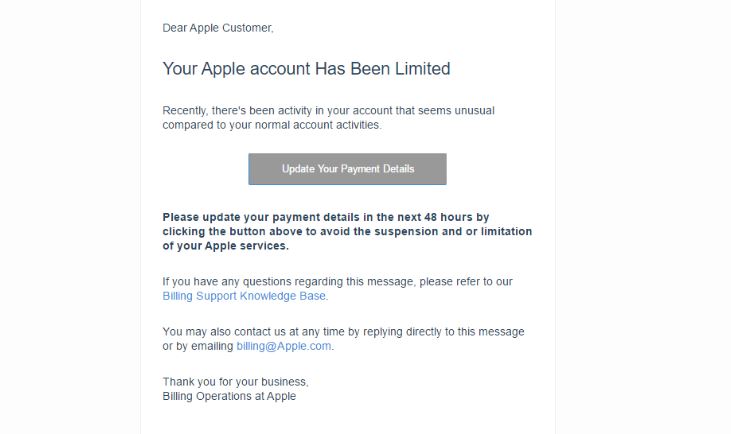
The Scarab-osk virus is the newest descendant from the Scarab ransomware family. It follows the already established behavior tactics of the previous versions and renames the target data with the .osk extension. Its development shows that the computer hackers continue…