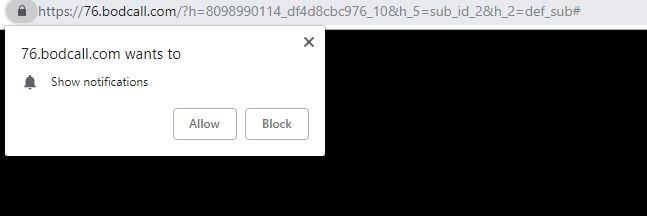
Remove Bodcall.com Notifications and Ads
Bodcall.com is a browser redirect which may try to trick you into subscribing to its notifications. The site will likely display a “confirm notification” message. However, if you click on the “allow” button it is very possible that you will…