Zorin Virus (.zorin File) – How to Remove + Restore Data
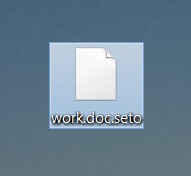
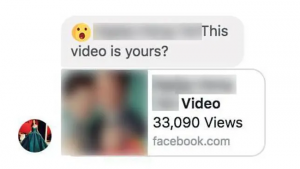
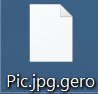
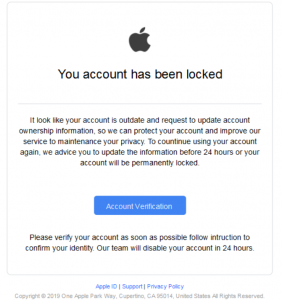
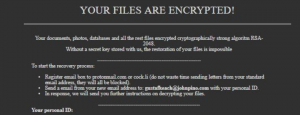
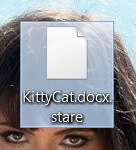
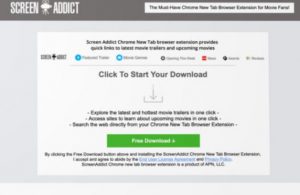
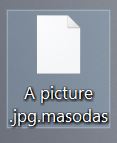
What is Zorin virus? What are .zorin files? How to remove Zorin ransomware and try to restore .zorin encrypted files? The Zorin ransomware is the type of threat, whose main goal is to enter your computer and encrypt the files…