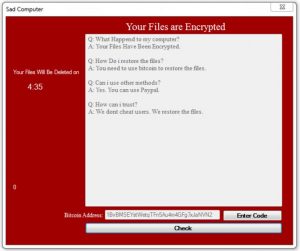
.sad Files (Sad Computer Ransomware) – WHAT IS IT + Remove It
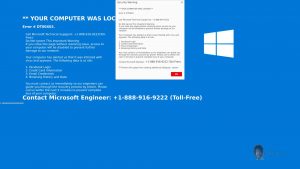
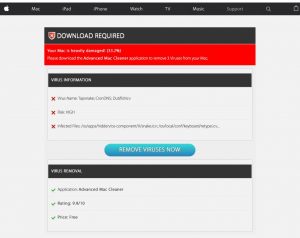
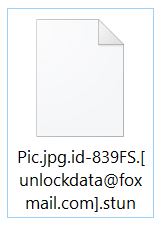
What are .sad files? What is .sad ransomware virus? How to remove Sad Ransomware and try to restore .sad encrypted files? A ransomware virus, called Sad Ransomware was recently detected by security researchers. The virus uses the .sad file extension…