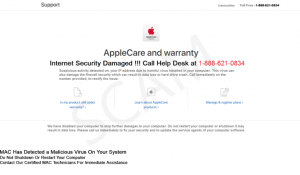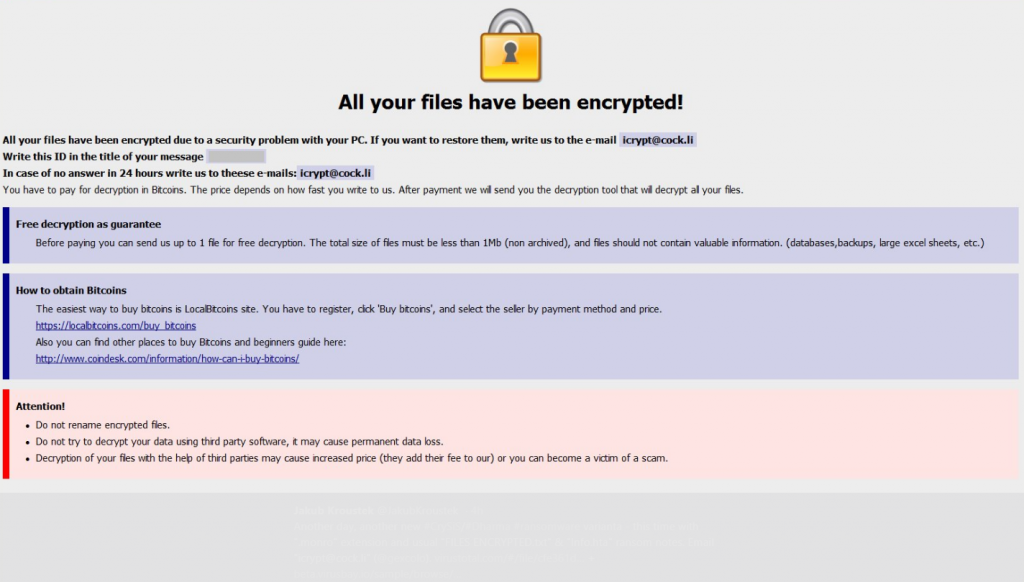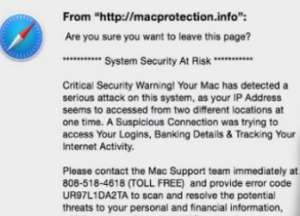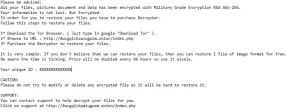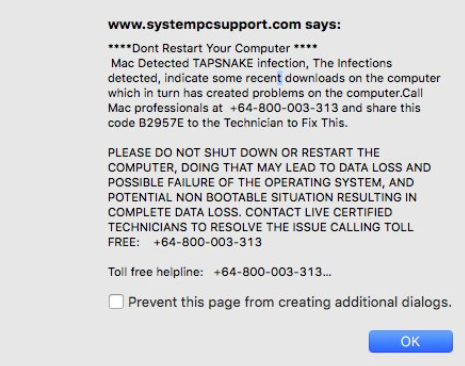
TAPSNAKE Infection (“Mac Detected TAPSNAKE” Scam) – How to Remove It
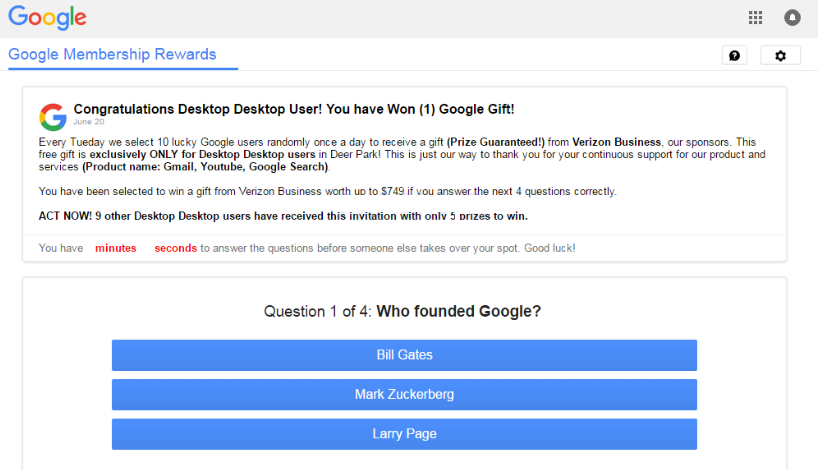
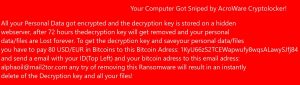
This article has been created in order to give you insight on how to quickly remove the TAPSNAKE infection scam from your Mac effectively. The tech support scams for Macs have recently seen a new spike and the TAPSNAKE infection…