Eorezo Ads “Virus” and Milicenso Trojan – How to Remove Them
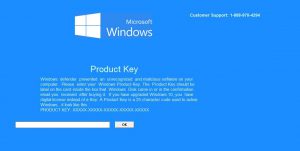
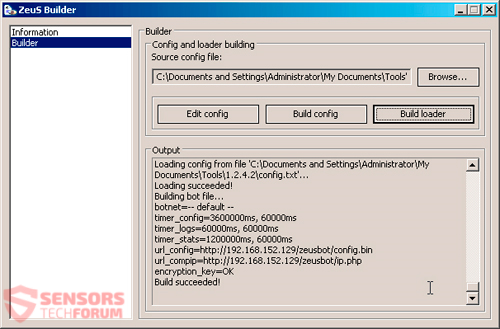
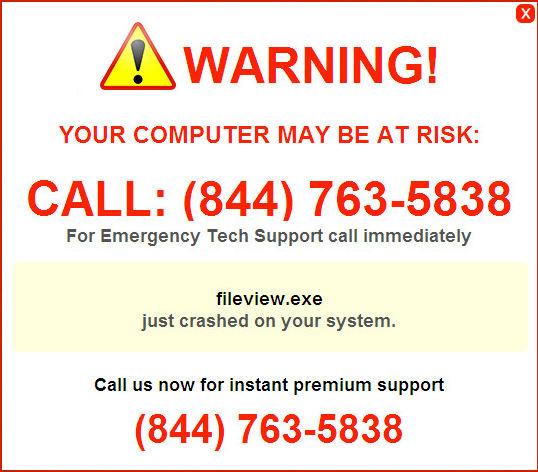
What Is Eorezo Ads “Virus”? This article aims to help you by explaining how to remove Eorezo adware from your computer and prevent it from displaying pop-ups in the future as well. New ad-supported software, known by the name Eorezo…