Remove Asruex Trojan From Your PC
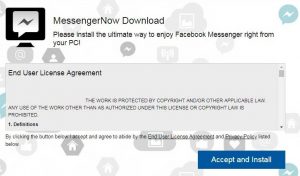
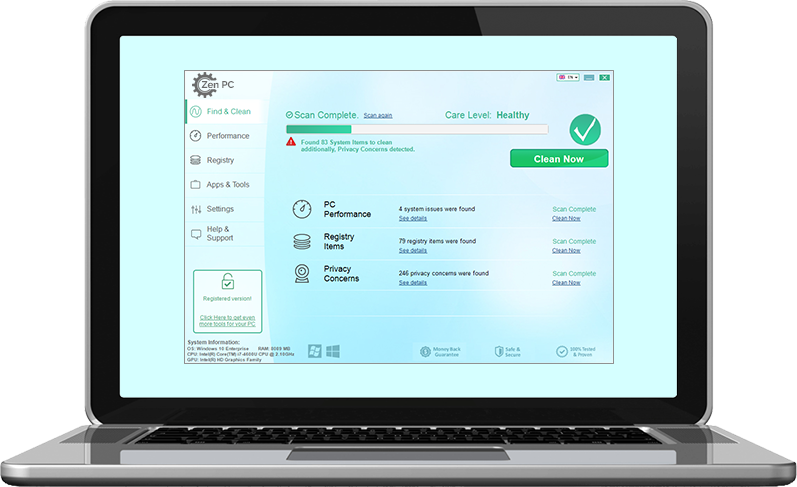
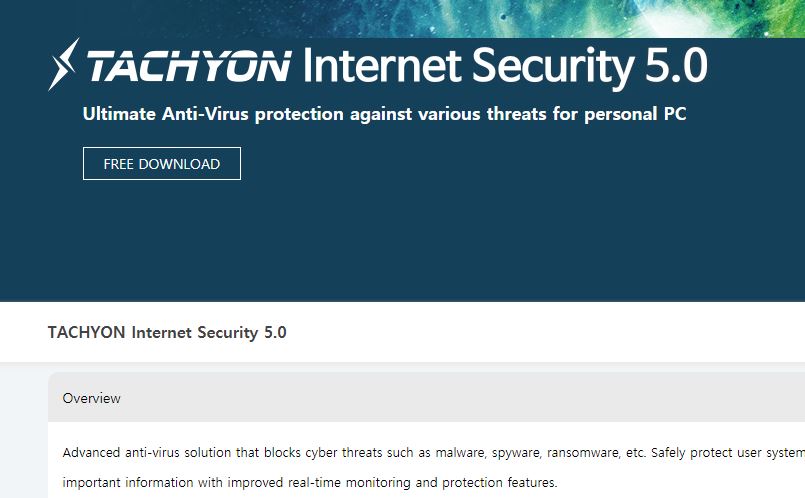
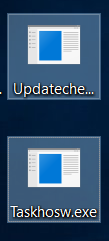
What is Asruex? How to remove Asruex Trojan from your PC or Mac? The Asruex Trojan is a dangerous malware threat which is designed for Microsoft Windows computers. It can be acquired from various sources, every attack campaign can focus…