
Trojan.Olydestroy Virus – How to Remove It and Restore Destroyed Files
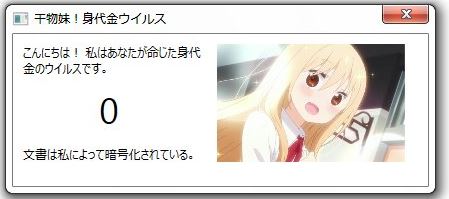
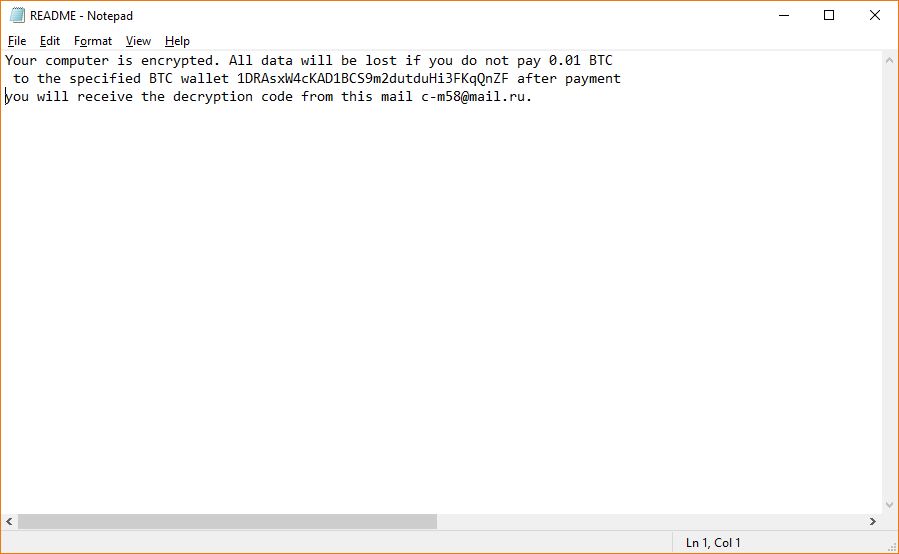
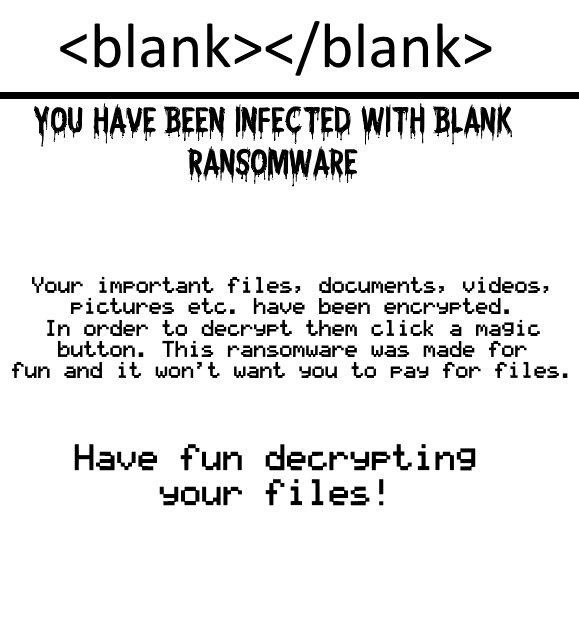
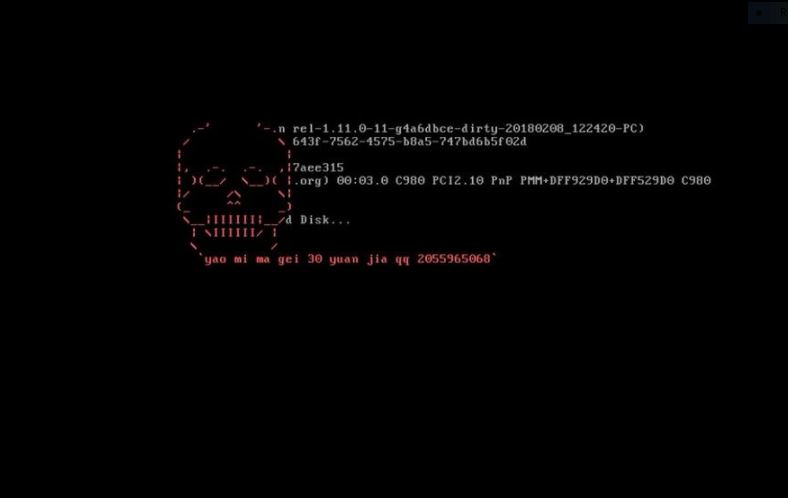
This article explains what is Trojan.Olydestroy virus and how to remove it from your computer plus how to try and restore your encrypted files. Trojan.Olydestroy is the type of malware which is the last thing you want on your computer.…







![Taskhostw.exe – What Is It + How to Remove It [Fix] Taskhostw.exe - What Is It + How to Remove It [Fix]](https://cdn.sensorstechforum.com/wp-content/uploads/2018/02/taskhostw-exe-what-is-it-how-to-remove-it-1024x576.jpg)

![Java:Malware-gen [Trj] Trojan – How to Detect and Remove CrossRAT](https://cdn.sensorstechforum.com/wp-content/uploads/2016/02/remote-access-trojan-sensorstechforum-300x260.png)

