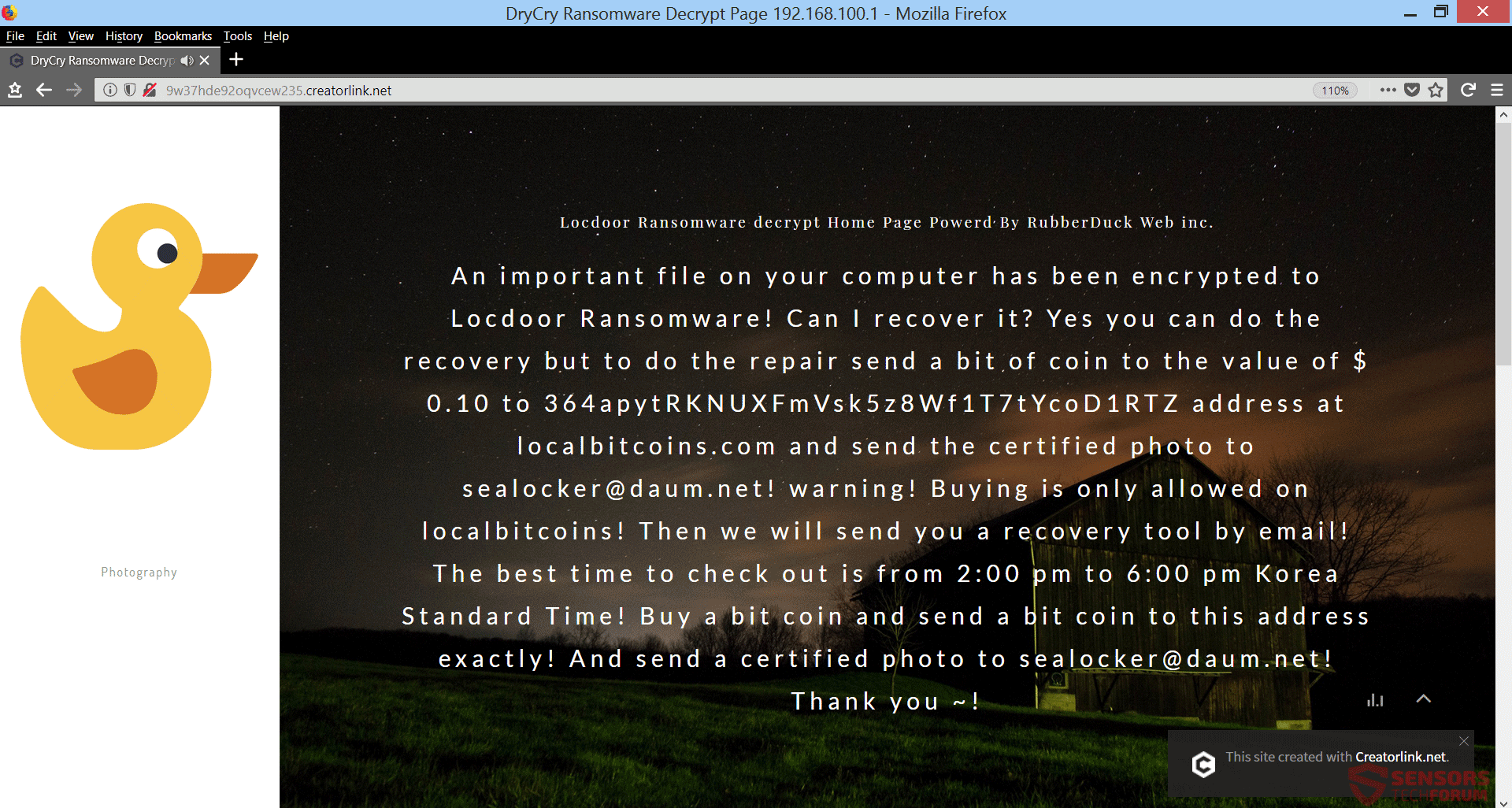
Remove Locdoor (DryCry) Ransomware – Restore Data
This article will help you remove Locdoor ransomware efficiently. Follow the ransomware removal instructions provided at the end of the article. Locdoor is a virus that claims to encrypt your files and demands money as a ransom to supposedly get…