A new botnet carrying out large-scale attacks has been discovered by security researchers. The botnet is dubbed DDG and is proclaimed the second biggest mining botnet ever. Its targets are the Redis and OrientDB servers.
DDG.Mining.Botnet Attacks Description
A couple of months ago Netlab researchers noticed a large-scale ongoing scan that was targeting OrientDB databases. After a further analysis, the researchers uncovered that this is “a long-running botnet” which is aimed at mining Monero. Netlab named the botnet DDG.Mining.Botnet after its core function module.
According to statistics, the botnet has mined more than 3,395 Monero which amounts to more than $920,000, making it the second largest Monero botnet after the MyKings botnet.
The botnet has been active at least since late 2016 and had been updated thoroughly during the course of 2017.
DDG uses a C2 and HUB layout to communicate with its clients. The HUB is a set of IPs and domain names that are used to provide Miner program for the compromised clients to download.
Researchers also note that they were able to register and sinkhole two domain names which were deployed by the botnet’s v2011. Thanks to this activity, it was possible for them to have a close look at the entire DDG botnet structure.
DDG Botnet Monero Mining Activities
The botnet uses https://monero.crypto-pool.fr/ as its mining pool, and three Monero wallets:
- Wallet #14AxgKJtp8TTN9Ab9JLnvg7BxZ7Hnw4hxigg35LrDVXbKdUxmcsXPEKU3SEUQxeSFV3bo2zCD7AiCzP2kQ6VHouK3KwnTKYg
- Wallet #245XyPEnJ6c2STDwe8GXYqZTccoHmscoNSDiTisvzzekwDSXyahCUmh19Mh2ewv1XDk3xPj3mN2CoDRjd3vLi1hrz6imWBR1
- Wallet #344iuYecTjbVZ1QNwjWfJSZFCKMdceTEP5BBNp4qP35c53Uohu1G7tDmShX1TSmgeJr2e9mCw2q1oHHTC2boHfjkJMzdxumM
Apparently, the pool made it possible for the researchers to check the payments of the wallets – a total of 3,395 Monero.
The DDG botnet exploits the following remote code execution flaw: CVE-2017-11467. Through this exploitation in the form of a brute-force attack, the botnet operators are successfully compromising the above-mentioned servers. What is troublesome is that the cybercriminals behind this operation are targeting servers with powerful computing capabilities.
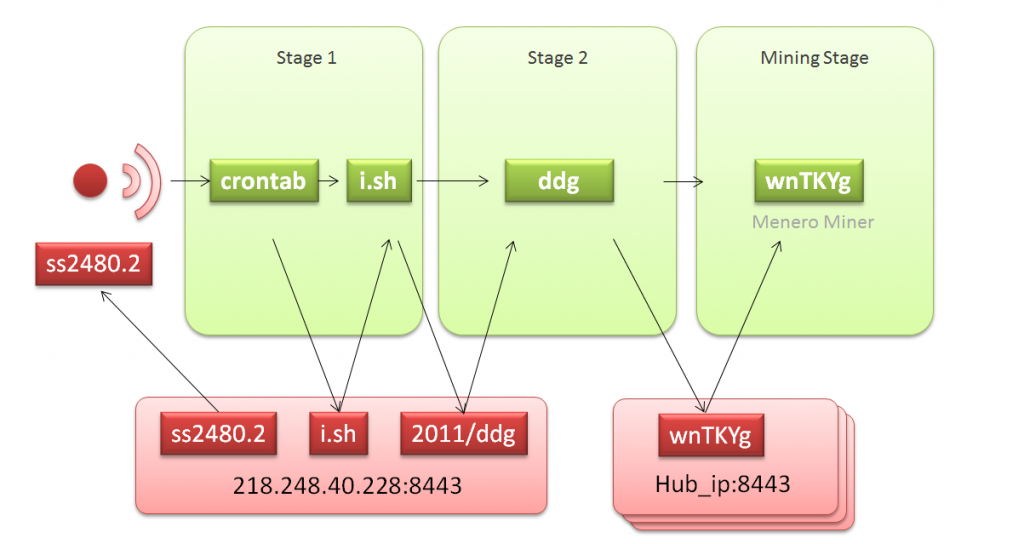
As for the attack itself, it follows this frame:
- Initial Scanning: Cybercriminals are exploiting the known RCE vulnerability of the OrientDB database to drop the attack payload;
- Stage 1: Cybercriminals are modifying local Crontab scheduled tasks, downloading and executing i.sh (hxxp: //218.248.40.228:8443/i.sh) on the primary server to keep it synchronized every 5 minutes;
- Stage 2: DDG traverses the built-in file hub_iplist.txt, then it checks the connectivity of every single entry and tries to download the corresponding Miner program wnTKYg;
- Mining Stage: The miner program is initiated, using the computing resources of the compromised host to begin mining for the cybercriminals’s wallet.
It is highly recommended for computer users to scan their system for active infections and malware using an anti-malware program. Such a program serves to prevent many malicious actions and stop further distribution of malware.
SpyHunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter


