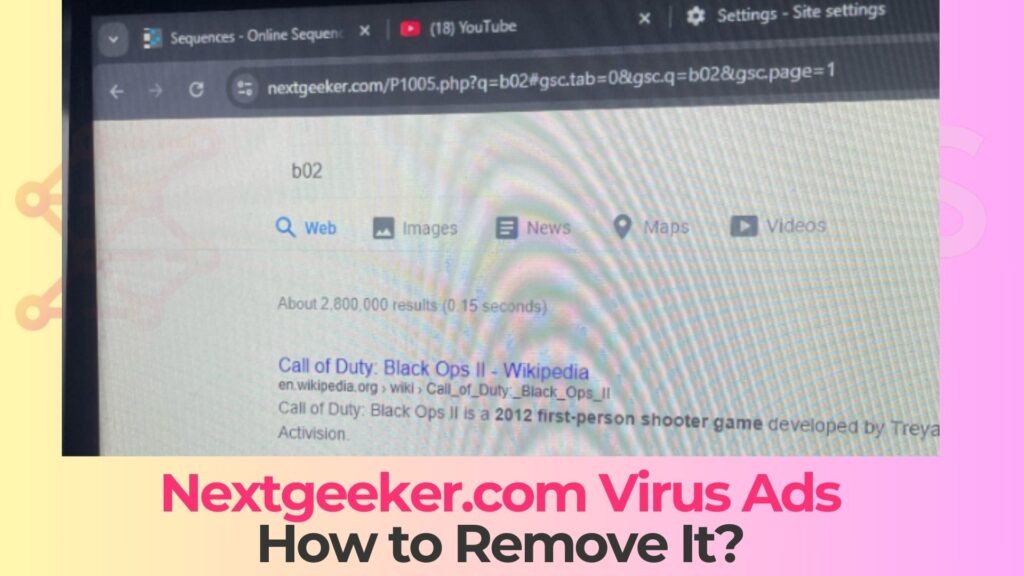
If your browser suddenly starts redirecting every search through Nextgeeker.com, shows unfamiliar ads, or feels “controlled” by something you never installed, you are likely dealing with a browser hijacker that pushes a fake search engine. This is not a harmless quirk. It usually means a potentially unwanted program (PUP) is actively tampering with your browser settings in the background. Read this article to find out what Nextgeeker.com Fake Search Engine Redirects really are, how this hijacker lands on your system, what it does behind the scenes, and what you should keep in mind before you proceed with Nextgeeker.com Fake Search Engine Redirects – Removal using the dedicated guide below.
Nextgeeker.com behaves like a fraudulent search engine that exists primarily to monetize your traffic, collect data, and funnel you through shady pages instead of providing clean, organic search results. In many cases, the engine itself simply forwards queries to a legitimate provider in the background, but injects tracking and paid redirections along the way. The core problem is that you do not get to choose it: a browser hijacker forces this search engine into your browser configuration and keeps it there through policies and other persistence tricks.
Because this threat class is often classified as a PUP, many users underestimate the risks. However, unwanted search redirects can expose you to deceptive ads, phishing pages, and additional malware. If your homepage, new tab page, or default search engine are locked on Nextgeeker.com and revert after each change, you are most likely facing an active hijacker that requires a thorough cleanup.
What is Nextgeeker.com Fake Search Engine?
Nextgeeker.com Fake Search Engine Redirects is a term used to describe the unwanted behavior caused by a browser hijacker that forces your browser to use Nextgeeker.com as a default search provider and landing page. Technically, this is not just a single executable virus, but a combination of components:
- A fake search engine endpoint (Nextgeeker.com) that receives your queries and returns manipulated results.
- A browser hijacker PUP installed on the system which modifies key browser settings.
- Additional configuration artefacts such as policies, registry key entries, or browser profiles that maintain persistence.
Nextgeeker.com Short Overview
| Type | Browser Hijacker, Redirect, PUA |
| Short Description | A suspicious website and rogue search engine that hijacks your browsers and causes redirects. |
| Symptoms | Unwanted pop-ups may start appearing while you are browsing the web. A browser hijacker may be downloaded without your knowledge. |
| Removal Time | Approximately 15 minutes for a full-system scan |
| Removal Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
The short description of this threat summarizes it well: it is a fraudulent search engine pushed by a browser hijacker type of PUP running actively on the victim’s computer. In practice, the PUP integrates with one or more browsers (typically Chrome, Edge, Firefox, or Chromium-based variants) and silently replaces:
- Your default search engine in the address bar and search box.
- The homepage that opens when you start the browser.
- The new tab page that appears whenever you open a fresh tab.
From a security standpoint, the classification as a browser hijacker is crucial. Unlike legitimate search providers, Nextgeeker.com is introduced without transparent consent and focuses on advertising, data collection, and traffic redirection rather than on delivering high-quality search results.
Nextgeeker.com as a fake search provider
Fake search engines of this type often do not operate their own full search index. Instead, they act as an intermediary that:
- Logs your query and associated identifiers (IP address, browser type, approximate location, language, etc.).
- Forwards the query to a real search engine or a partner feed in the background.
- Injects promoted links, pop-ups, banners, or redirects before you see the final results.
This approach allows the operators to generate ad revenue, push low-quality or misleading content, and build detailed profiles of users’ browsing habits. What makes Nextgeeker.com particularly problematic is that all of this is enabled by a PUP that has already broken your trust by forcibly taking over the browser.
Browser hijacker and PUP characteristics
The component that installs and controls Nextgeeker.com behaves like a typical browser hijacker:
- It installs silently or with misleading wording inside software bundles.
- It requests or abuses excessive permissions in the browser (for example, full control over “change your search settings”).
- It changes settings without clear, informed consent and actively resists user attempts to revert them.
Because it focuses on monetization and tracking rather than direct system damage, many security vendors label it as a PUP instead of a high-risk Trojan. However, its presence should be considered a security red flag, especially because the same channel that delivered this hijacker can be reused to push much more dangerous payloads in the future.
How Did I Get Nextgeeker.com on My Browser?
Most users do not deliberately visit Nextgeeker.com and set it as their search engine. Instead, they encounter it as a side effect of installing other software or interacting with deceptive online content. Understanding the main infection vectors will help you avoid similar hijackers going forward.
Bundled installers and freeware packages
The most common path for Nextgeeker.com-like hijackers is through software bundling. Free programs, questionable download managers, or “cracks” frequently include additional offers that are pre-selected during installation. These may be presented as “search enhancements,” “security tools,” or “browser optimizers,” but in reality they are adware and PUPs.
- During the setup wizard, optional components may be hidden behind Advanced or Custom options.
- Default choices often authorize changes to your browser’s homepage, new tab page, and default search engine.
- Declining these offers can be intentionally confusing, and many users click Next without noticing what is being installed.
If you recently installed freeware from third-party download portals or cracked activators, that is a strong candidate for the source of the Nextgeeker.com hijacker.
Misleading ads, fake updates, and pushed extensions
Another frequent vector is aggressive advertising and deceptive pages that prompt you to install browser extensions or “updates.” These may appear while visiting streaming portals, file-sharing sites, or other low-reputation web pages. Typical scenarios include:
- Pop-ups claiming that your browser is “out of date” or that a “critical codec/update” is required to view content.
- Promotions for “better search,” “faster browsing,” or “shopping helpers” that are in fact hijacker extensions.
- Push notifications that trick you into granting broad permissions or clicking through to extension stores with misleading descriptions.
Once installed, these add-ons may request the ability to “read and change all your data on websites you visit” and “change your search settings,” which they then exploit to redirect all searches through redirect chains ending at Nextgeeker.com.
System-level changes and policies
More persistent variants do not rely solely on standard browser settings. They may apply policy-based configuration that causes the browser to display messages like “Managed by your organization” even on home machines. Behind the scenes, this means registry key changes or configuration files are forcing the hijacker’s preferences, blocking you from changing them through normal menus.
In these cases, simply resetting the browser may not be enough. You must assume that a PUP or script on the system is actively reapplying the Nextgeeker.com configuration at every startup until its core files and policies are removed.
What Does Nextgeeker.com Do?
Once active, the Nextgeeker.com hijacker focuses on traffic redirection, data collection, and ad injection. While it may not encrypt files or behave like classic ransomware, the long-term impact on privacy and security can be significant.
Forced redirects and search manipulation
The most visible symptom is the constant redirect behavior. Instead of letting you use your preferred search engine, the hijacker:
- Routes all address bar and search box queries through Nextgeeker.com.
- Opens this site as a start page or new tab, even after you change settings back to normal.
- Occasionally redirects you further to other dubious domains, including scam pages or pages that aggressively push software and subscriptions.
This breaks your normal browsing workflow and ensures that all your search traffic is first monetized by the operators of the fake engine.
Tracking, profiling, and data harvesting
Because all queries and interactions pass through their infrastructure, the operators can accumulate extensive analytics on how you browse. The hijacker and its associated scripts may:
- Collect search phrases, clicked results, visited domains, and timestamps.
- Log device and browser information, including version, language, and basic geolocation.
- Store identifiers such as cookies, advertising IDs, and possibly referrer chains that link multiple sessions together.
This data is typically used for targeted advertising and sold or shared with third parties. While not always labeled as “sensitive” in a legal sense, such profiles can be abused for phishing, social engineering, and further malicious campaigns.
Exposure to additional malware and scams
Nextgeeker.com does not operate in isolation. Fake search engines often redirect to:
- Websites distributing other PUPs, browser extensions, and adware.
- Technical support scam pages that show fake alarms and attempt to make you call fraudulent numbers—this is known as fake tech support.
- Phishing portals that imitate banking, email, or social media login pages.
Even if the hijacker itself is “only” a PUP, the environment it creates drastically increases your risk of landing on pages that can steal credentials, plant more aggressive malware, or trick you into paying for bogus services. Treat the ongoing redirects as a warning sign that the integrity of your browsing environment has been compromised.
Performance and usability impact
Constant redirects and injected content can also have a noticeable impact on how your browser performs:
- Pages may load slower due to multiple intermediate requests and additional tracking scripts.
- The interface becomes cluttered with sponsored content, banners, and new tab overlays.
- Settings menus may appear locked or revert after every restart, creating the impression that the browser is “broken.”
These symptoms often cause users to suspect a deeper infection or even a system-level computer virus. In many cases, the underlying cause is this kind of hijacker PUP manipulating the browser rather than the entire operating system—but that does not make it safe to ignore.
How to Remove Nextgeeker.com Fake Search Engine Redirects
Nextgeeker.com Fake Search Engine Redirects – Removal is not just about changing the search engine back once. Because the hijacker uses persistence mechanisms and may add policies or additional components, effective removal means cleaning all layers of the infection. The dedicated removal guide beneath this article is designed to walk you through that process in detail.
Why a structured removal approach is important
Simply uninstalling a visible extension or closing the hijacked tab is rarely enough. A robust cleanup strategy should take into account that:
- The PUP may exist both as a browser add-on and as an installed program in the operating system.
- Registry key or policy entries may silently enforce Nextgeeker.com as the default search engine and homepage.
- Other components installed at the same time (toolbars, “utility” programs, or update helpers) can reinstall the hijacker if left behind.
This is why the removal guide focuses on detecting and eliminating the hijacker’s core files, its browser extension hooks, and any system-level settings that allow it to persist after reboot.
Automated scans combined with manual inspection
Modern security tools are generally capable of detecting browser hijackers and associated PUPs. Running a full system scan with a reputable anti-malware program can help you identify:
- Known Nextgeeker.com-related components and helper executables.
- Suspicious browser extensions and add-ons tied to redirect behavior.
- Residual registry entries or scheduled tasks connected to the hijacker.
However, automated detection is only part of the picture. Manual verification of installed programs, browser profiles, and configuration policies is just as important. Even if a scanner removes the main payload, a leftover profile, policy object, or extension may continue to enforce the fake search engine until you remove or reset it properly.
Restoring clean browser settings and hardening against hijackers
After the malicious components have been removed, it is crucial to restore a clean configuration and reduce the chance of future hijacking attempts. The removal instructions below this article typically include measures such as:
- Reconfiguring the homepage, new tab page, and default search engine to your preferred, legitimate provider.
- Checking for unknown or untrusted extensions and disabling or removing them.
- Reviewing browser policies, profiles, and synchronization options to ensure no unwanted settings are being reapplied from the cloud.
In addition, you should consider tightening your installation habits. Avoid software bundles from unverified portals, carefully read installation dialogs, and treat unsolicited prompts to install “search helpers” or “browser optimizers” with extreme skepticism.
What should you do?
If your browser is currently redirecting through Nextgeeker.com and refuses to respect your normal search settings, you are dealing with a browser hijacker that behaves as a fraudulent search engine and a PUP. Do not rely on quick fixes or temporary changes in the settings menu. Instead, assume that the hijacker is actively running on your system and can expose you to scams, intrusive ads, and further malware.
The safest next move is to follow the detailed Nextgeeker.com Fake Search Engine Redirects – Removal instructions provided in the guide directly below this article. They will help you scan for unwanted components, remove the hijacker’s core files, restore your preferred browser configuration, and apply basic hardening steps so that similar threats have a much harder time compromising your system in the future.
- Windows
- Mac OS X
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Safari
- Internet Explorer
- Stop Push Pop-ups
How to Remove Nextgeeker.com from Windows.
Step 1: Scan for Nextgeeker.com with SpyHunter Anti-Malware Tool



Step 2: Boot Your PC In Safe Mode





Step 3: Uninstall Nextgeeker.com and related software from Windows
Uninstall Steps for Windows 11
Uninstall Steps for Windows 10 and Older Versions
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully uninstall most programs.
Follow the instructions above and you will successfully uninstall most programs.
Step 4: Clean Any registries, Created by Nextgeeker.com on Your PC.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Nextgeeker.com there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Video Removal Guide for Nextgeeker.com (Windows).
Get rid of Nextgeeker.com from Mac OS X.
Step 1: Uninstall Nextgeeker.com and remove related files and objects
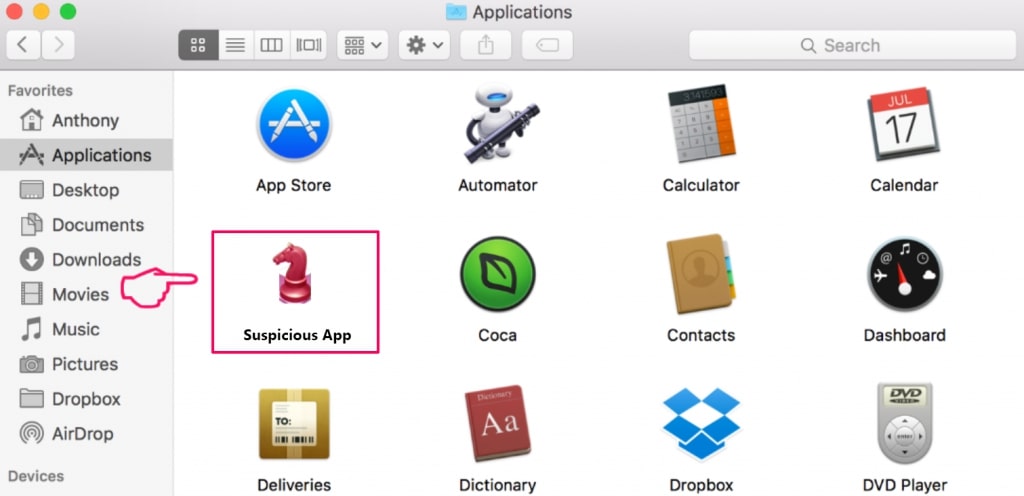
Your Mac will then show you a list of items that start automatically when you log in. Look for any suspicious apps identical or similar to Nextgeeker.com. Check the app you want to stop from running automatically and then select on the Minus (“-“) icon to hide it.
- Go to Finder.
- In the search bar type the name of the app that you want to remove.
- Above the search bar change the two drop down menus to “System Files” and “Are Included” so that you can see all of the files associated with the application you want to remove. Bear in mind that some of the files may not be related to the app so be very careful which files you delete.
- If all of the files are related, hold the ⌘+A buttons to select them and then drive them to “Trash”.
In case you cannot remove Nextgeeker.com via Step 1 above:
In case you cannot find the virus files and objects in your Applications or other places we have shown above, you can manually look for them in the Libraries of your Mac. But before doing this, please read the disclaimer below:
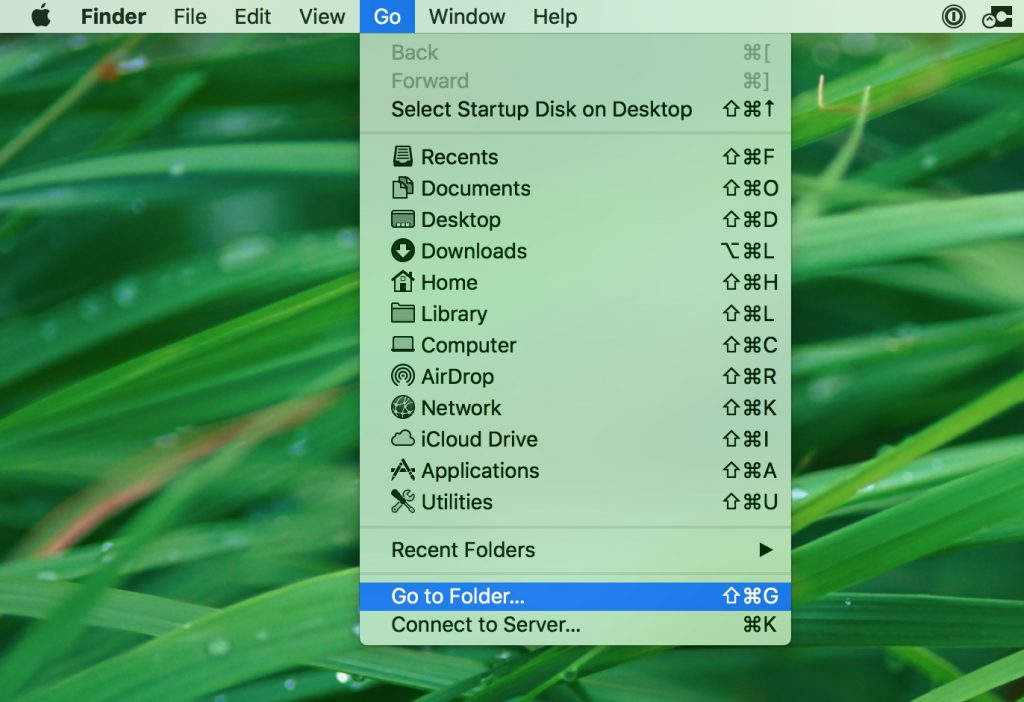
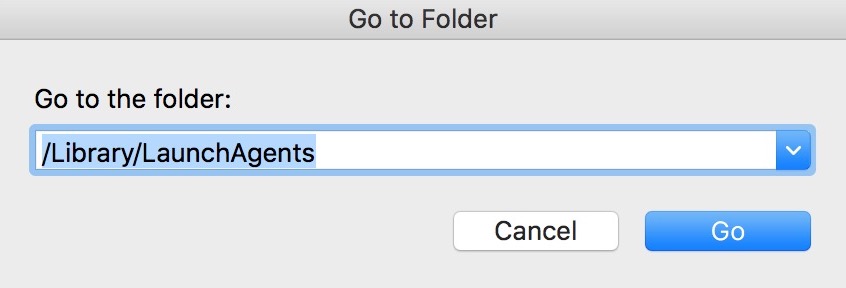
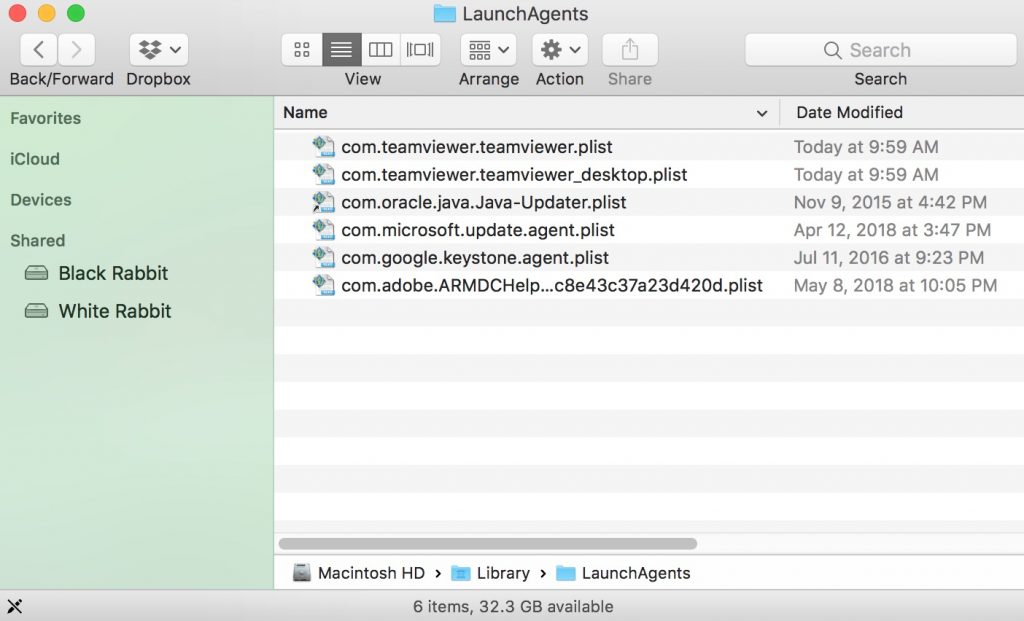
You can repeat the same procedure with the following other Library directories:
→ ~/Library/LaunchAgents
/Library/LaunchDaemons
Tip: ~ is there on purpose, because it leads to more LaunchAgents.
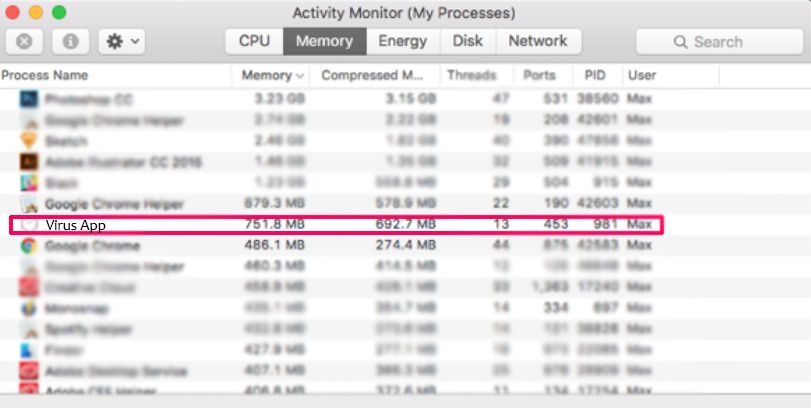
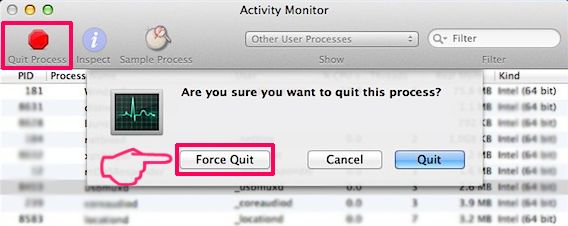
Step 2: Scan for and remove Nextgeeker.com files from your Mac
When you are facing problems on your Mac as a result of unwanted scripts and programs such as Nextgeeker.com, the recommended way of eliminating the threat is by using an anti-malware program. SpyHunter for Mac offers advanced security features along with other modules that will improve your Mac’s security and protect it in the future.
Video Removal Guide for Nextgeeker.com (Mac)
Remove Nextgeeker.com from Google Chrome.
Step 1: Start Google Chrome and open the drop menu
Step 2: Move the cursor over "Tools" and then from the extended menu choose "Extensions"
Step 3: From the opened "Extensions" menu locate the unwanted extension and click on its "Remove" button.
Step 4: After the extension is removed, restart Google Chrome by closing it from the red "X" button at the top right corner and start it again.
Erase Nextgeeker.com from Mozilla Firefox.
Step 1: Start Mozilla Firefox. Open the menu window:
Step 2: Select the "Add-ons" icon from the menu.
Step 3: Select the unwanted extension and click "Remove"

Step 4: After the extension is removed, restart Mozilla Firefox by closing it from the red "X" button at the top right corner and start it again.
Uninstall Nextgeeker.com from Microsoft Edge.
Step 1: Start Edge browser.
Step 2: Open the drop menu by clicking on the icon at the top right corner.
Step 3: From the drop menu select "Extensions".
Step 4: Choose the suspected malicious extension you want to remove and then click on the gear icon.
Step 5: Remove the malicious extension by scrolling down and then clicking on Uninstall.
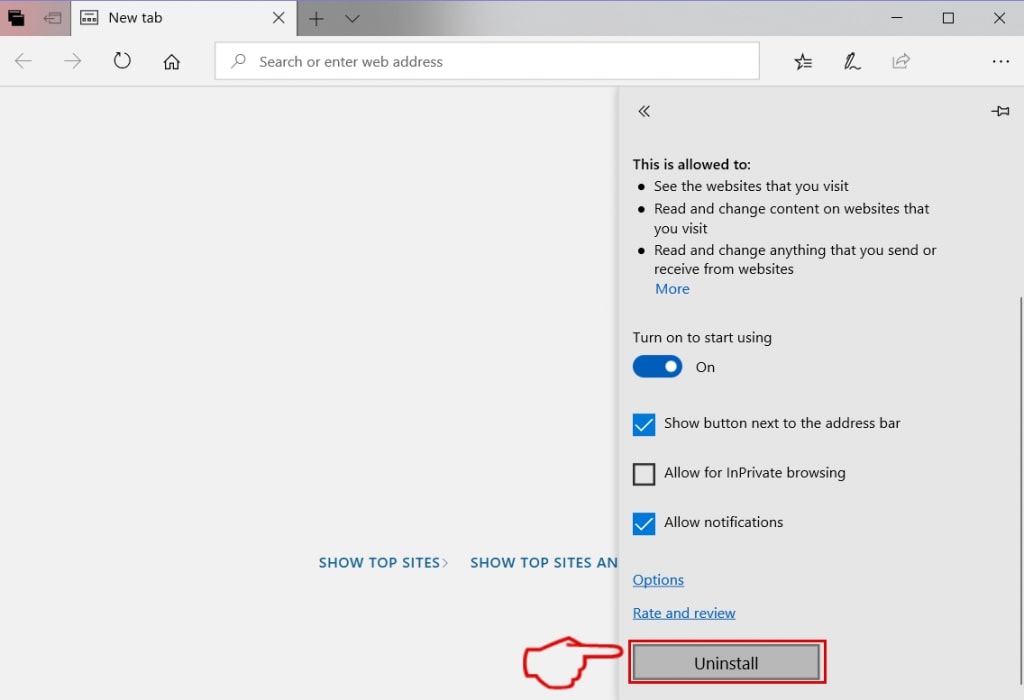
Remove Nextgeeker.com from Safari
Step 1: Start the Safari app.
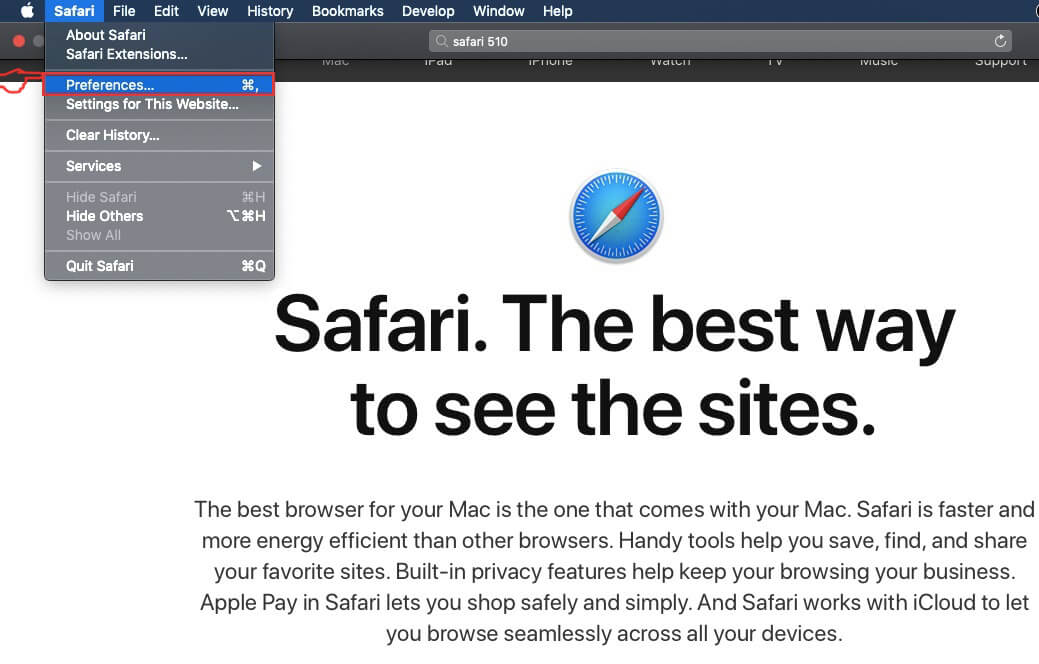
Step 2: After hovering your mouse cursor to the top of the screen, click on the Safari text to open its drop down menu.
Step 3: From the menu, click on "Preferences".
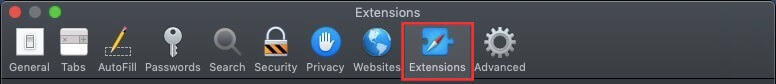
Step 4: After that, select the 'Extensions' Tab.
Step 5: Click once on the extension you want to remove.
Step 6: Click 'Uninstall'.
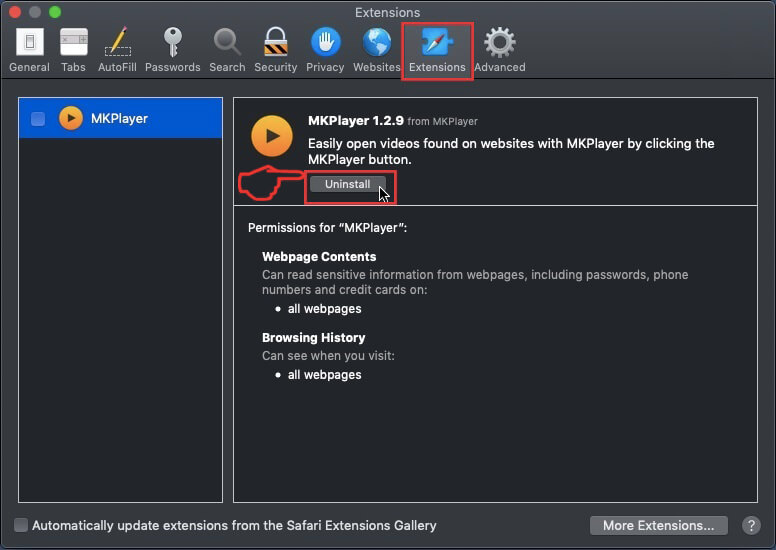
A pop-up window will appear asking for confirmation to uninstall the extension. Select 'Uninstall' again, and the Nextgeeker.com will be removed.
Eliminate Nextgeeker.com from Internet Explorer.
Step 1: Start Internet Explorer.
Step 2: Click on the gear icon labeled 'Tools' to open the drop menu and select 'Manage Add-ons'
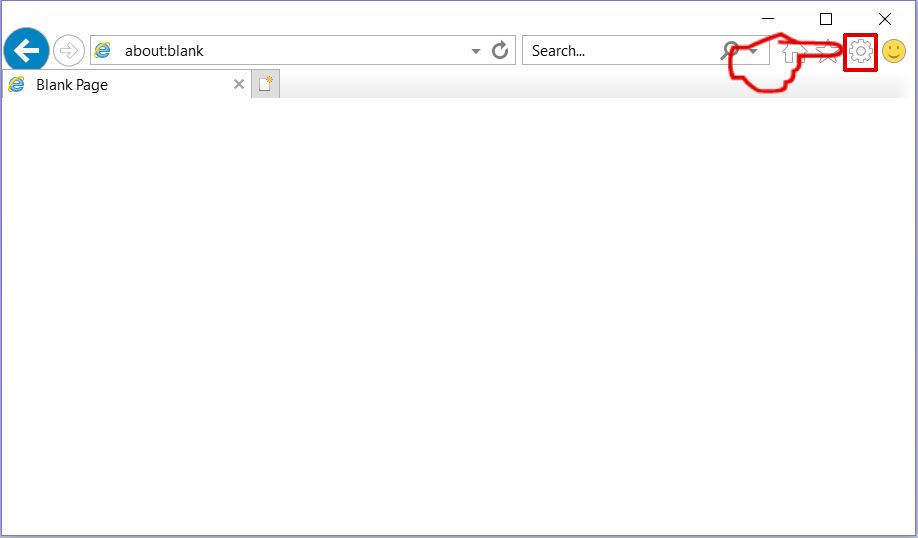
Step 3: In the 'Manage Add-ons' window.
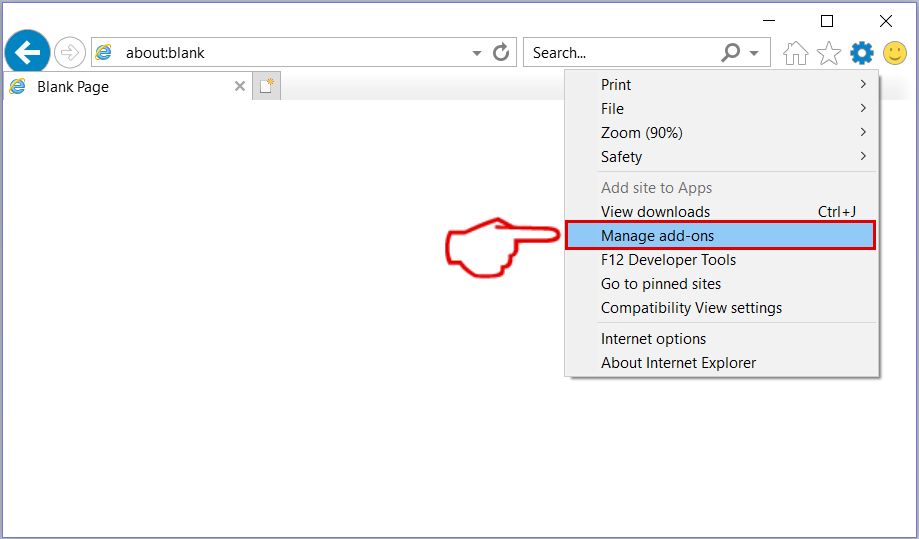
Step 4: Select the extension you want to remove and then click 'Disable'. A pop-up window will appear to inform you that you are about to disable the selected extension, and some more add-ons might be disabled as well. Leave all the boxes checked, and click 'Disable'.
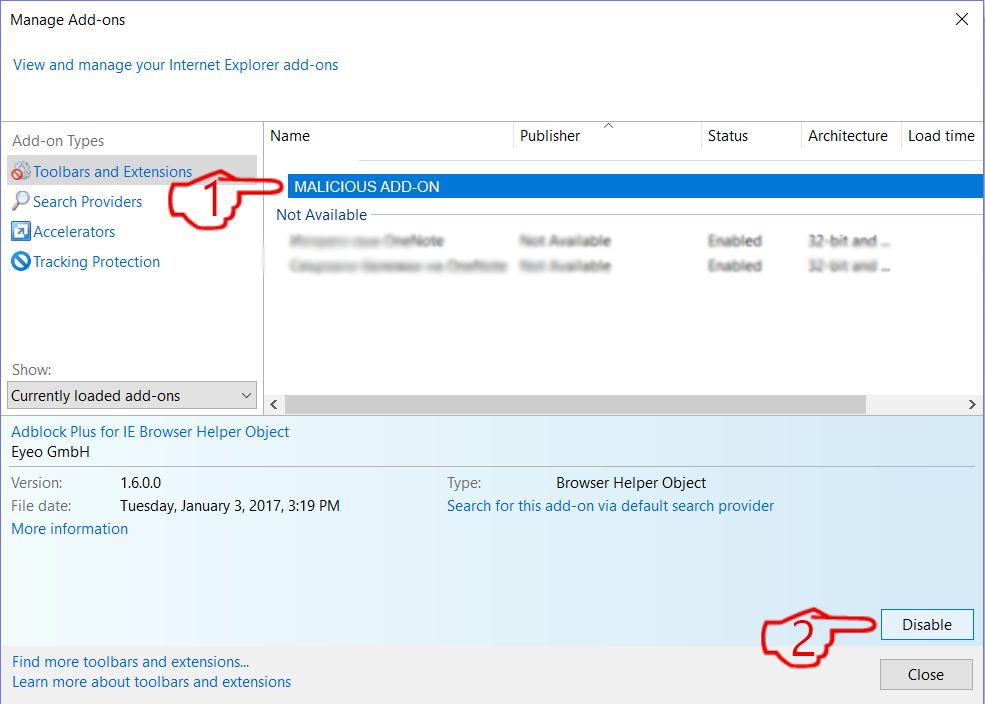
Step 5: After the unwanted extension has been removed, restart Internet Explorer by closing it from the red 'X' button located at the top right corner and start it again.
Remove Push Notifications from Your Browsers
Turn Off Push Notifications from Google Chrome
To disable any Push Notices from Google Chrome browser, please follow the steps below:
Step 1: Go to Settings in Chrome.
Step 2: In Settings, select “Advanced Settings”:
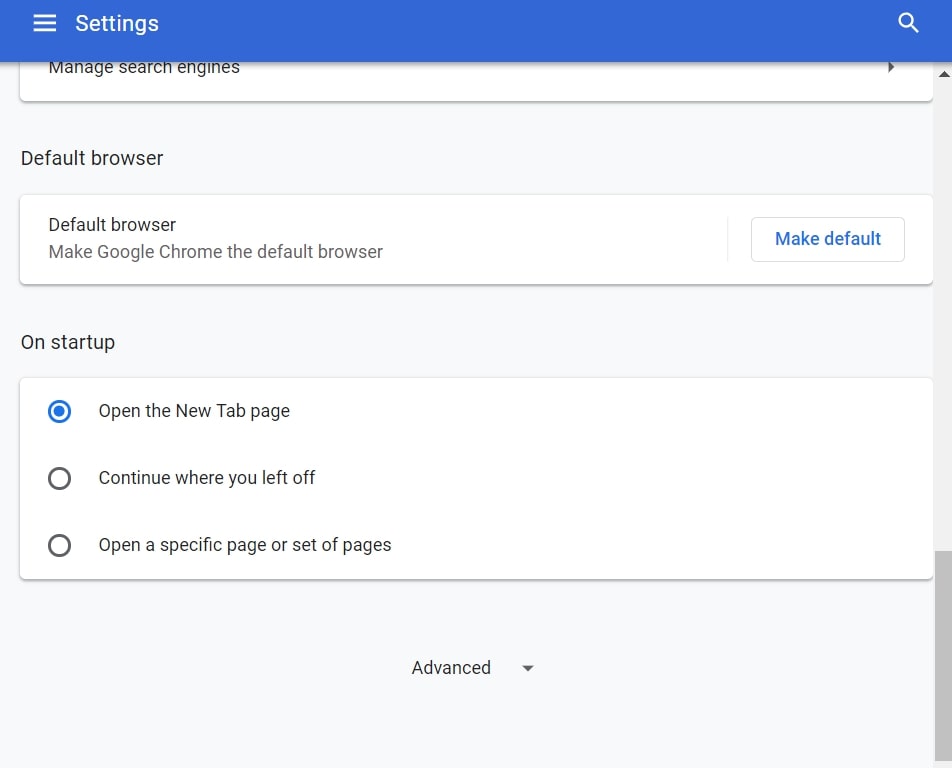
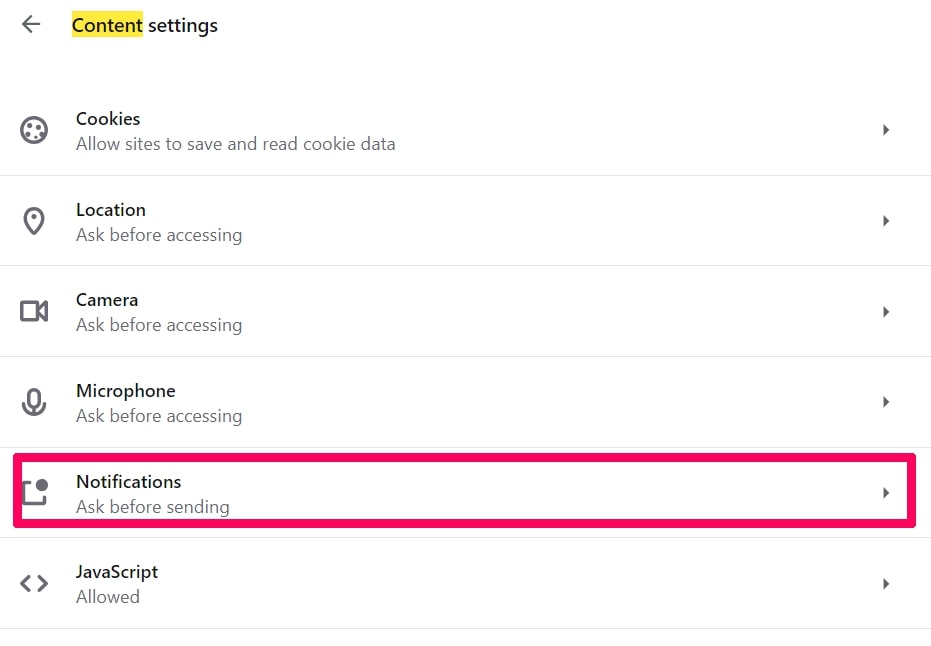
Step 3: Click “Content Settings”:
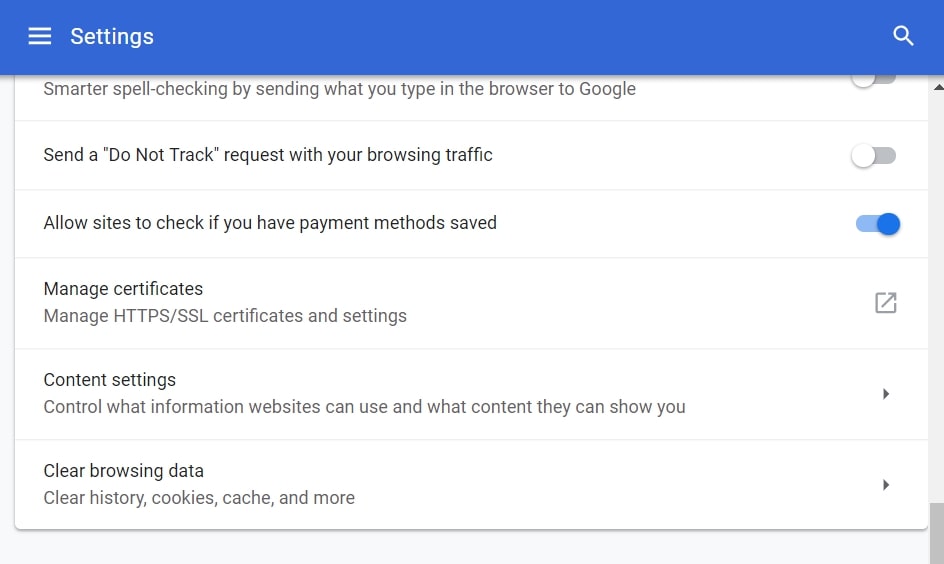
Step 4: Open “Notifications”:
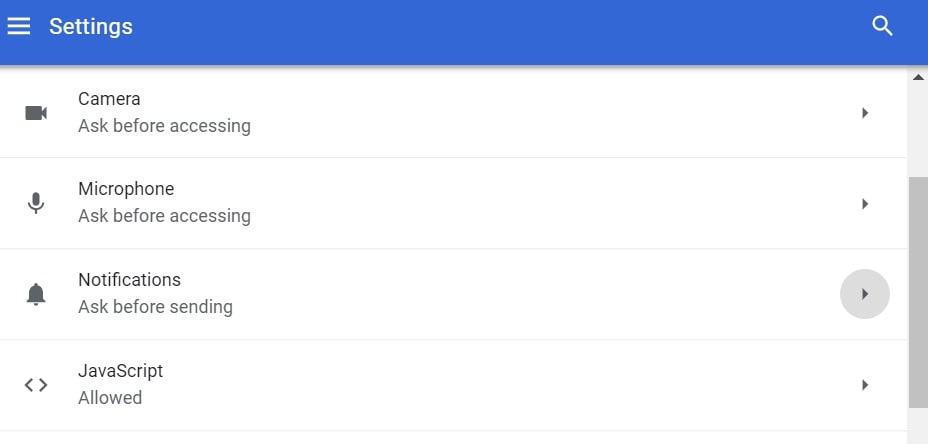
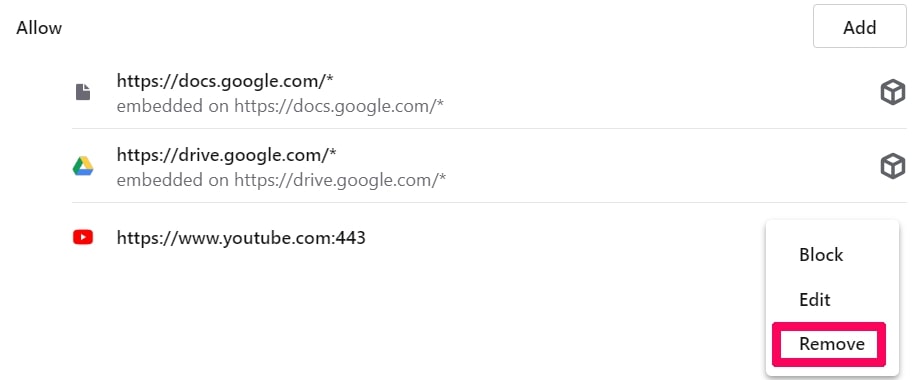
Step 5: Click the three dots and choose Block, Edit or Remove options:

Remove Push Notifications on Firefox
Step 1: Go to Firefox Options.
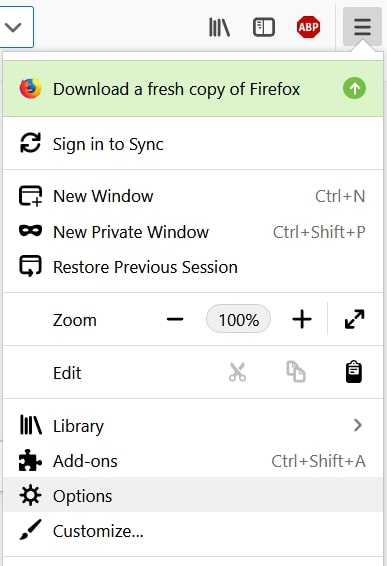
Step 2: Go to “Settings”, type “notifications” in the search bar and click "Settings":
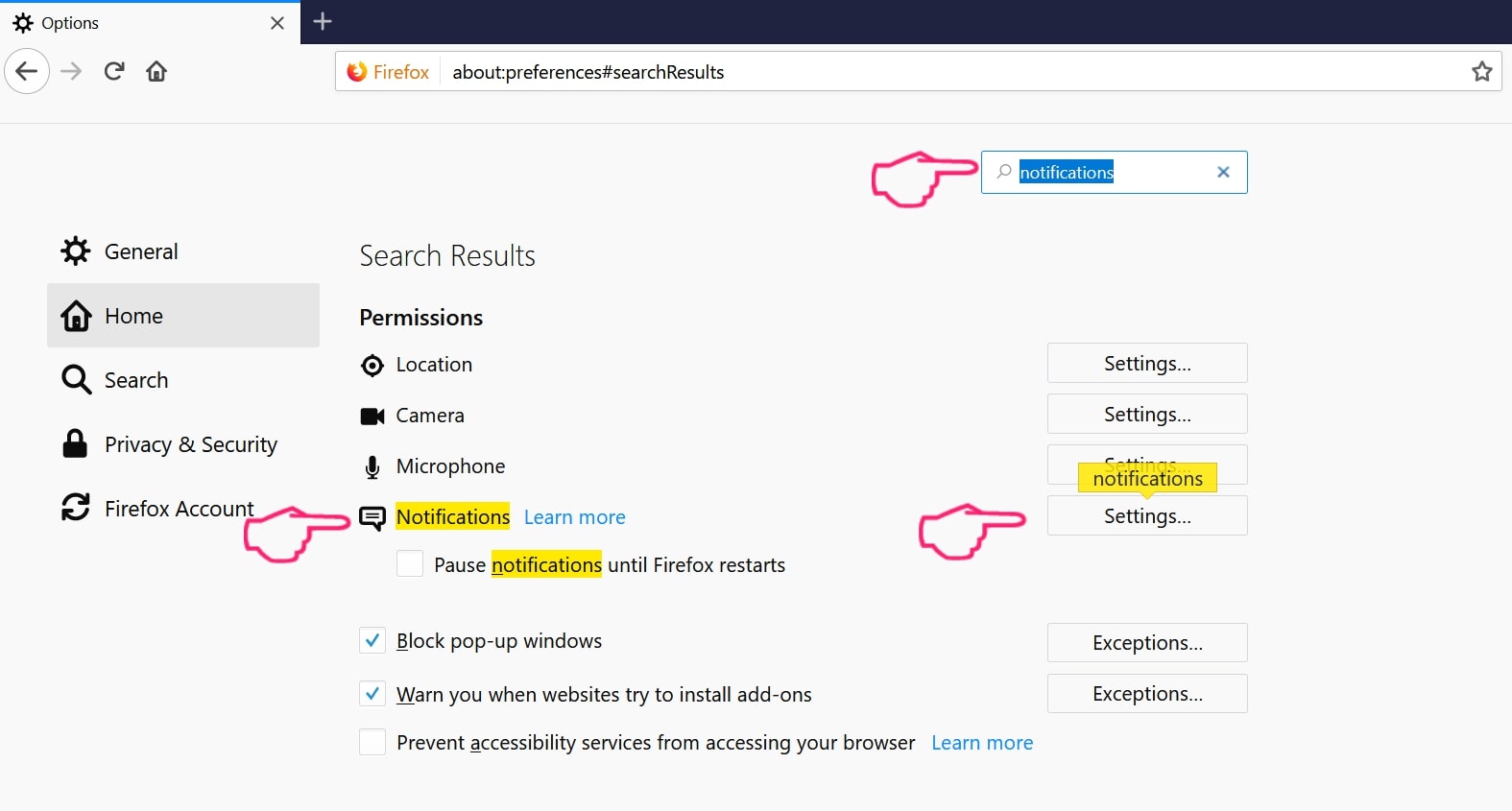
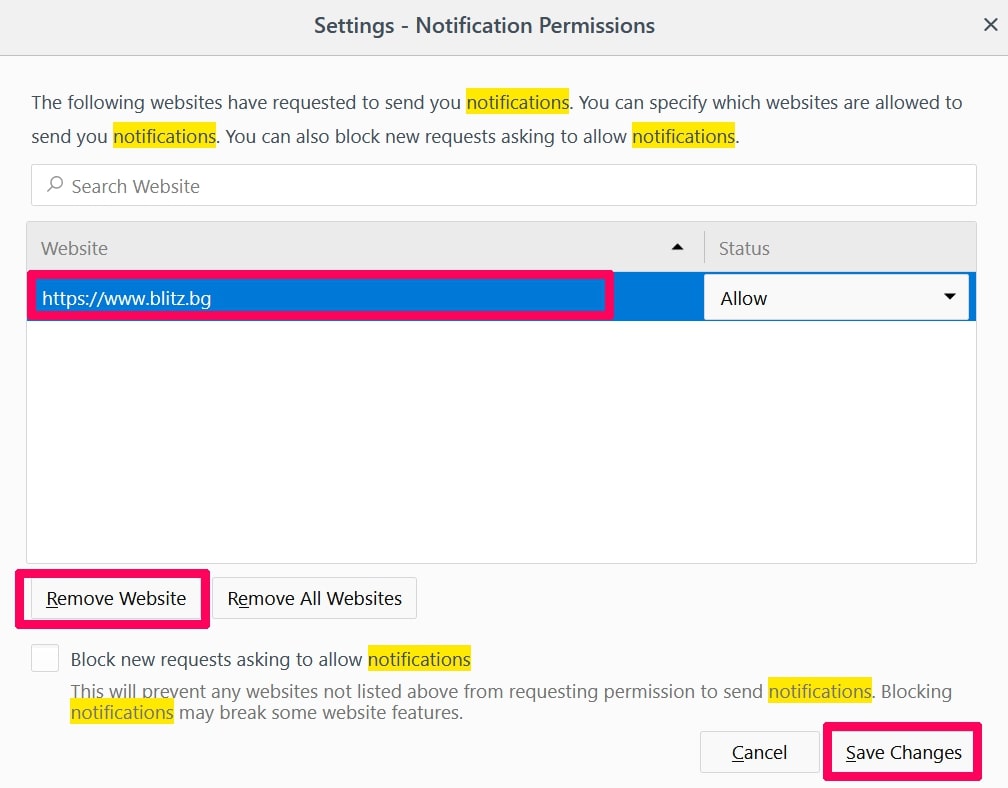
Step 3: Click “Remove” on any site you wish notifications gone and click “Save Changes”
Stop Push Notifications on Opera
Step 1: In Opera, press ALT+P to go to Settings.
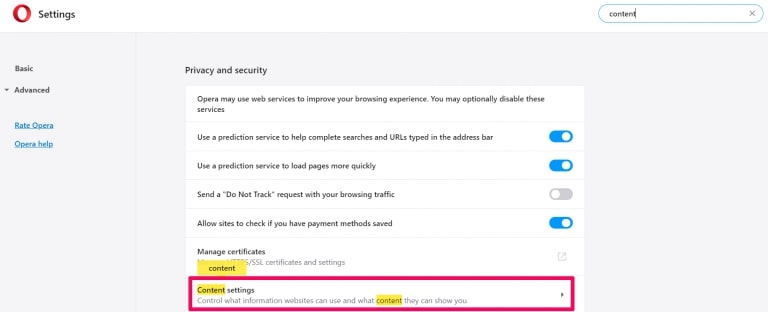
Step 2: In Setting search, type “Content” to go to Content Settings.
Step 3: Open Notifications:
Step 4: Do the same as you did with Google Chrome (explained below):
Eliminate Push Notifications on Safari
Step 1: Open Safari Preferences.
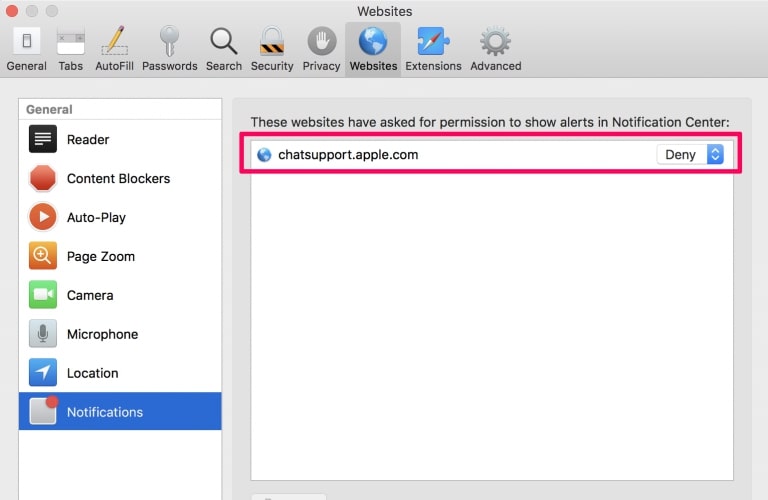
Step 2: Choose the domain from where you like push pop-ups gone and change to "Deny" from "Allow".
Nextgeeker.com-FAQ
What Is Nextgeeker.com?
The Nextgeeker.com threat is adware or browser redirect virus.
It may slow your computer down significantly and display advertisements. The main idea is for your information to likely get stolen or more ads to appear on your device.
The creators of such unwanted apps work with pay-per-click schemes to get your computer to visit risky or different types of websites that may generate them funds. This is why they do not even care what types of websites show up on the ads. This makes their unwanted software indirectly risky for your OS.
What Are the Symptoms of Nextgeeker.com?
There are several symptoms to look for when this particular threat and also unwanted apps in general are active:
Symptom #1: Your computer may become slow and have poor performance in general.
Symptom #2: You have toolbars, add-ons or extensions on your web browsers that you don't remember adding.
Symptom #3: You see all types of ads, like ad-supported search results, pop-ups and redirects to randomly appear.
Symptom #4: You see installed apps on your Mac running automatically and you do not remember installing them.
Symptom #5: You see suspicious processes running in your Task Manager.
If you see one or more of those symptoms, then security experts recommend that you check your computer for viruses.
What Types of Unwanted Programs Are There?
According to most malware researchers and cyber-security experts, the threats that can currently affect your device can be rogue antivirus software, adware, browser hijackers, clickers, fake optimizers and any forms of PUPs.
What to Do If I Have a "virus" like Nextgeeker.com?
With few simple actions. First and foremost, it is imperative that you follow these steps:
Step 1: Find a safe computer and connect it to another network, not the one that your Mac was infected in.
Step 2: Change all of your passwords, starting from your email passwords.
Step 3: Enable two-factor authentication for protection of your important accounts.
Step 4: Call your bank to change your credit card details (secret code, etc.) if you have saved your credit card for online shopping or have done online activities with your card.
Step 5: Make sure to call your ISP (Internet provider or carrier) and ask them to change your IP address.
Step 6: Change your Wi-Fi password.
Step 7: (Optional): Make sure to scan all of the devices connected to your network for viruses and repeat these steps for them if they are affected.
Step 8: Install anti-malware software with real-time protection on every device you have.
Step 9: Try not to download software from sites you know nothing about and stay away from low-reputation websites in general.
If you follow these recommendations, your network and all devices will become significantly more secure against any threats or information invasive software and be virus free and protected in the future too.
How Does Nextgeeker.com Work?
Once installed, Nextgeeker.com can collect data using trackers. This data is about your web browsing habits, such as the websites you visit and the search terms you use. It is then used to target you with ads or to sell your information to third parties.
Nextgeeker.com can also download other malicious software onto your computer, such as viruses and spyware, which can be used to steal your personal information and show risky ads, that may redirect to virus sites or scams.
Is Nextgeeker.com Malware?
The truth is that PUPs (adware, browser hijackers) are not viruses, but may be just as dangerous since they may show you and redirect you to malware websites and scam pages.
Many security experts classify potentially unwanted programs as malware. This is because of the unwanted effects that PUPs can cause, such as displaying intrusive ads and collecting user data without the user’s knowledge or consent.
About the Nextgeeker.com Research
The content we publish on SensorsTechForum.com, this Nextgeeker.com how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific, adware-related problem, and restore your browser and computer system.
How did we conduct the research on Nextgeeker.com?
Please note that our research is based on independent investigation. We are in contact with independent security researchers, thanks to which we receive daily updates on the latest malware, adware, and browser hijacker definitions.
Furthermore, the research behind the Nextgeeker.com threat is backed with VirusTotal.
To better understand this online threat, please refer to the following articles which provide knowledgeable details.


