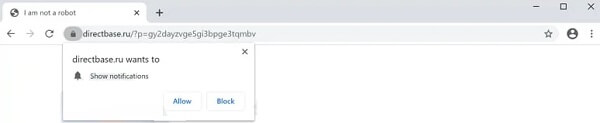
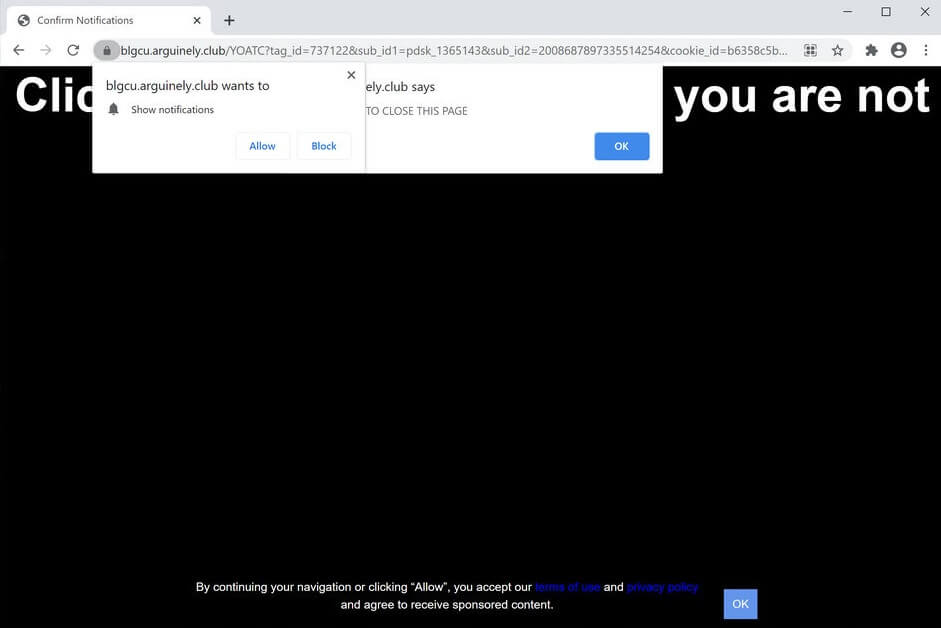
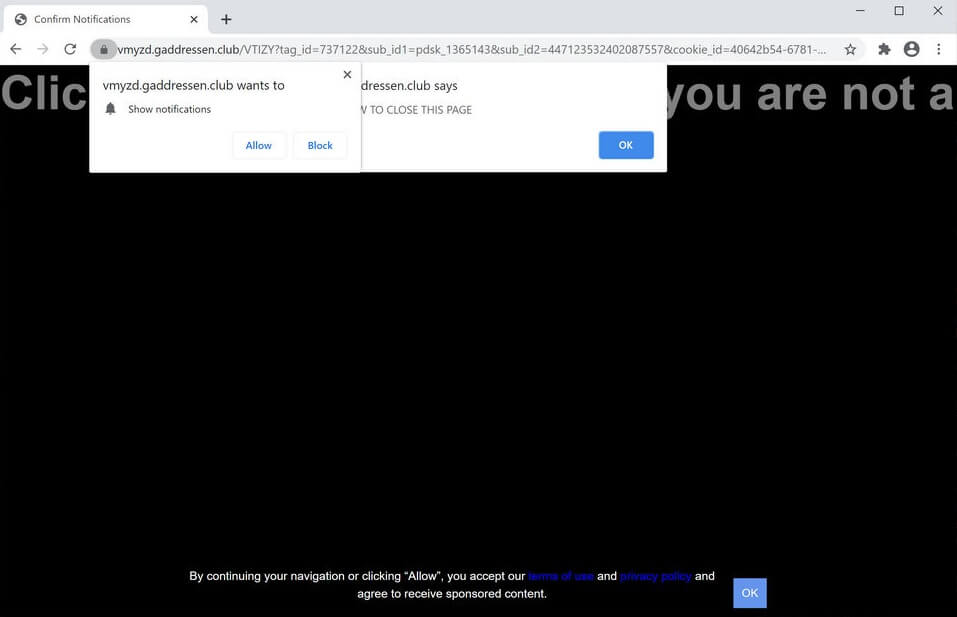
Remove Product Connecter Browser Redirect
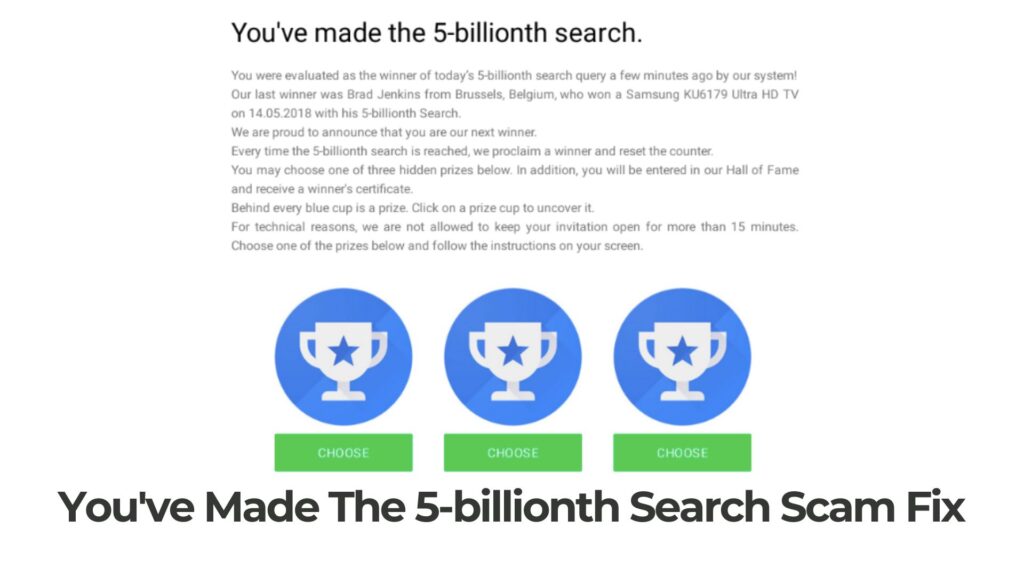
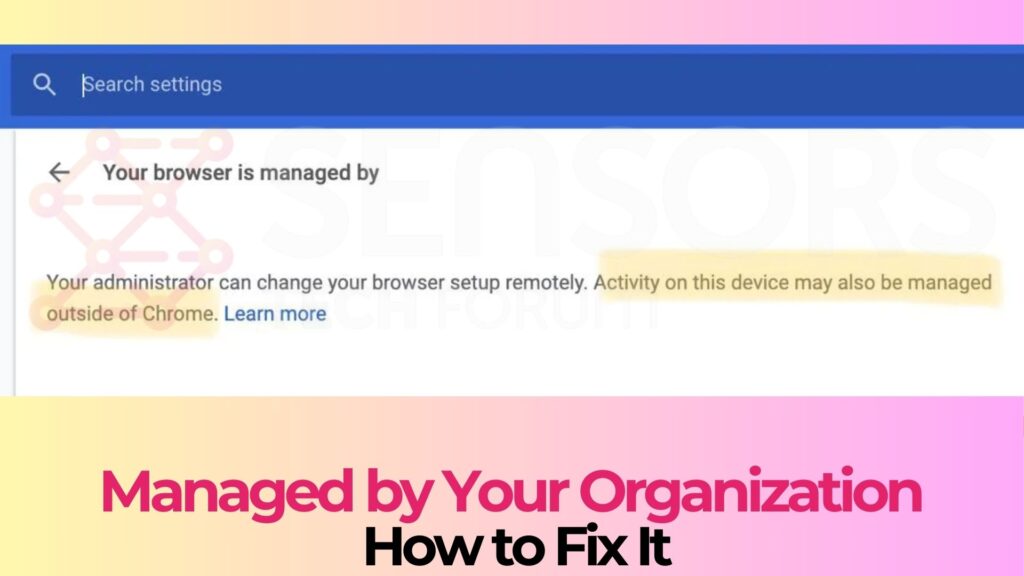
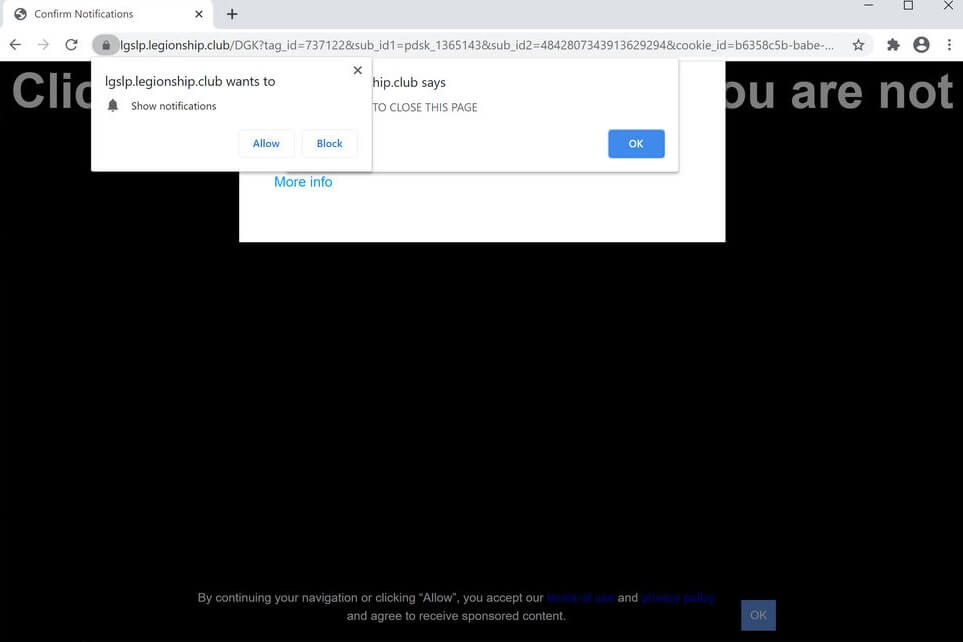
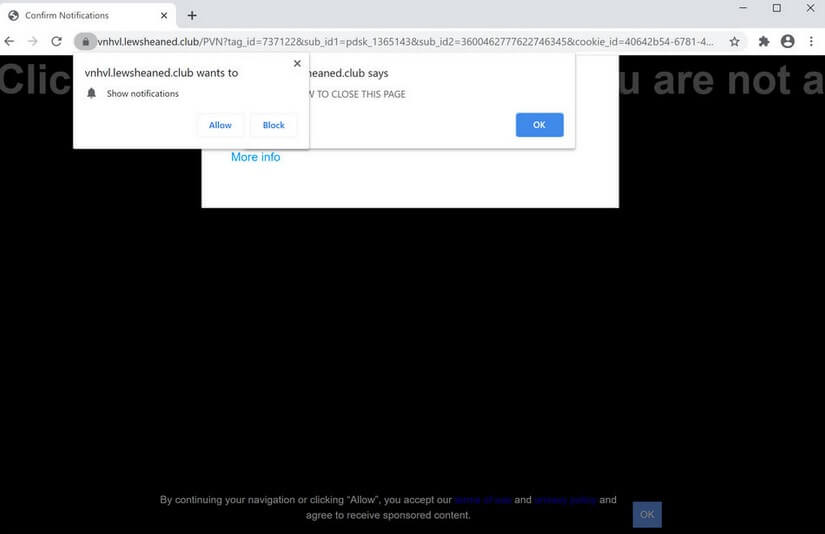
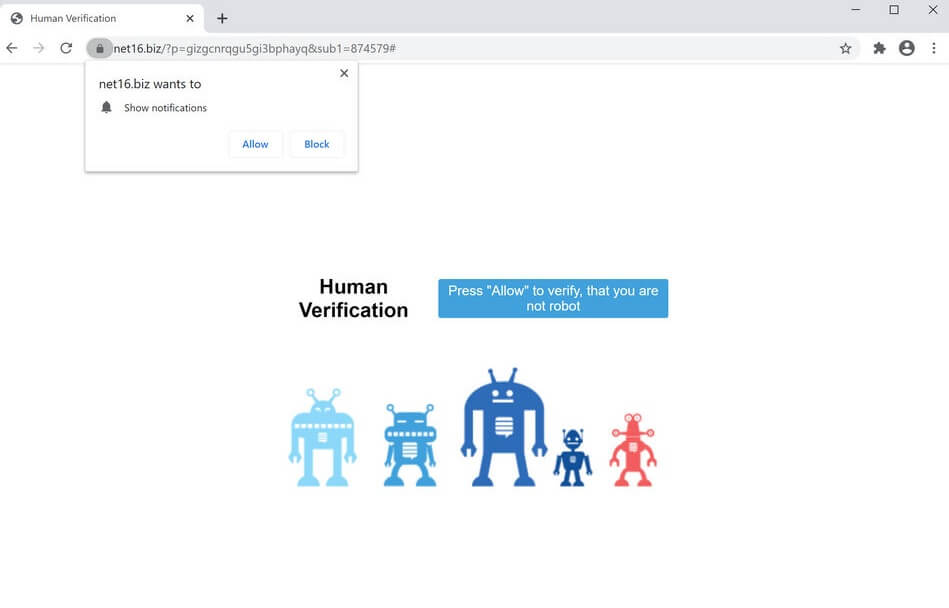
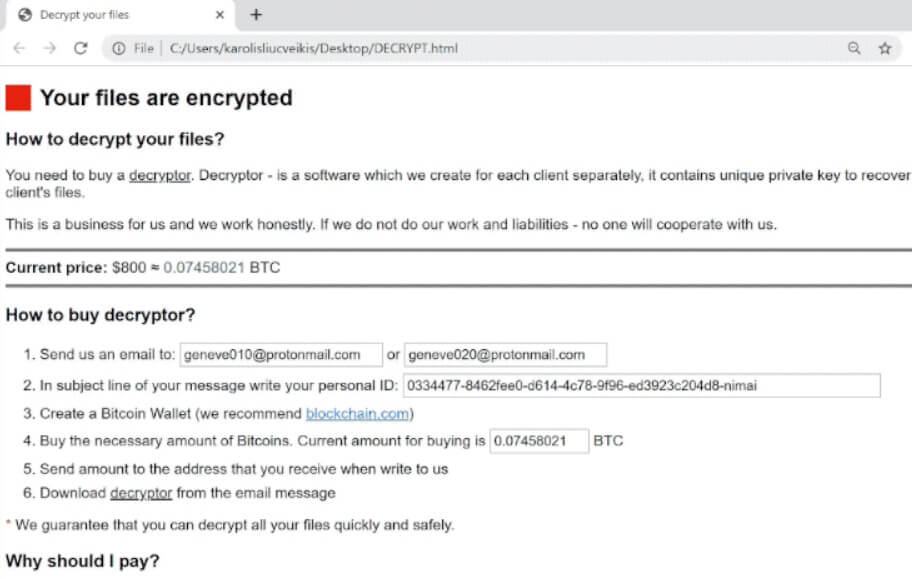
Seeing Product Connecter Redirect in your browsers? Product Connecter is a suspicious domain as it can redirect and even trigger malicious actions in your browsers. Product Connecter can push advertisements and redirects, but can also land you on a page…