.cizer Virus Files (Ransomware) – How to Remove
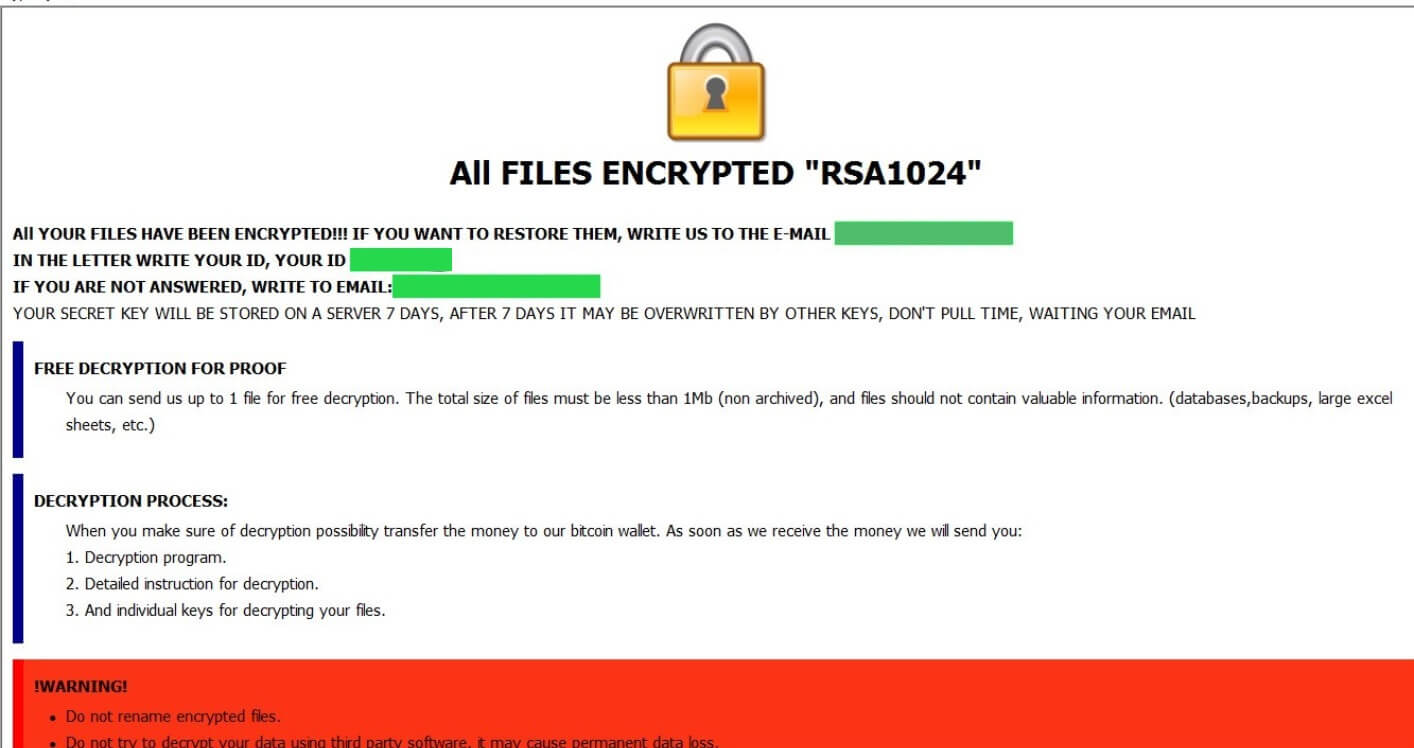
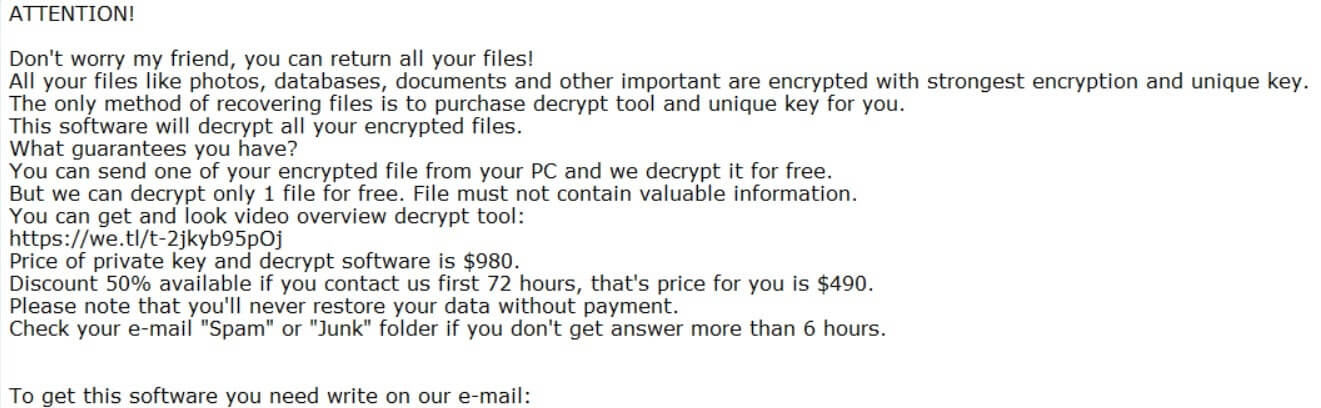
What is .cizer ransomware? What are .cizer virus files? How to remove .cizer ransomware from your computer? How to try and restore .cizer encrypted files? Yet another ransomware virus, using the .cizer file extension has been spotted. The virus aims…