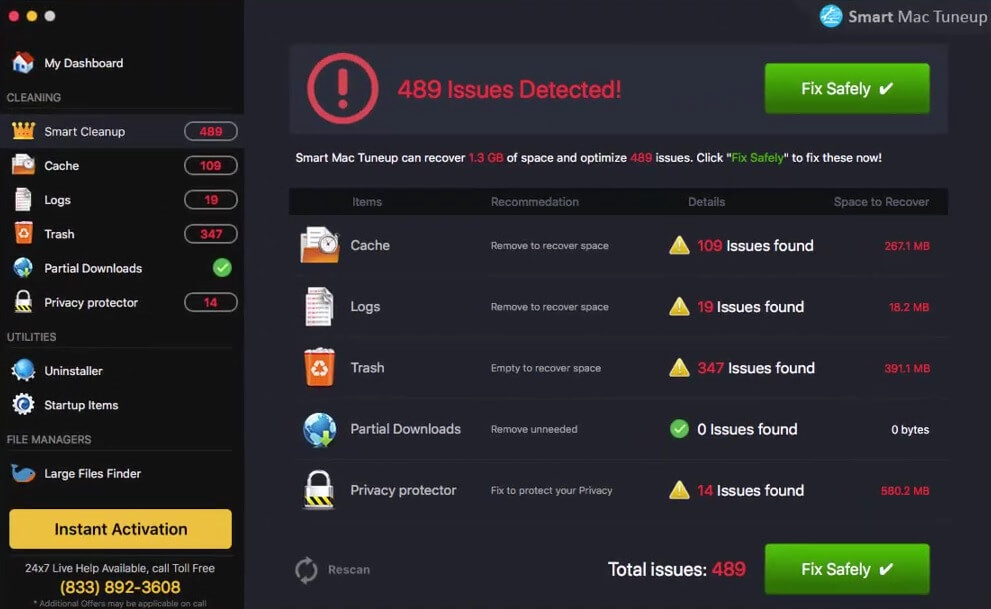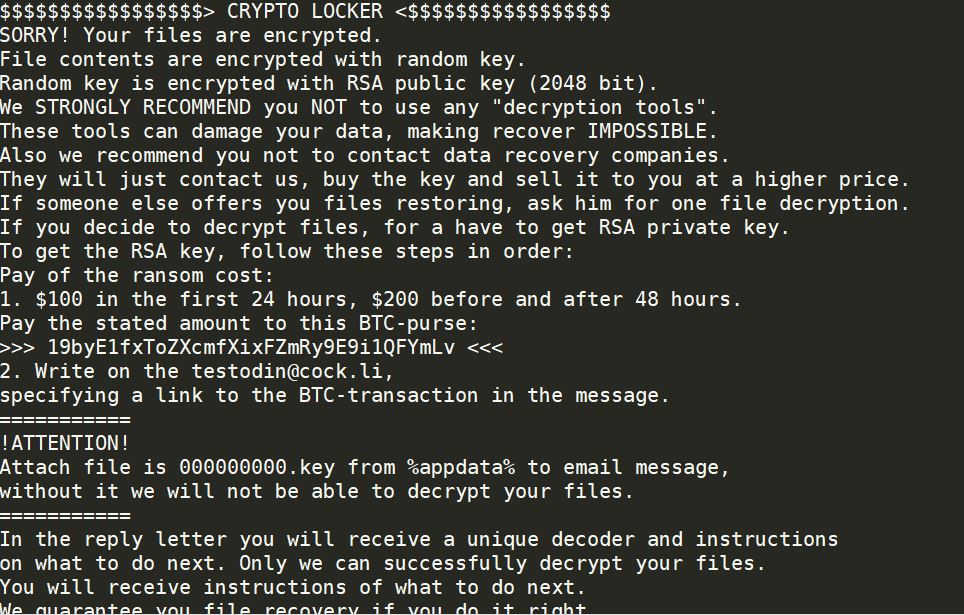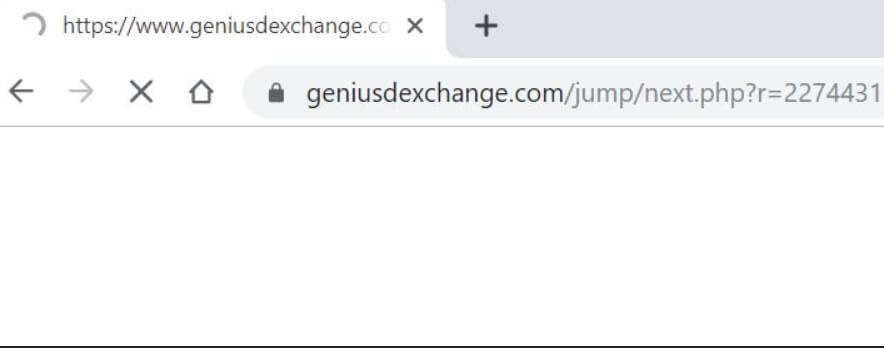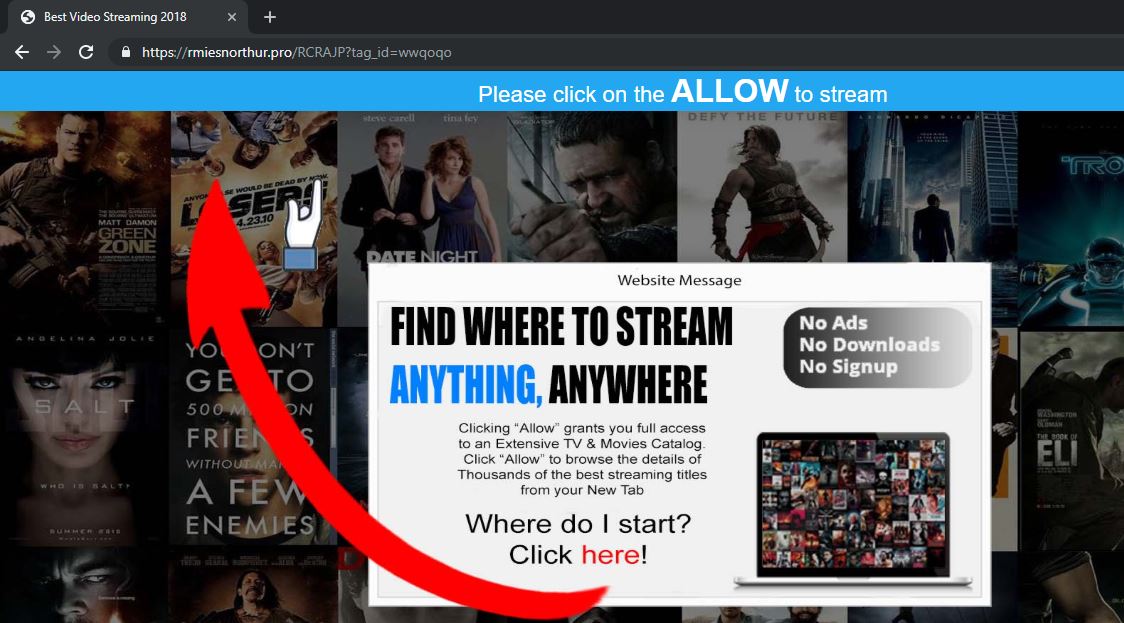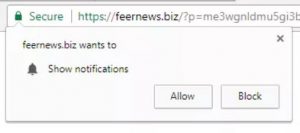
Feernews.biz Show Notifications “Virus” – Remove It
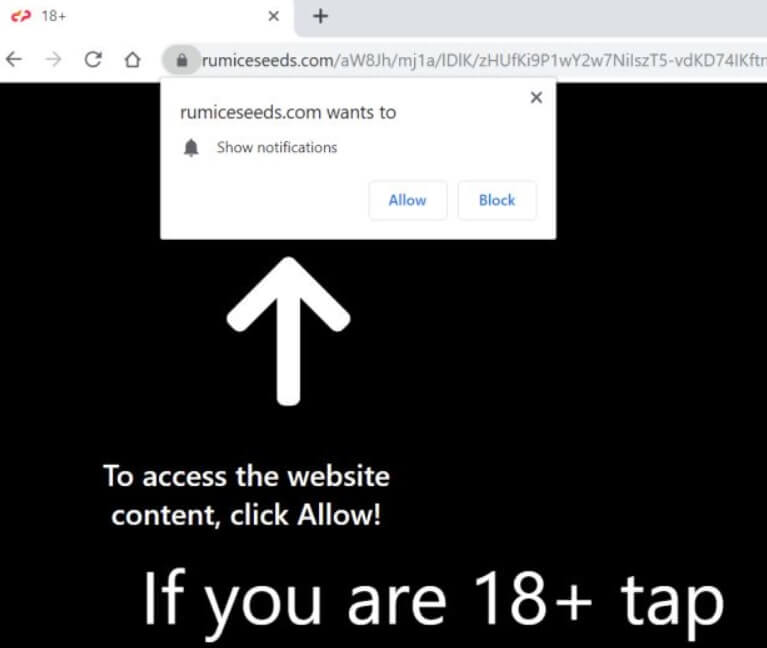
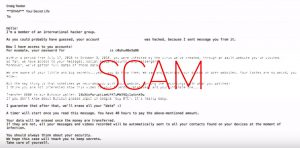
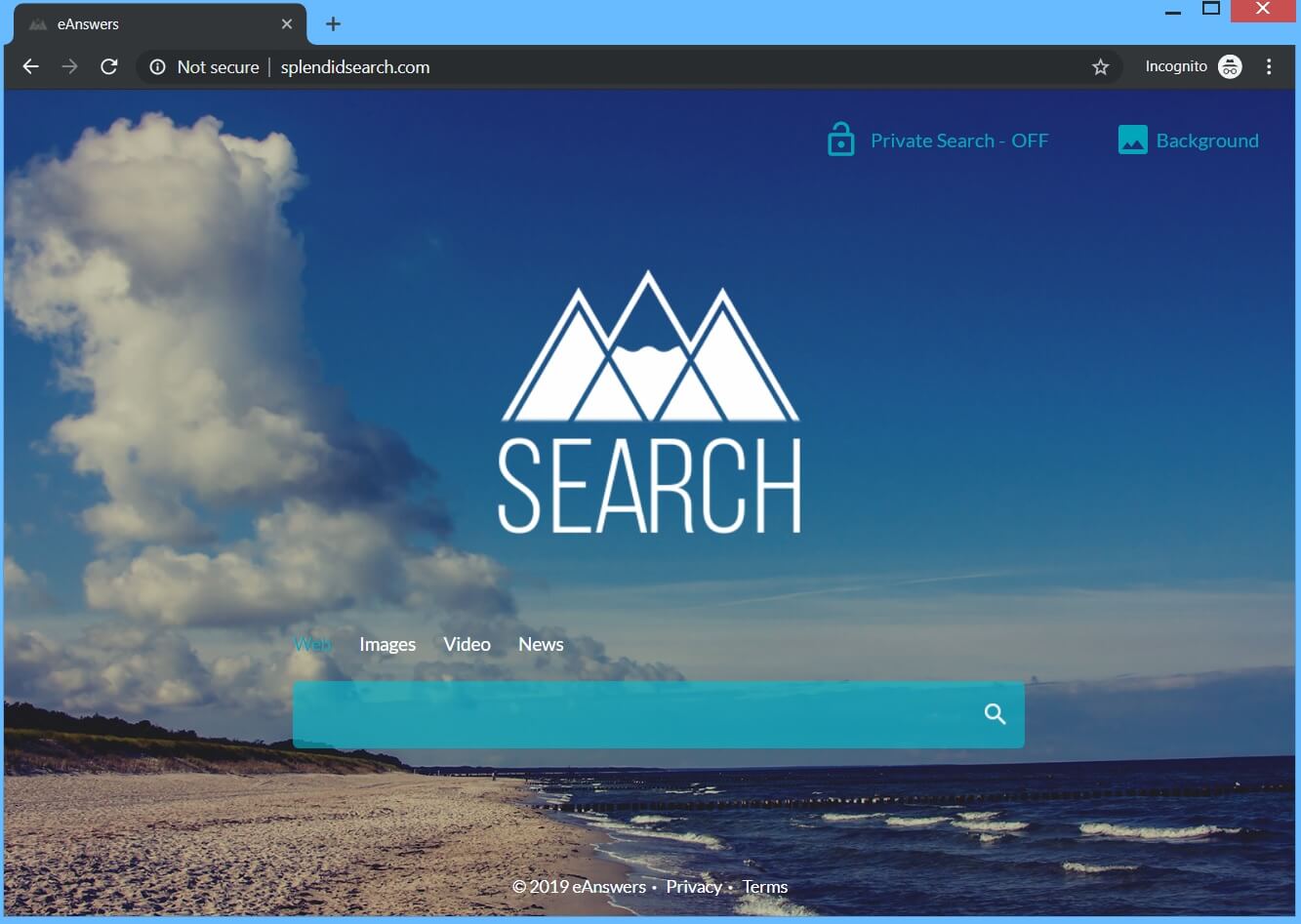
What is Feernews.biz? What are Feernews.biz notifications? How to remove Feernews.biz notifications virus from your computer? The Feernews.biz is a domain, that requests users to accept Push Notifications on their browsers. These forms of notifications may be appear as unwanted…