Remove iyfsearch.com Redirect
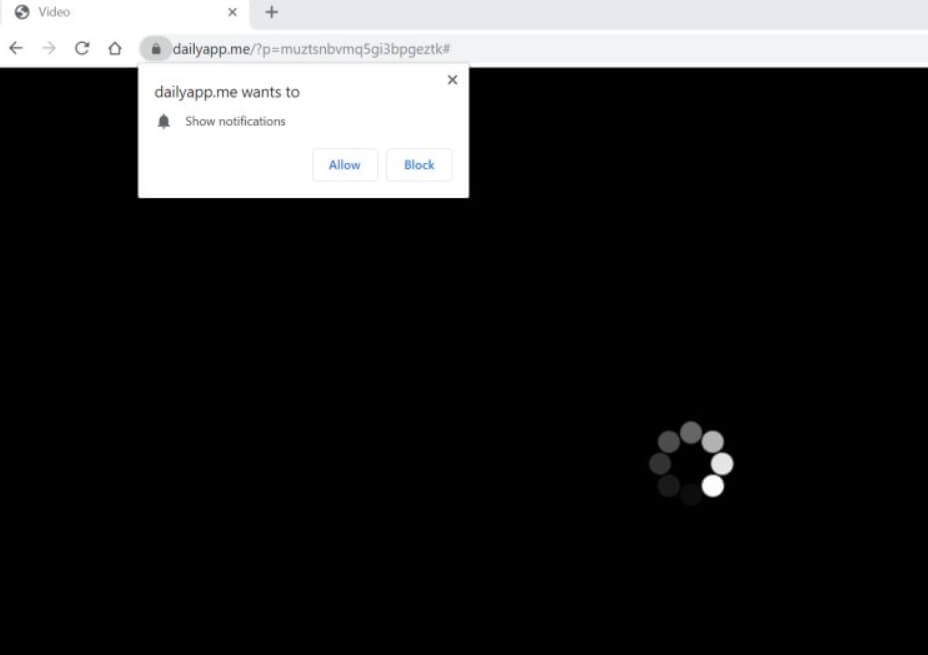
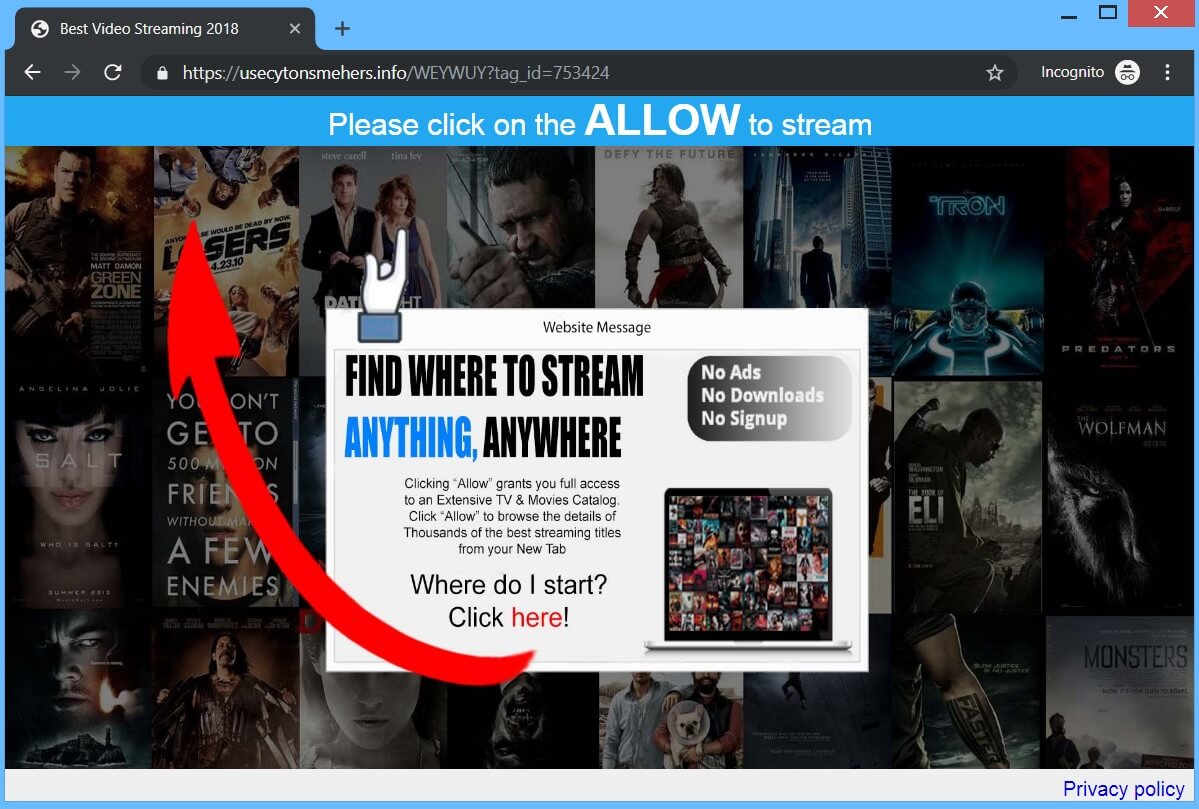
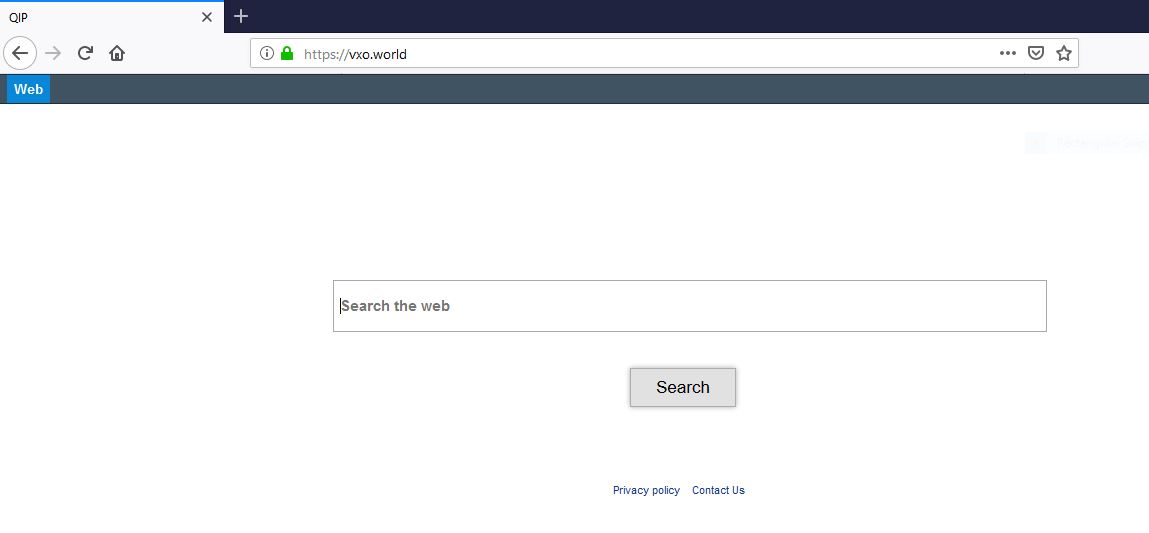
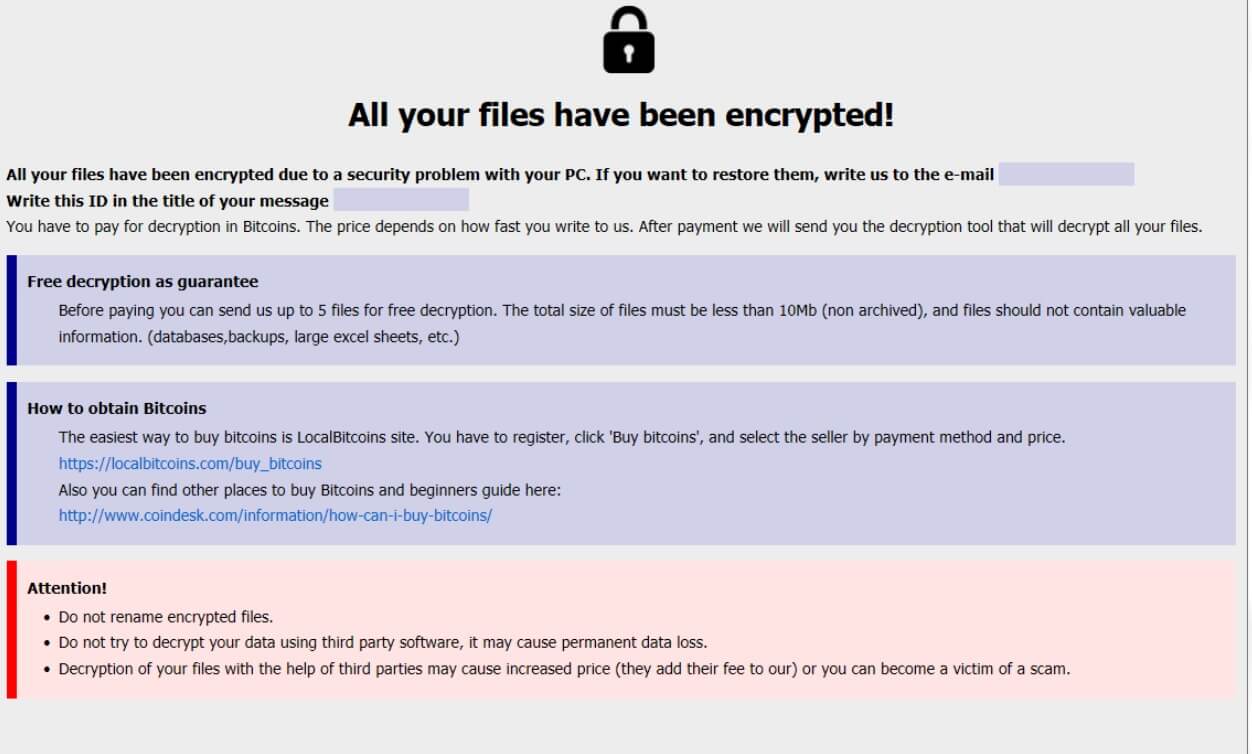
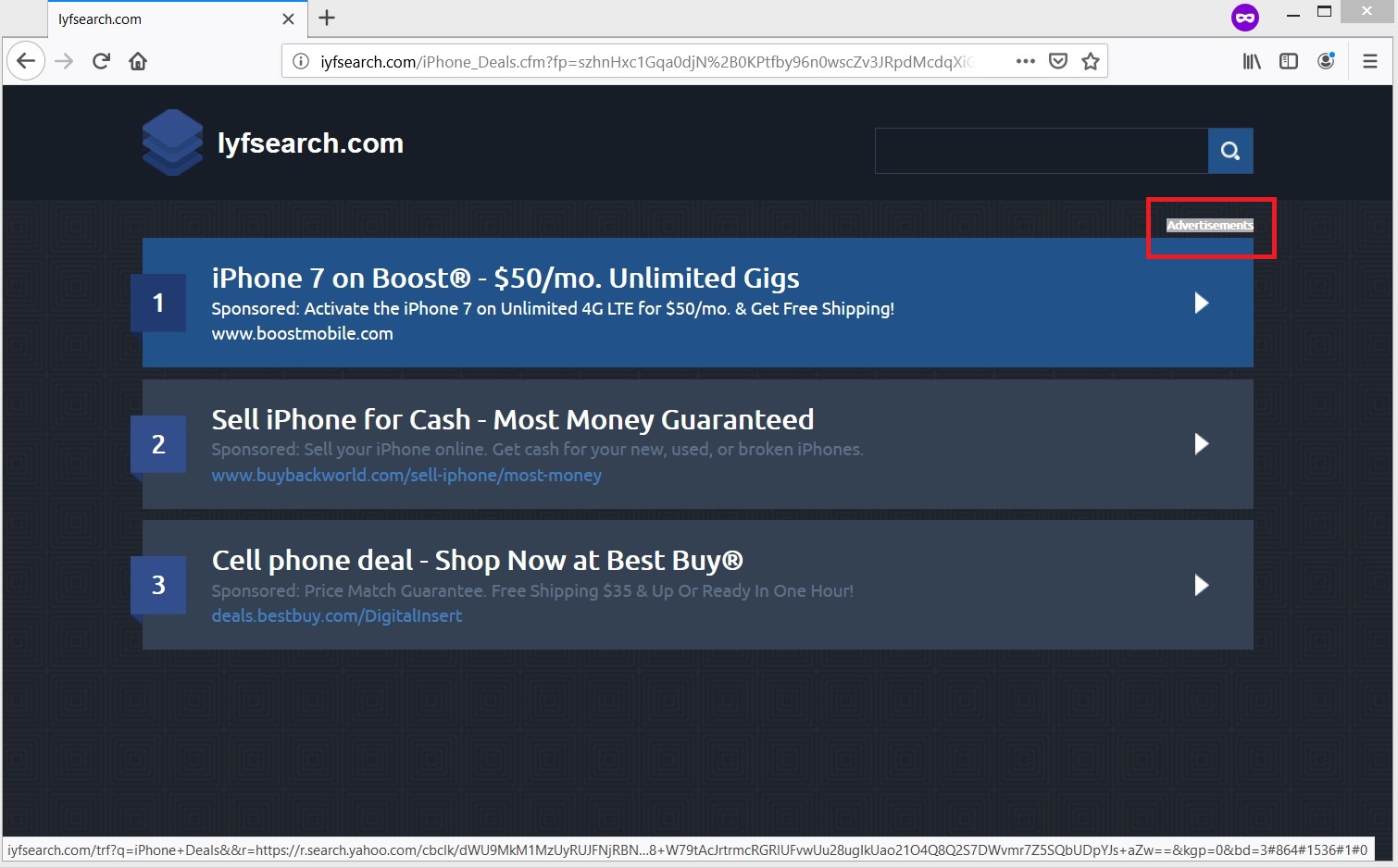
This article presents information about the annoying iyfsearch.com browser redirect and provides help for its complete removal from the affected system. The website iyfsearch.com is as presented an online platform that presents software and product promotions. It is categorized as…