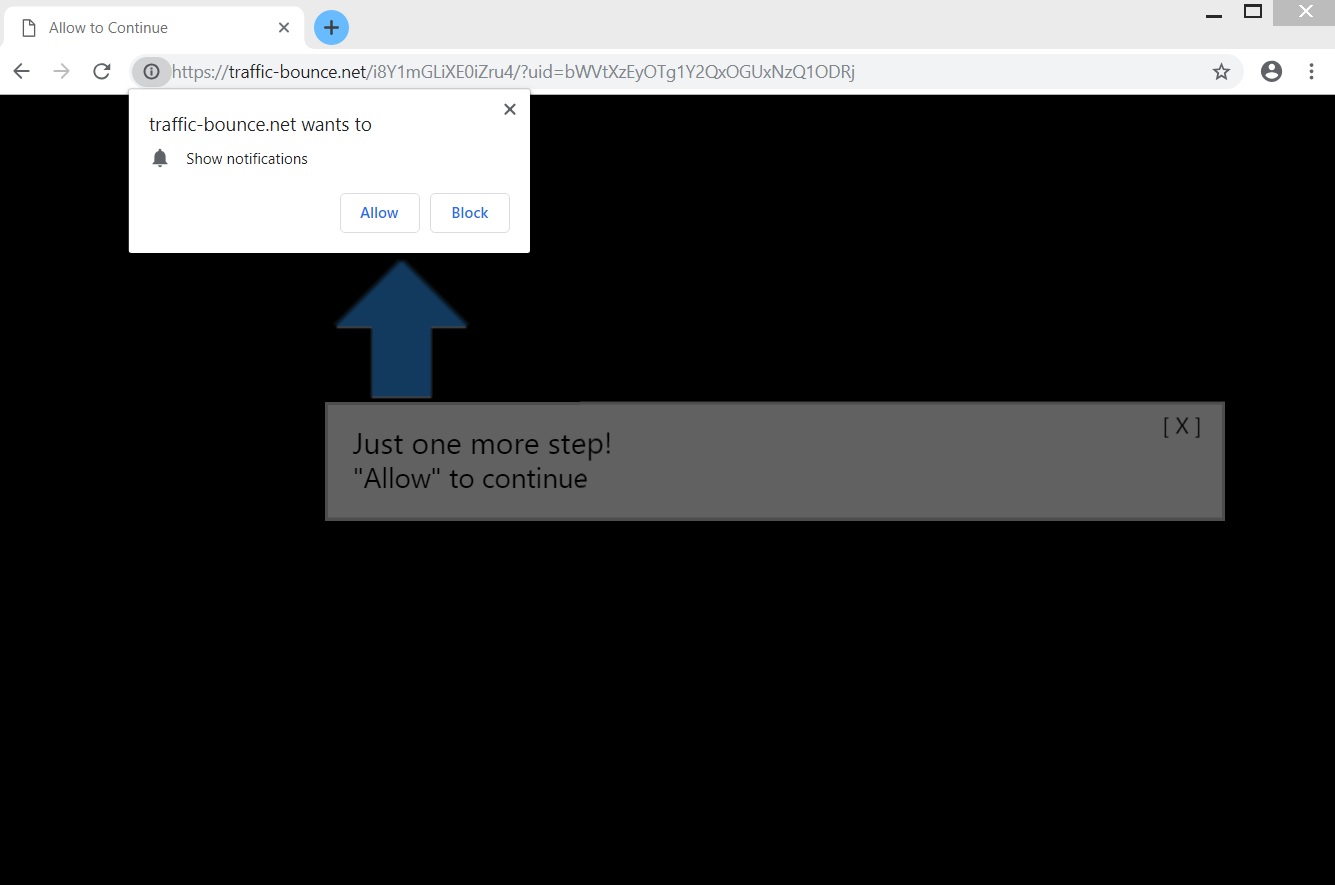
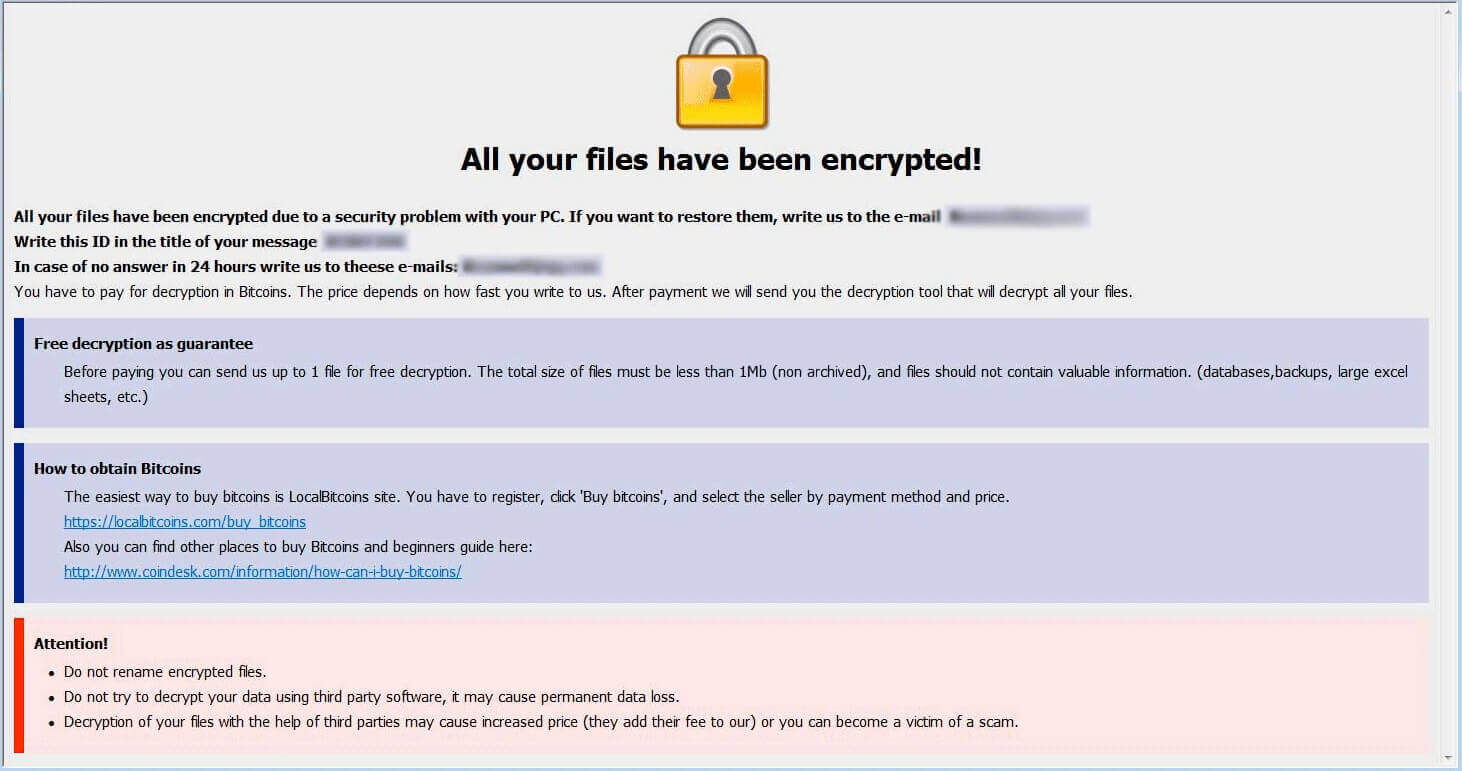
.zoro Files Virus (Scarab) – How to Remove
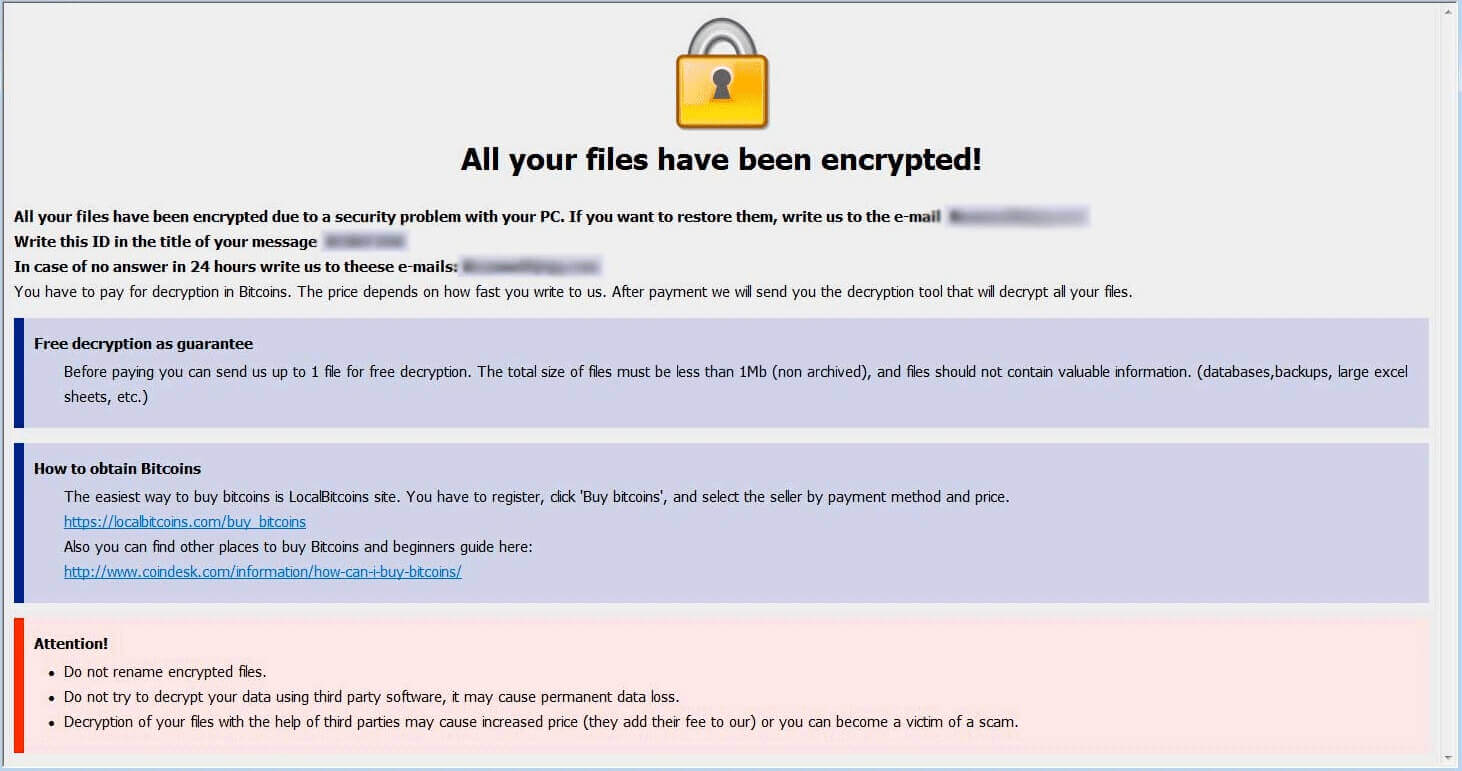
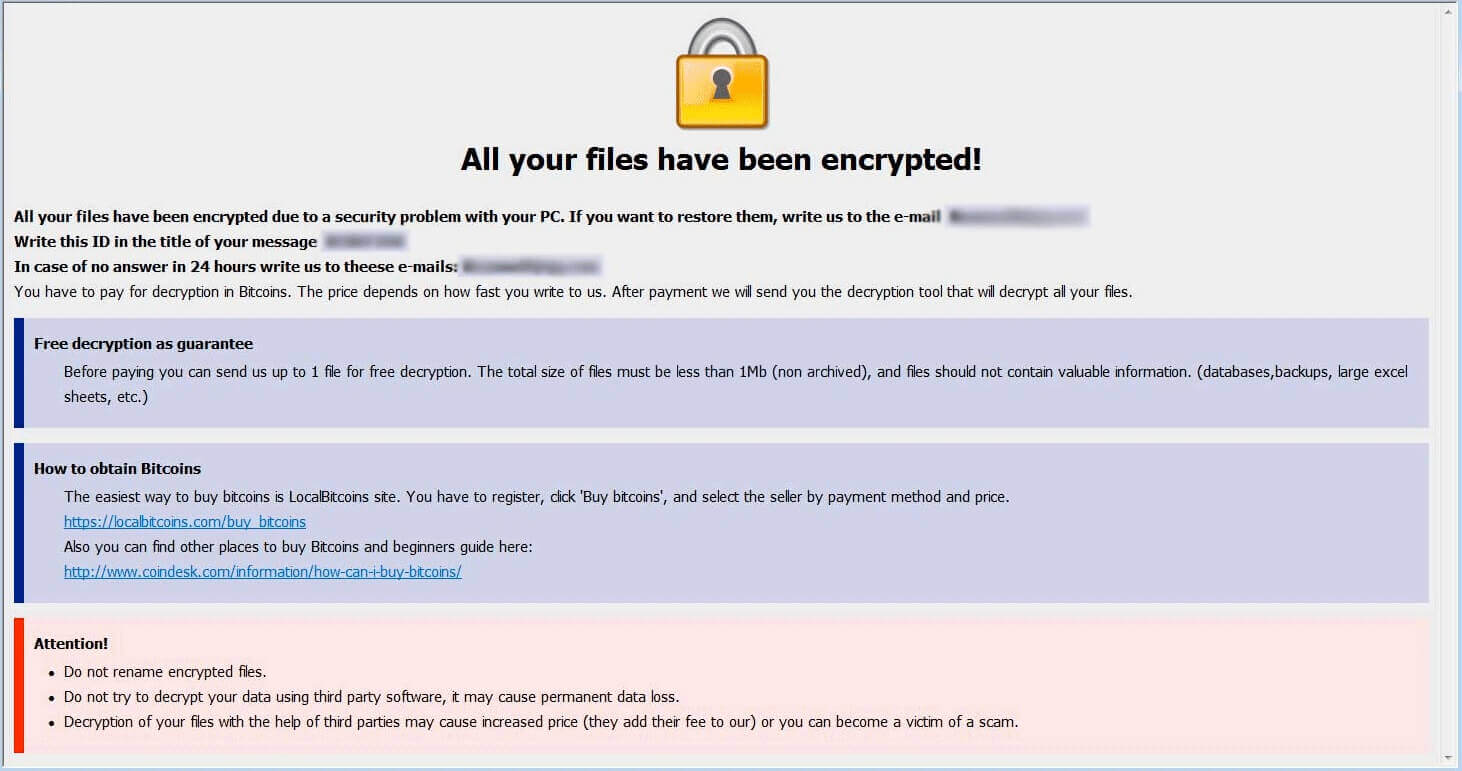
Why did .zoro Files Virus encrypt my files? What is Scarab ransomware? Can I get files encrypted by the .zoro Files Virus restored? .zoro Files Virus belongs to the Scarab family of cryptoviruses which aim to encrypt your files and…







![.[SSSDKVNSDFITD] Ransomware — How to Remove It .[SSSDKVNSDFITD] Ransomware virus remove](https://cdn.sensorstechforum.com/wp-content/uploads/2019/05/SSSDKVNSDFITD-ransomware-image-sensorstechforum-com.jpg)