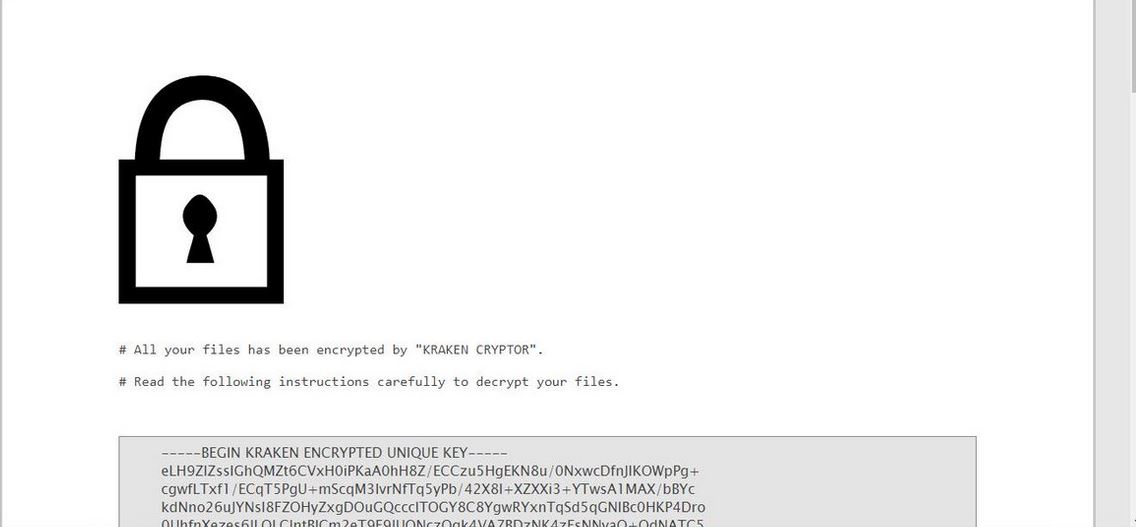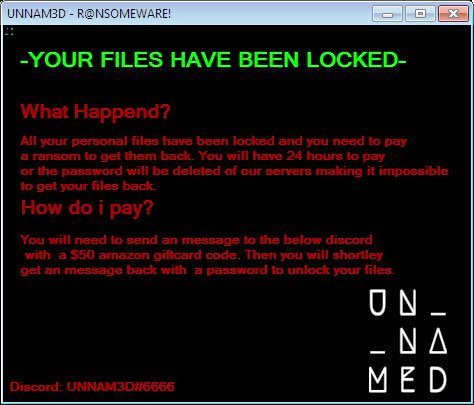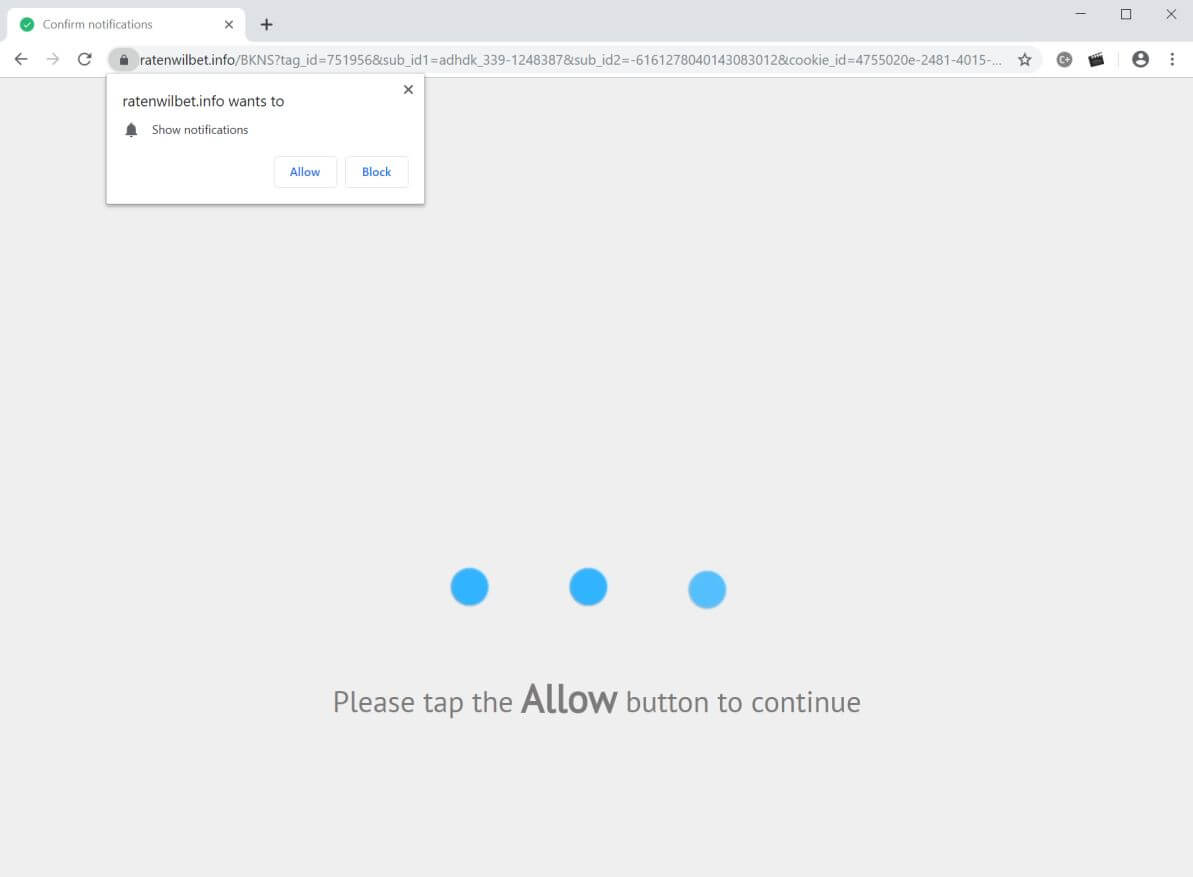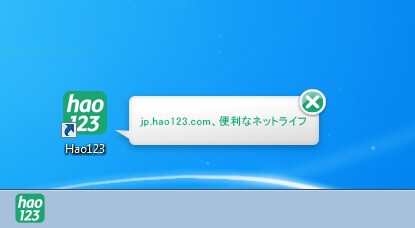
Hao123.com Browser Hijacker – Remove It
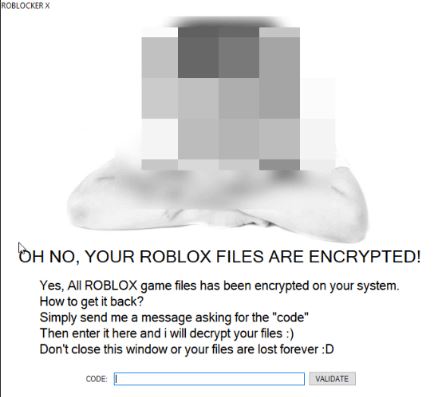
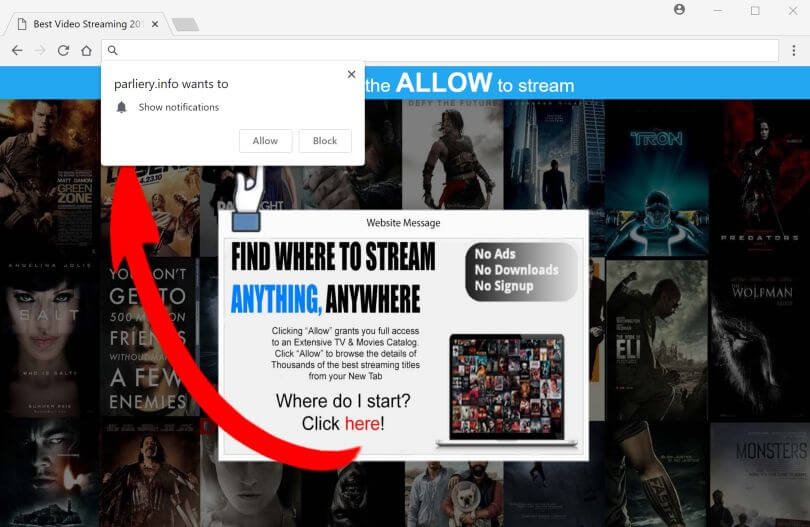
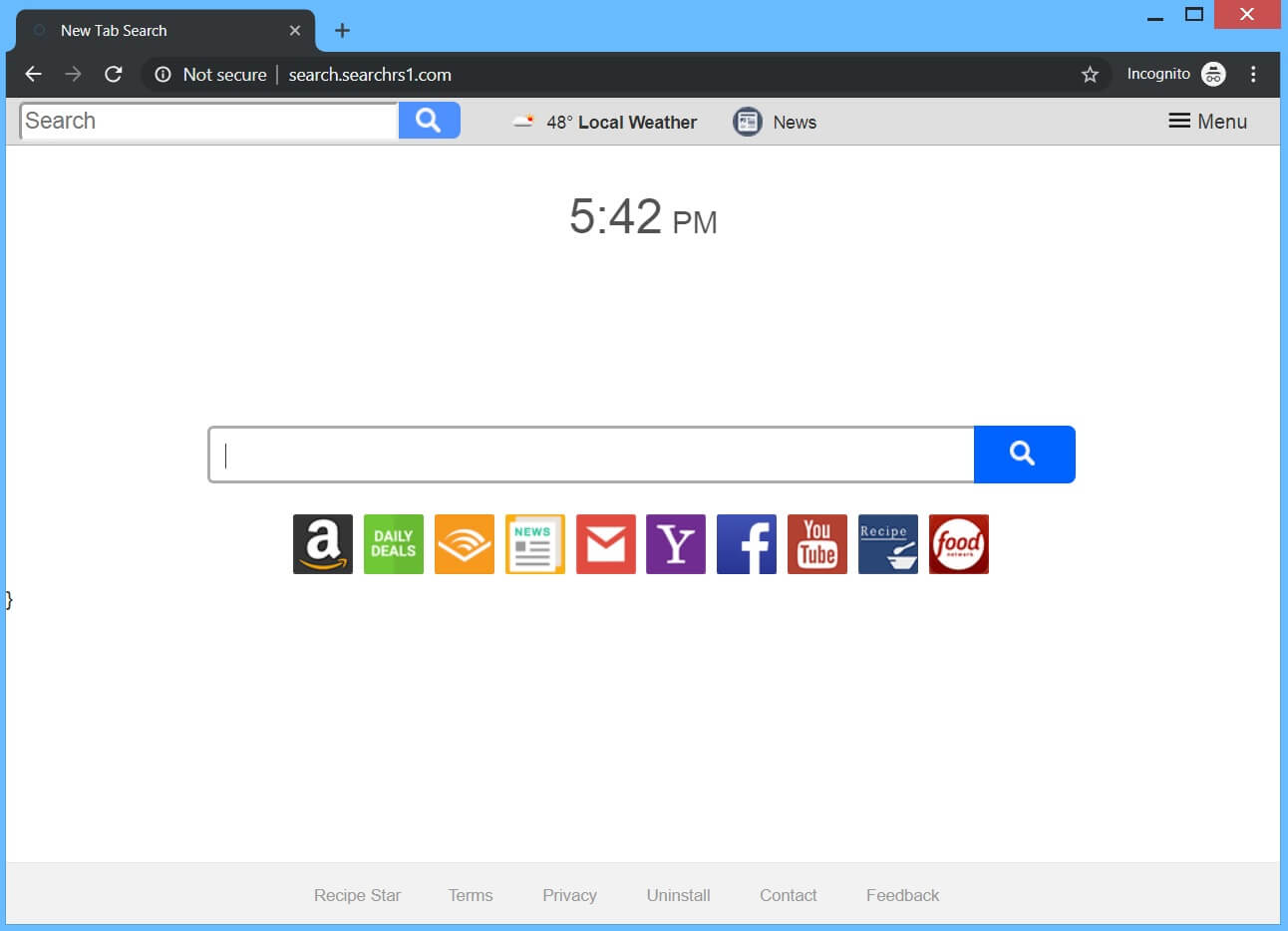
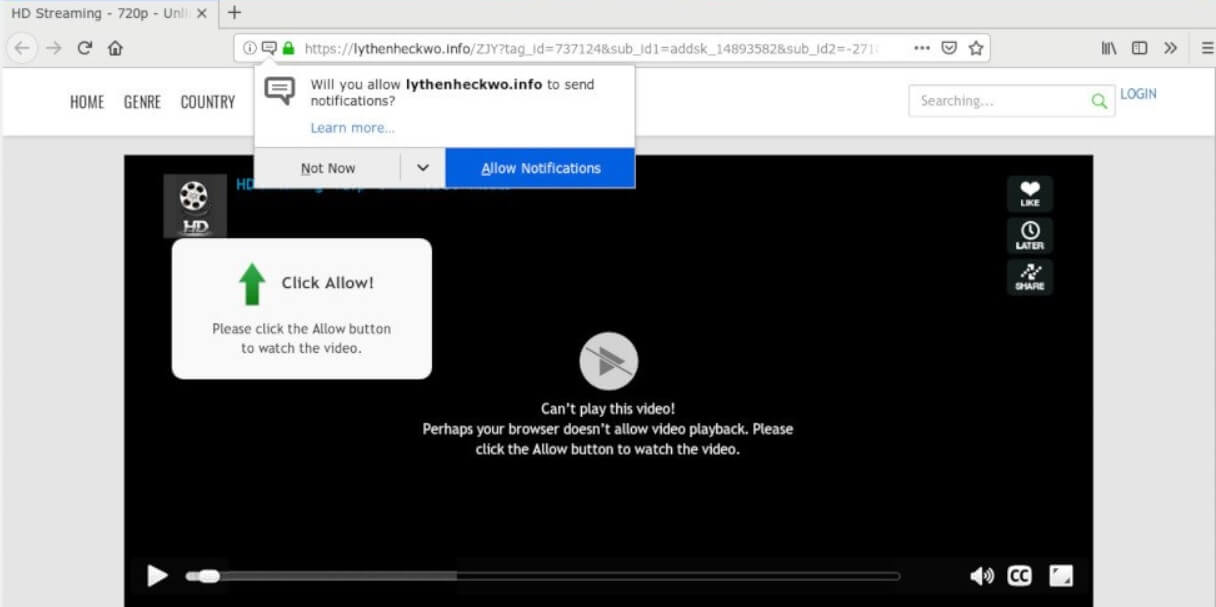
What is Hao123.com? Does Hao123.com hijack your browser? What ads does Hao123.com show? Does Hao123.com redirect you? Hao123.com is the main page that will show up when you open a new tab page if you have the related browser hijacker…