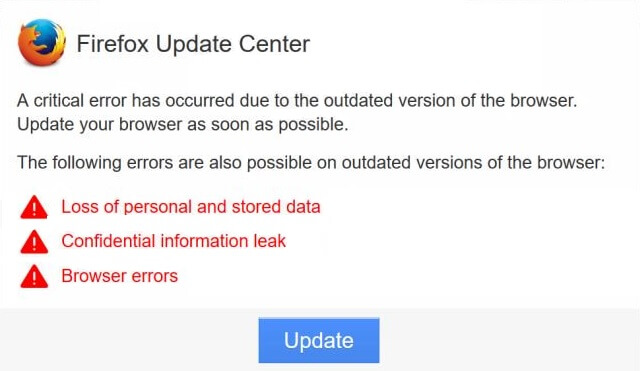
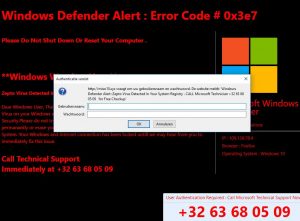
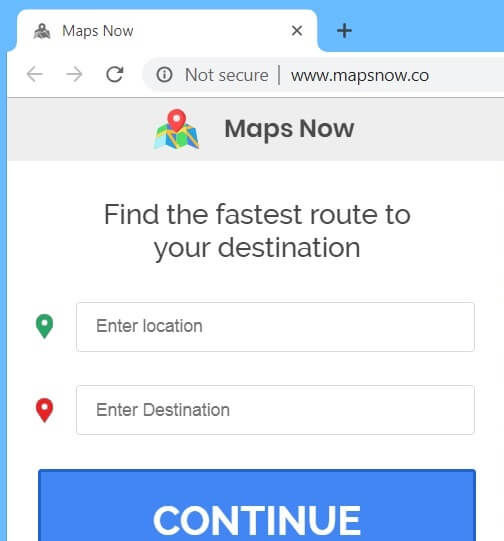
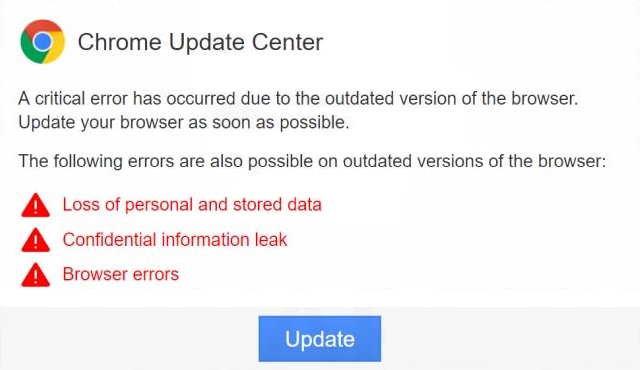
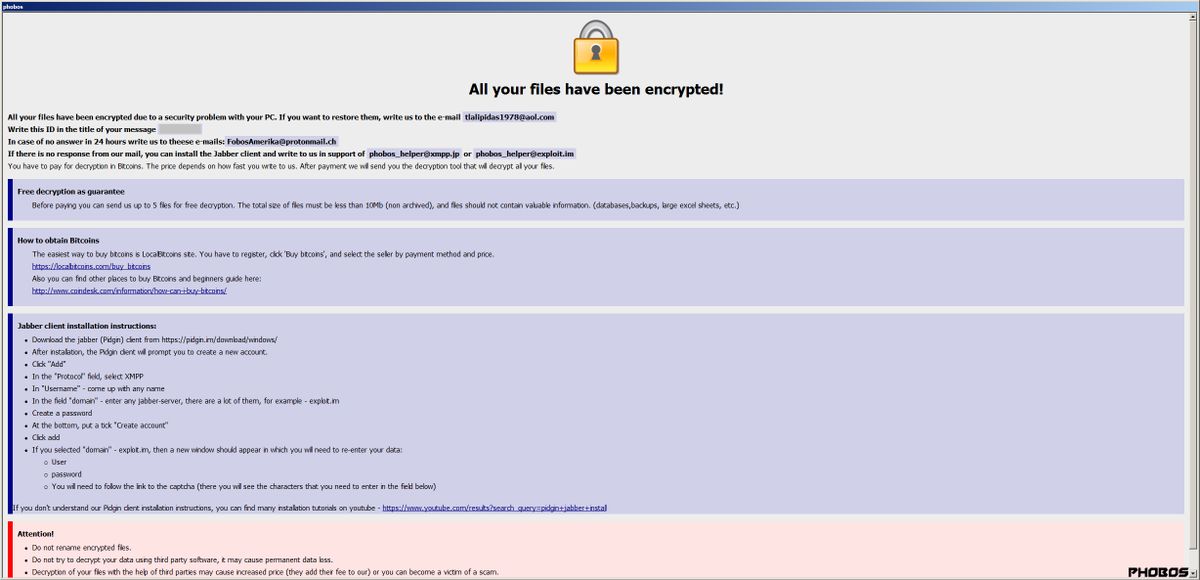
.Neptune Files Virus – How to Remove It
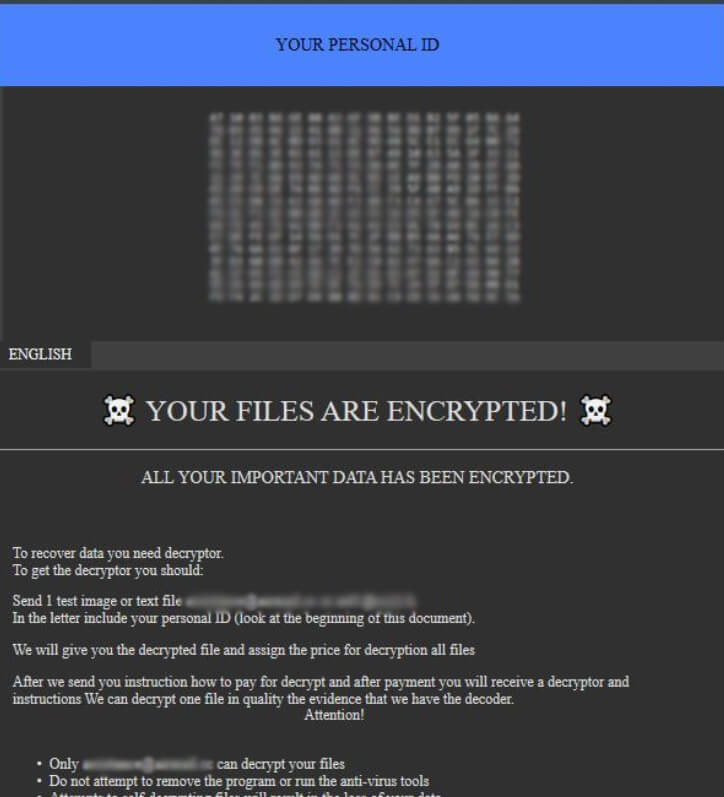
In this article, you will find more information about .Neptune files virus as well as a step-by-step guide on how to remove malicious files from an infected system and how to potentially recover files encrypted by this ransomware. The so-called…