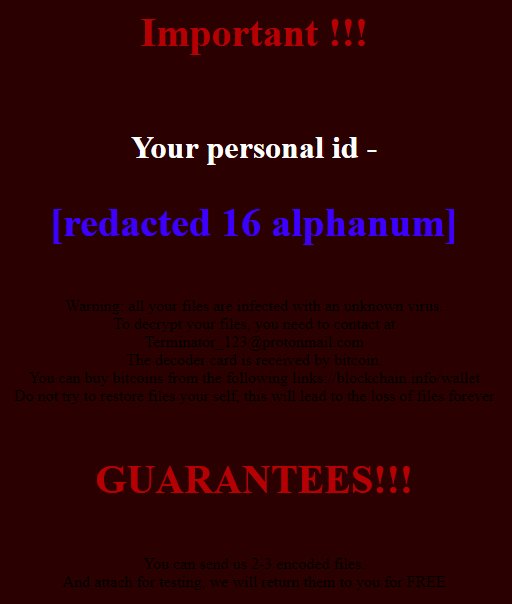
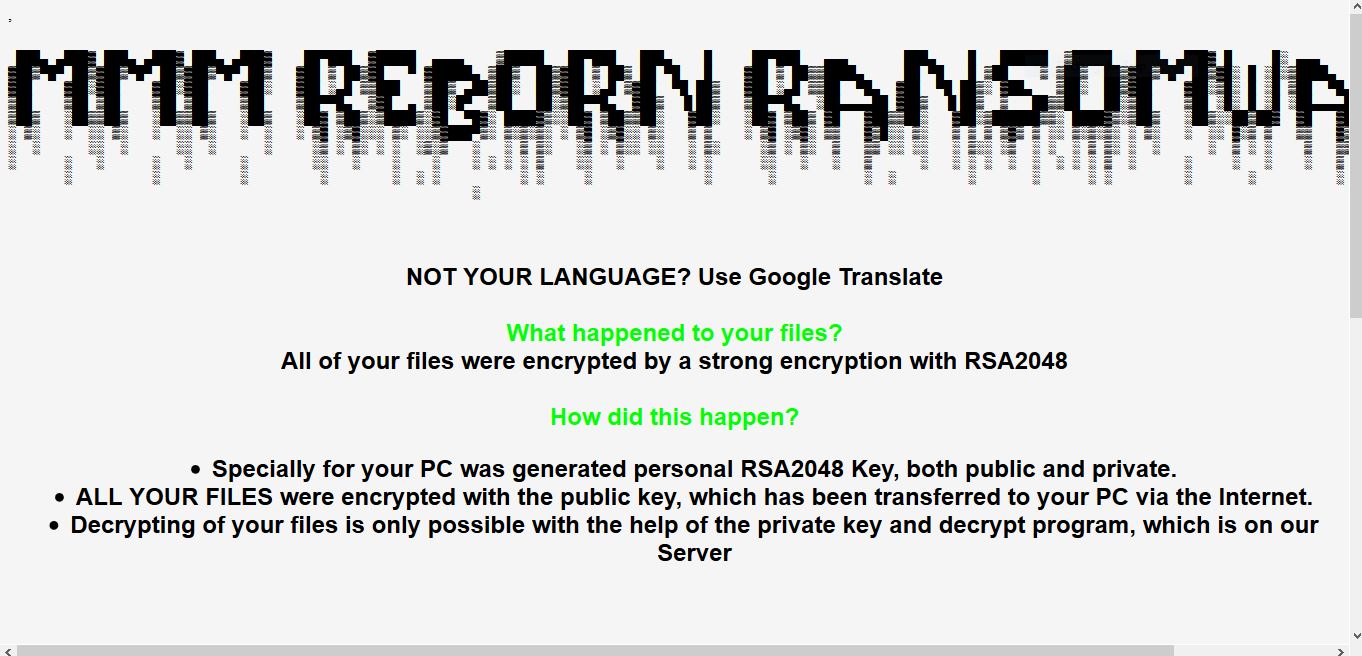
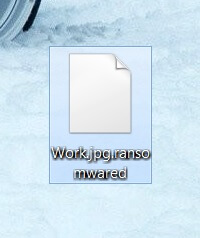
.bizer Files Virus (Dharma) – How to Remove
This article will help you remove the latest version of the Dharma ransomware virus and show you how you can try to possibly restore files encrypted with the .bizer extension. Dharma ransomware authors keep on building new variants of their…