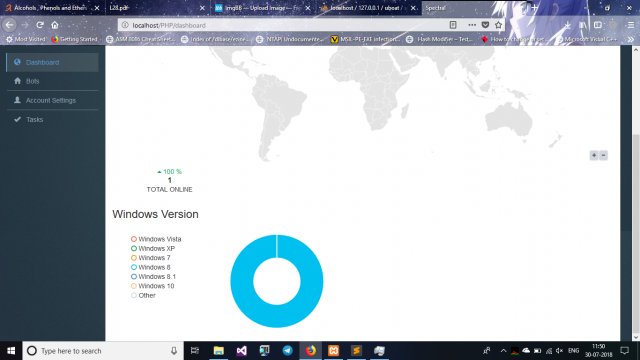
Mobile PoS Vulnerabilities Impact Paypal, Square, SumUp
An alarming discovery was recently made during the Black Hat conference held in Las Vegas. Security researchers from Positive Technologies reported that vulnerabilities in mPOS (mobile Point-of-Sale) machines allow attackers to take over customer accounts and steal credit card data.…


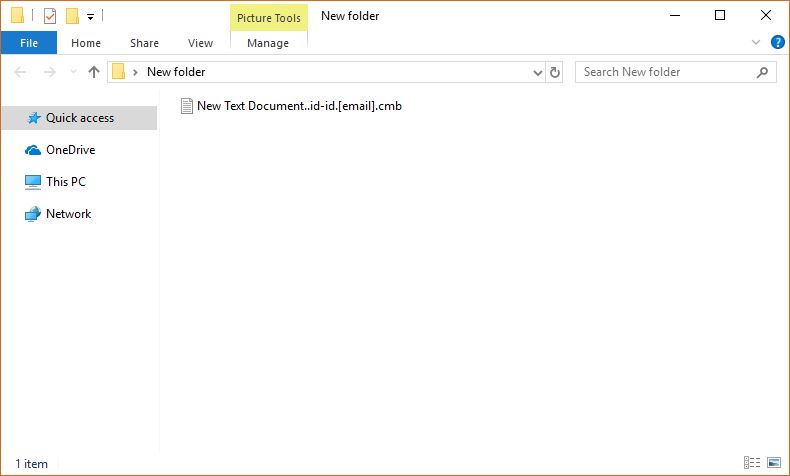

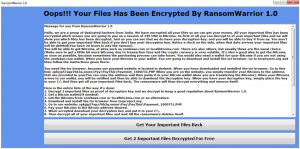







![Remove Yourencrypter@protonmail.ch Virus Infections Yourencrypter@protonmail.ch Virus image ransomware note Yourencrypter@protonmail.ch.[random ext] extension](https://cdn.sensorstechforum.com/wp-content/uploads/2018/08/Yourencrypter@protonmail.ch-virus-image-sensorstechforum-com.jpg)