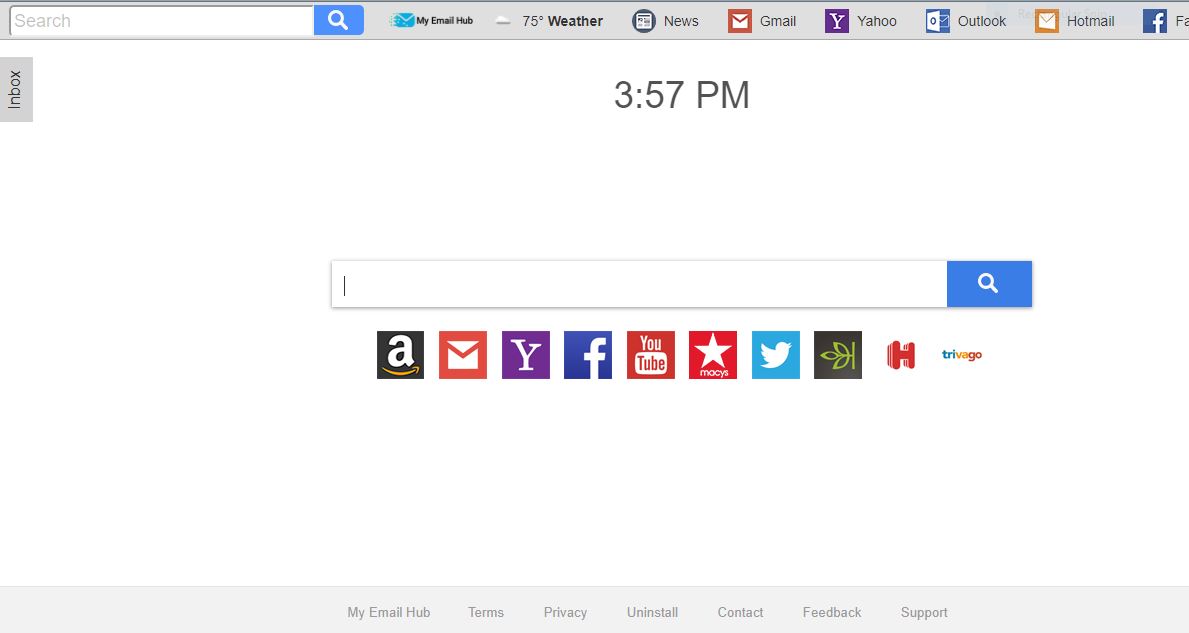
Remove My Email Hub Redirect and Restore Your Browser
What Is My Email Hub? My Email Hub is a suspicious browser extension that can be used for browser-hijacking purposes. Interaction with it can compromise your personal details. Also note that My Email Hub may cause redirects in your browser…



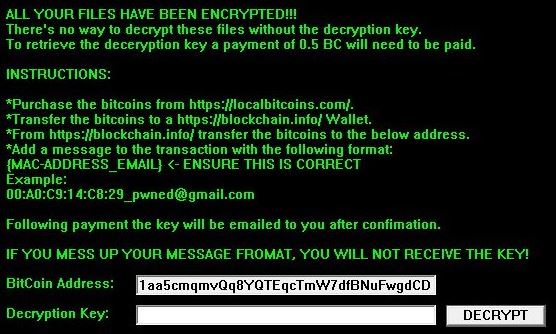








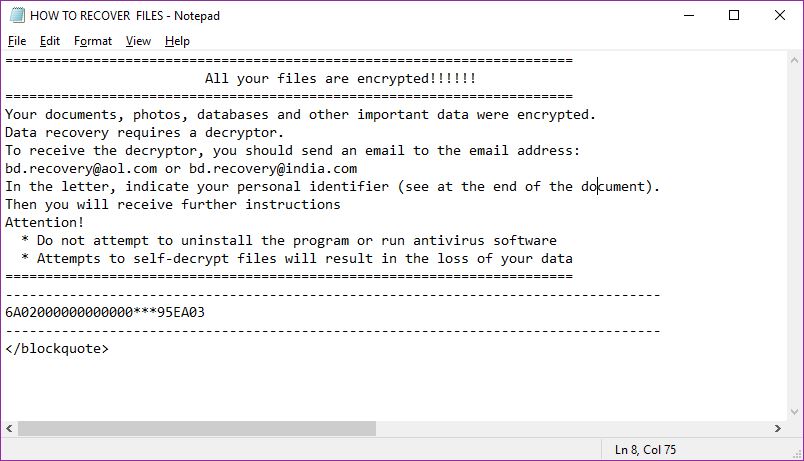
![.[Filesreturn247@gmx.de].lock Files Virus (Scarab) – Remove It and Restore Data](https://cdn.sensorstechforum.com/wp-content/uploads/2018/07/stf-remove-scarab-ransomware-and-restore-Filesreturn247@gmx.de_.lock-encrypted-files-sensorstechforum-com.png)