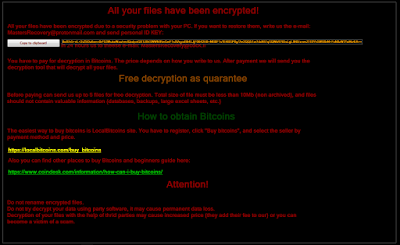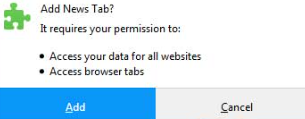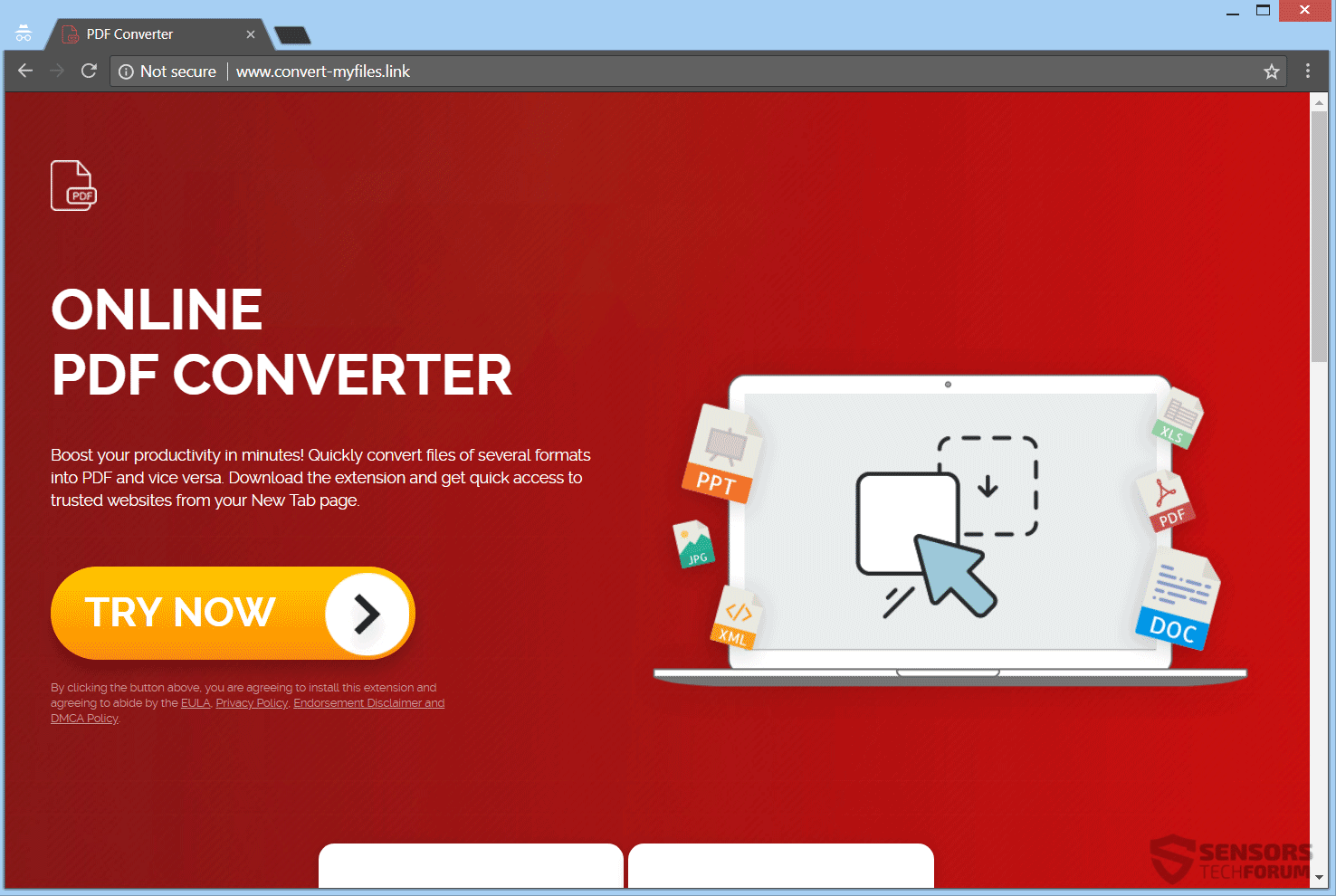
Remove Freerpgonline.net Redirect
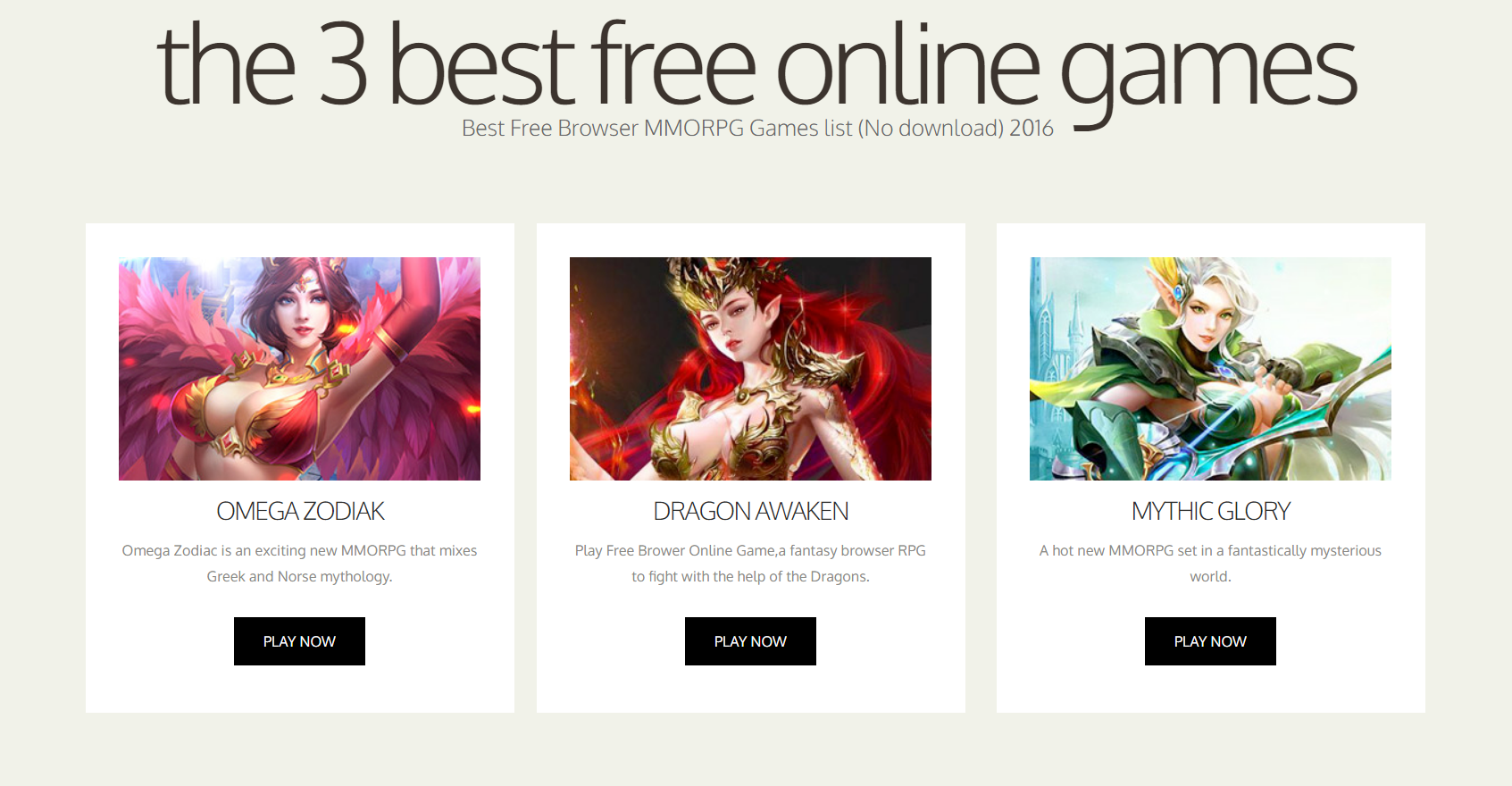
This article aims to help you with the removal of Freerpgonline.net redirect from affected web browsers and system. Follow the detailed guide to remove this nasty redirect completely from your PC. The suspicious website Freerpgonline.net appears in commonly used web…