MBRlock Virus — How to Remove + Restore Encrypted Files
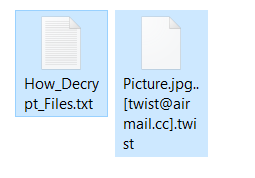
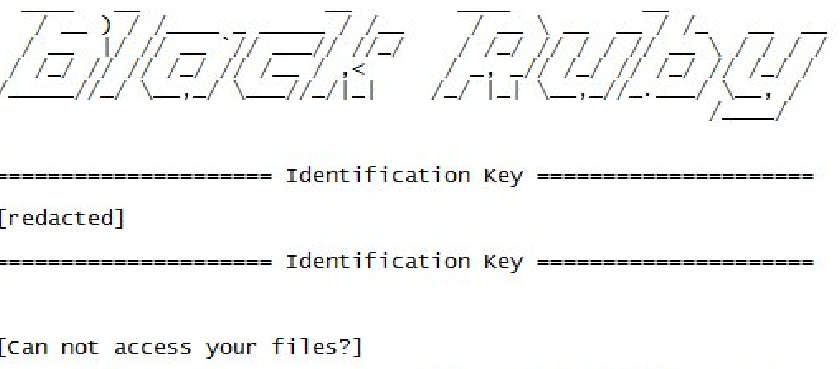
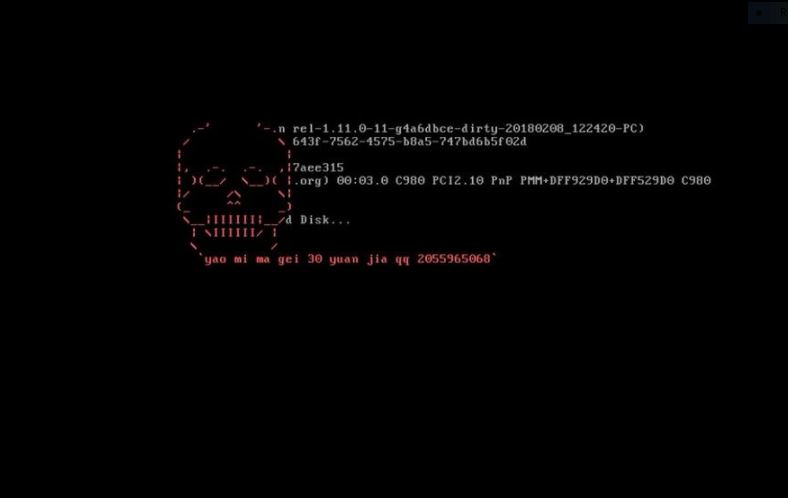
The MBRlock virus is a dangerous ransomware that is able to corrupt the Master Boot Record (MBR) of the victim machines. It then extorts the victims to pay a ransomware fee. The infections can also cause a wide variety of…



![Taskhostw.exe – What Is It + How to Remove It [Fix] Taskhostw.exe - What Is It + How to Remove It [Fix]](https://cdn.sensorstechforum.com/wp-content/uploads/2018/02/taskhostw-exe-what-is-it-how-to-remove-it-1024x576.jpg)