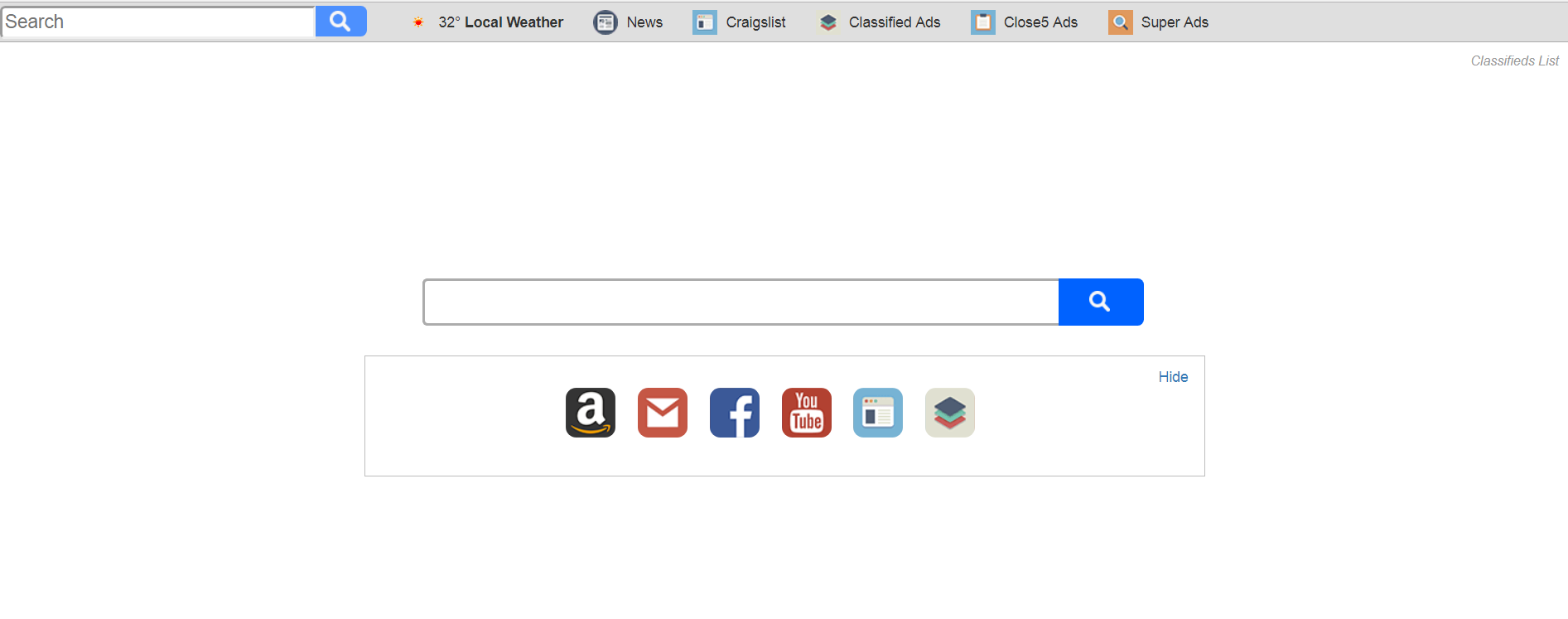
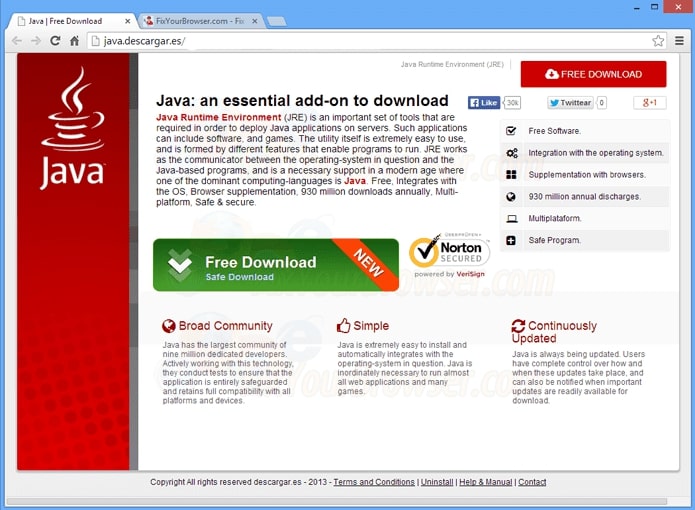
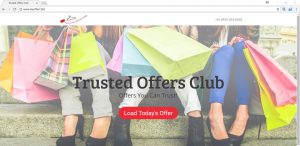
Remove Chrome-tab.com Redirect Effectively
This article provides step-by-step removal for Chrome-tab.com. Follow the guide below to remove the redirect entirely from Chrome, Firefox, Explorer, Safari, and Windows system. Chrome-tab.com is a website of unknown origin that affects commonly used browsers in an attempt to…








![Java:Malware-gen [Trj] Trojan – How to Detect and Remove CrossRAT](https://cdn.sensorstechforum.com/wp-content/uploads/2016/02/remote-access-trojan-sensorstechforum-300x260.png)