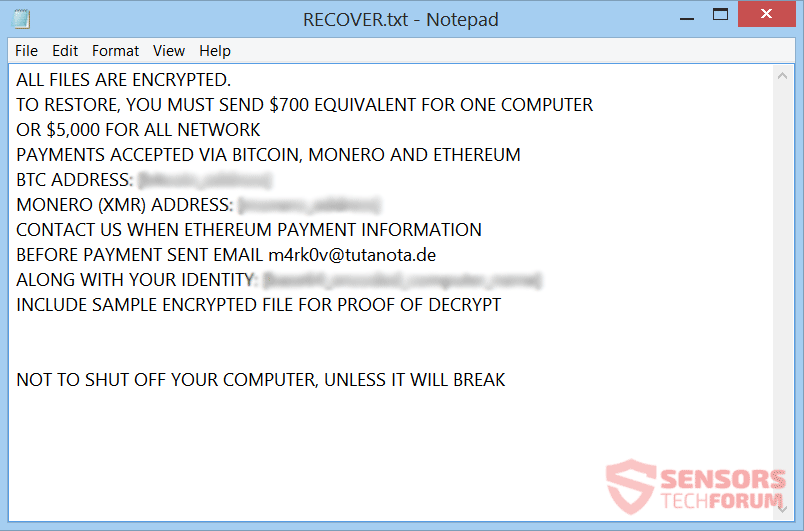
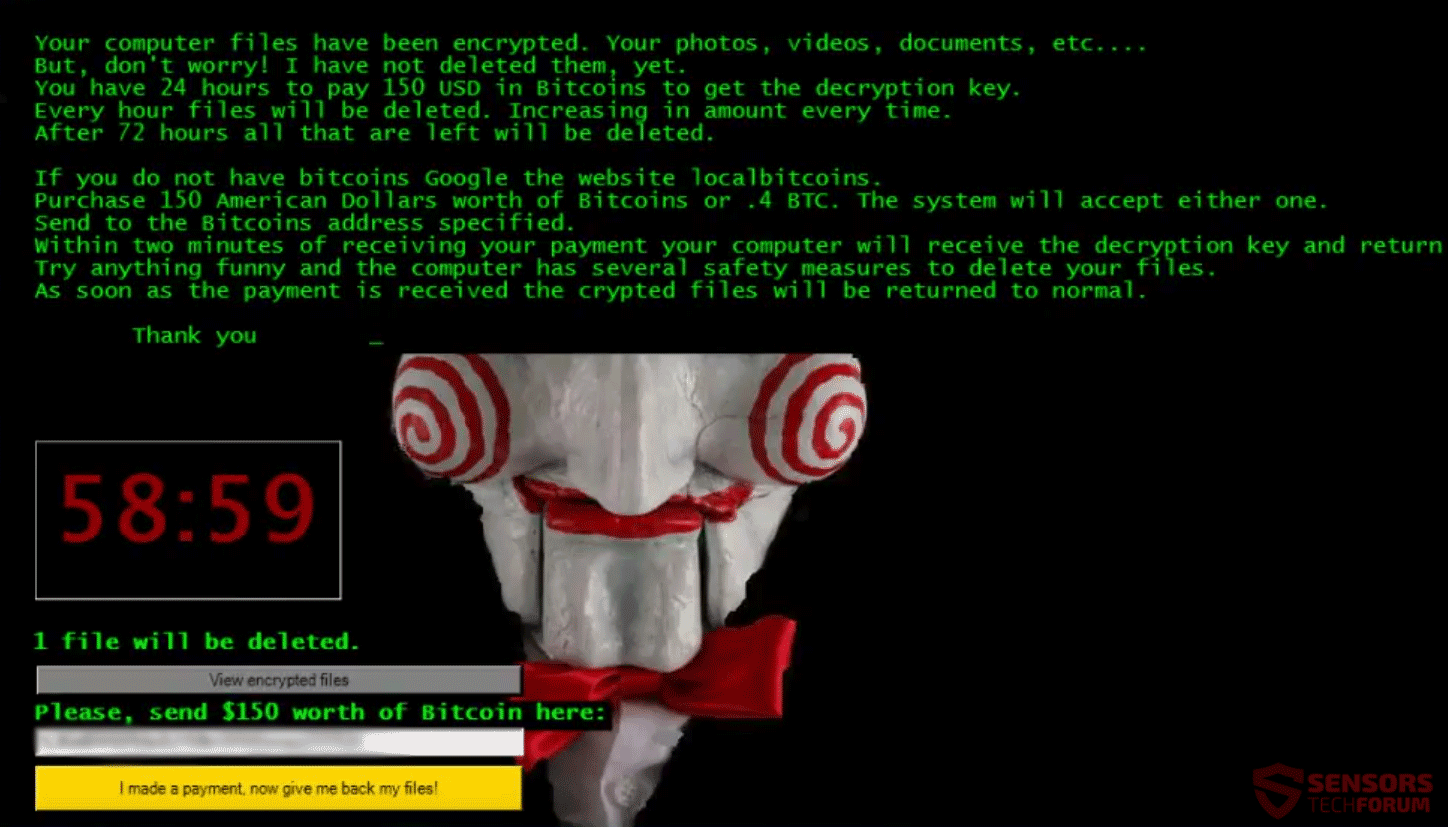
Remove LazagneCrypt Ransomware – Restore .encr Files
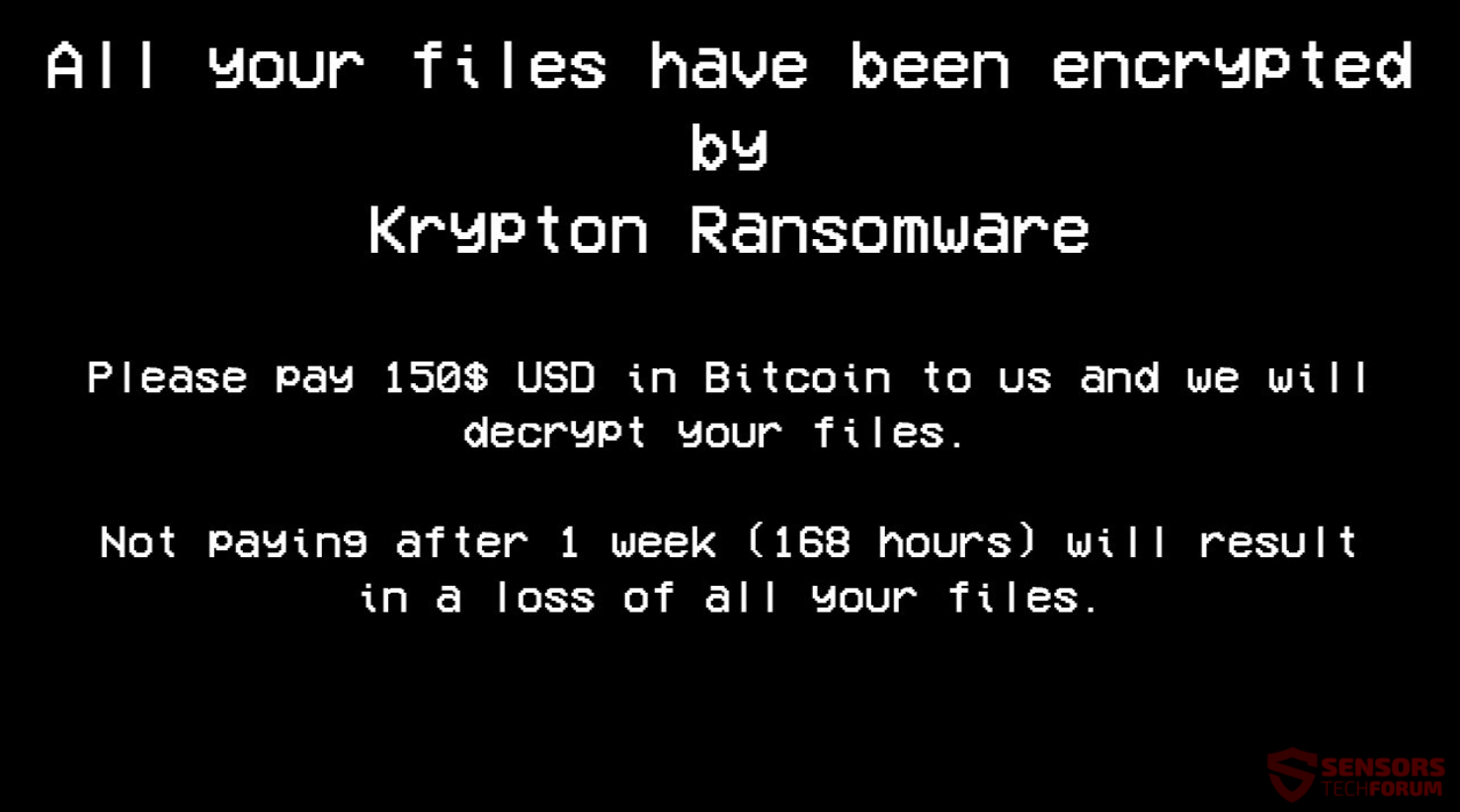
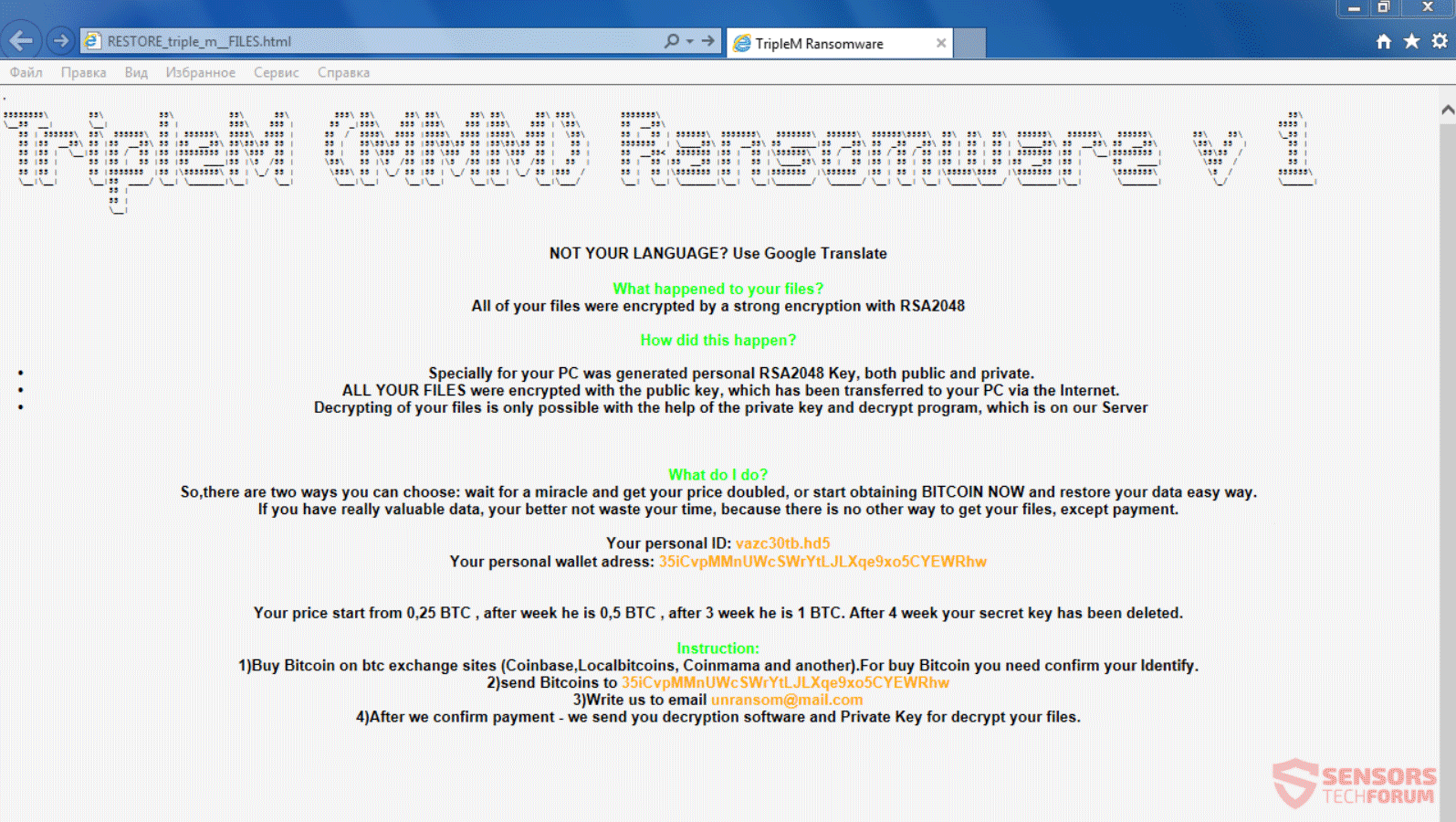
This article is created to help users infected by LazagneCrypt ransomware through the removal and the recovery process of .encr files. LazagneCrypt ransomware aims to locate predefined types of files stored on the compromised machine and then encrypts them. For…