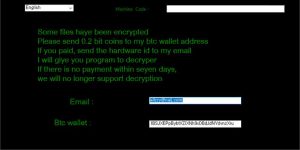
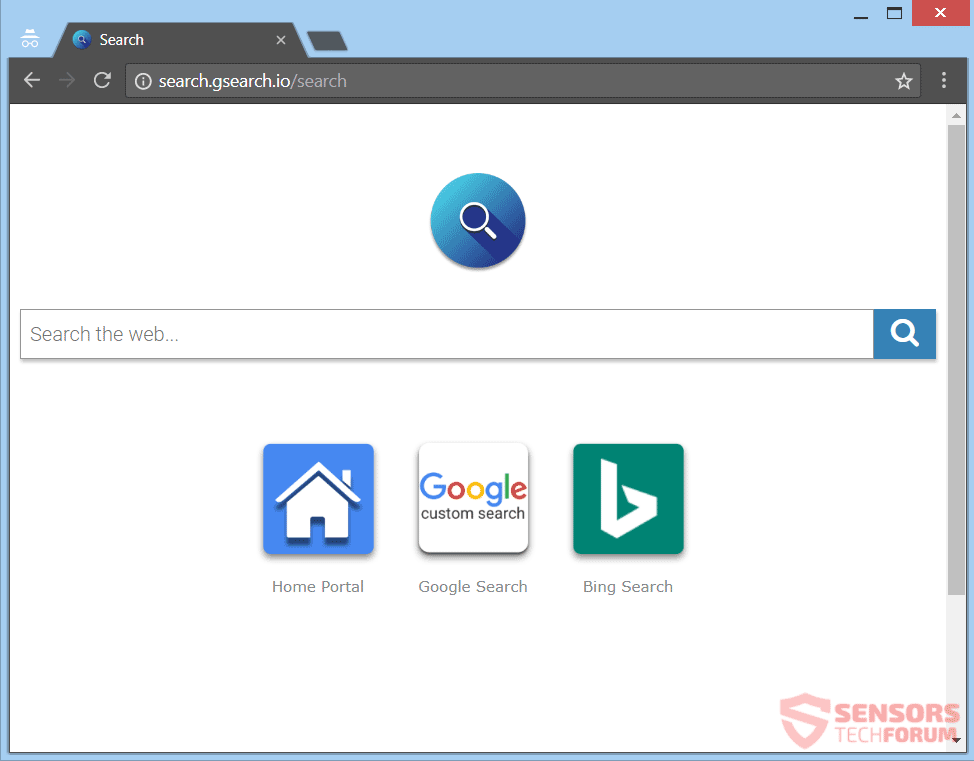
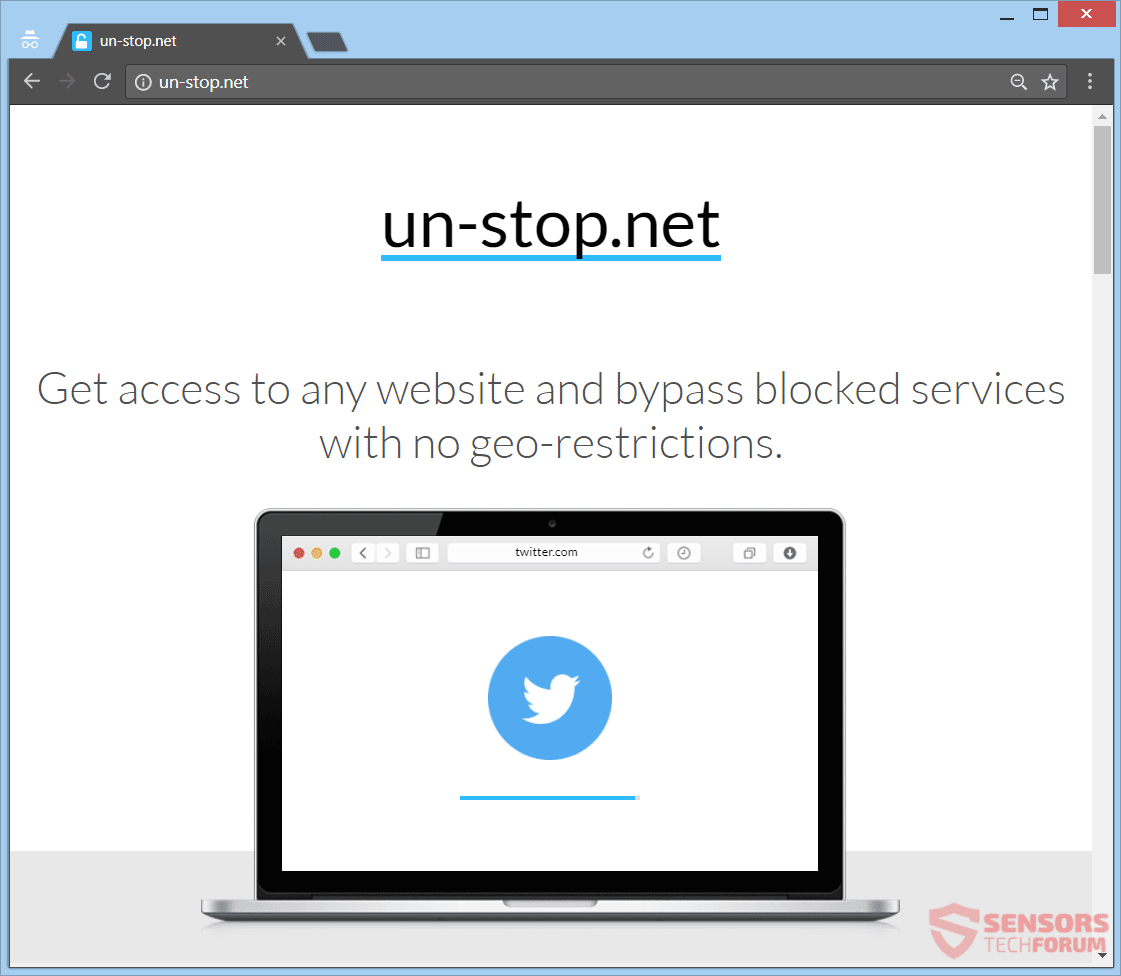
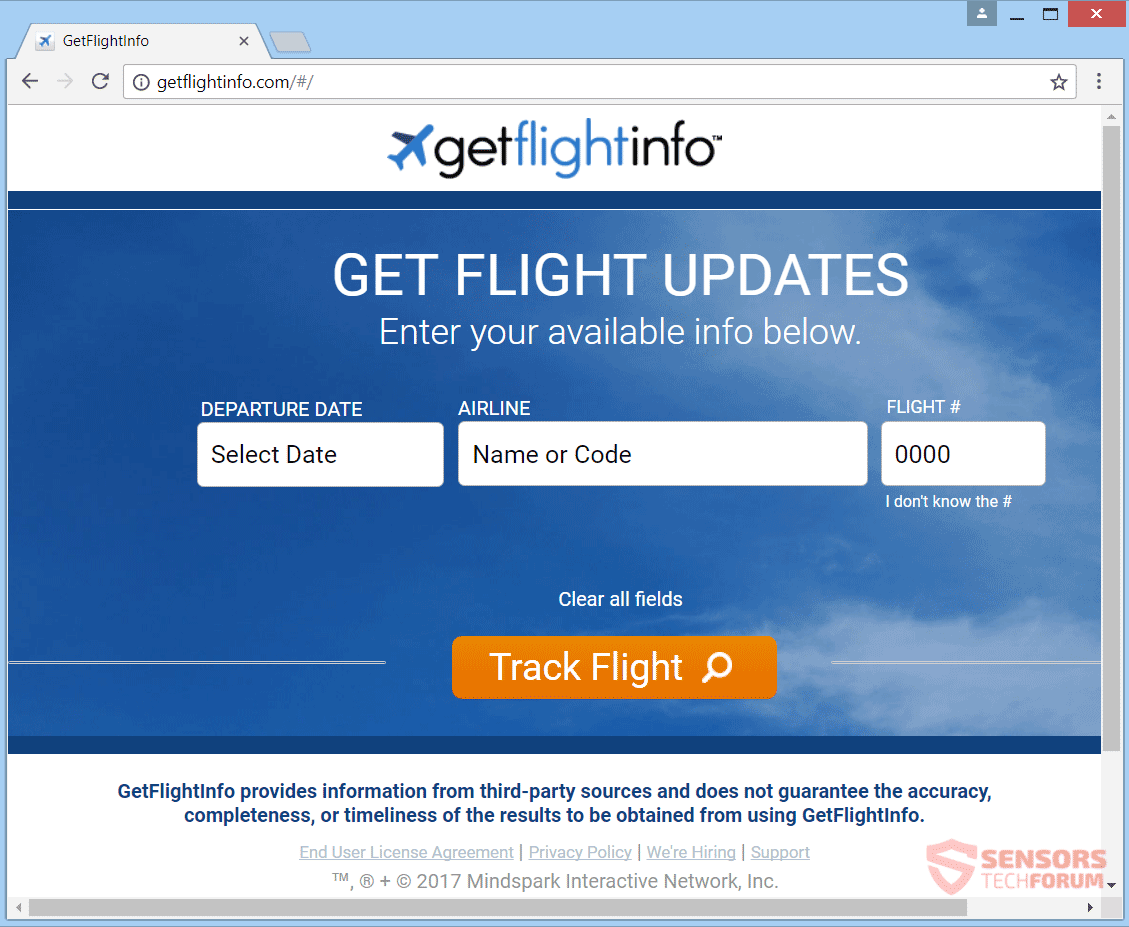
Fastplayz Adware – How to remove It from Your PC
This article aims to show you how to delete the Fastplayz adware from your computer system and protect it from ads in the future. An ad-supported program, going by the name Fastplayz has been the reason for many different reports…