Remove Zeus Trojan Virus
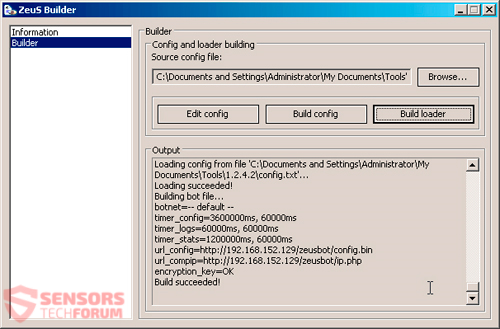
In this Article you will find out how to remove Zeus Trojan virus and get rid of infected files. Zeus Trojan horse virus is spread on a large scale via the RIG Exploit Kit. That new version is dubbed “Chthonic”…

In this Article you will find out how to remove Zeus Trojan virus and get rid of infected files. Zeus Trojan horse virus is spread on a large scale via the RIG Exploit Kit. That new version is dubbed “Chthonic”…

CVE-2017-1000367 is a severe root Linux vulnerability discovered by Qualys Security researchers. The flaw resides in Sudo’s “get_process_ttyname()” function for Linux and could allow a user with Sudo privileges to run commands as root or elevate privileges to root. Sudo,…

This article has the agenda to show you how to remove OoPS Ransomware and attempt to restore files that have been encrypted with the added .ramen file extension. A file encryption malware, known as OoPS ransomware has been detected at…
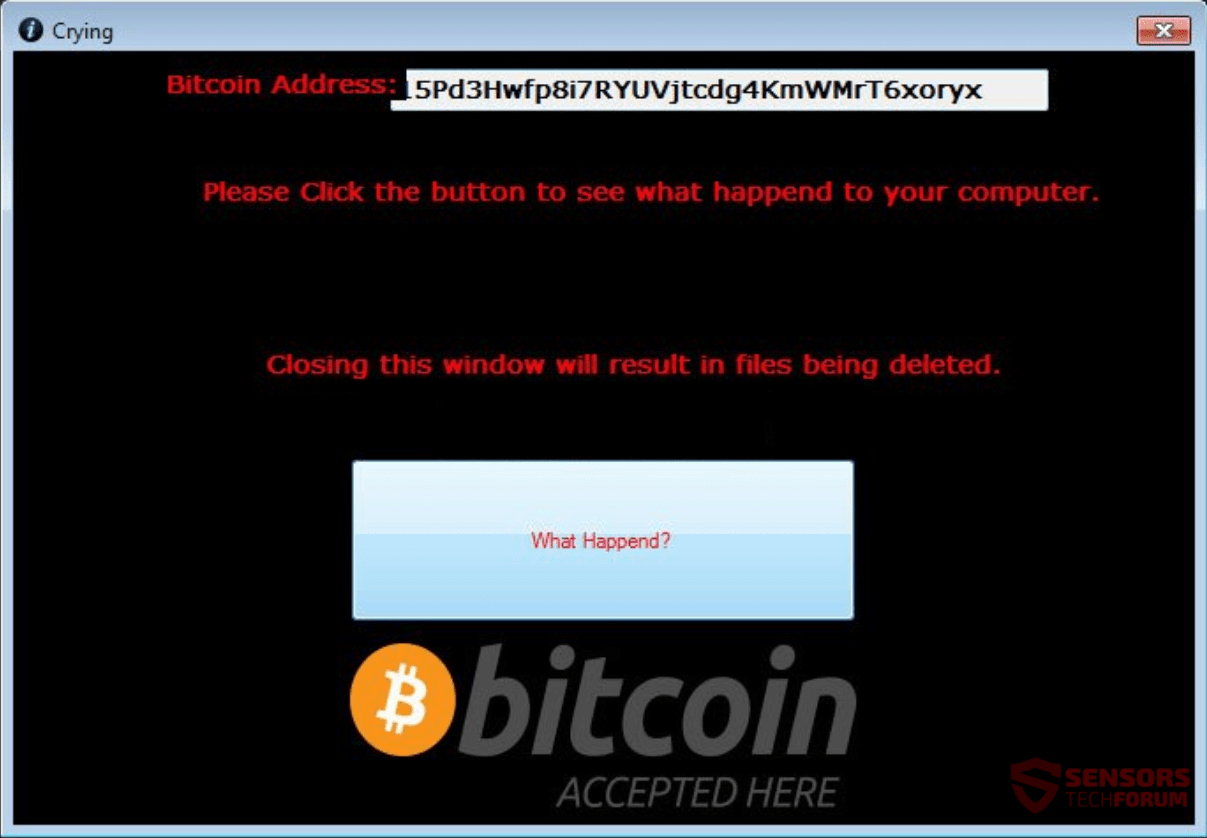
This article will help you remove Crying ransomware efficiently. Follow the ransomware removal instructions at the end of the article. Crying is a ransomware cryptovirus that displays multiple windows with its instructions for ransom payment. The ransomware is a variant…
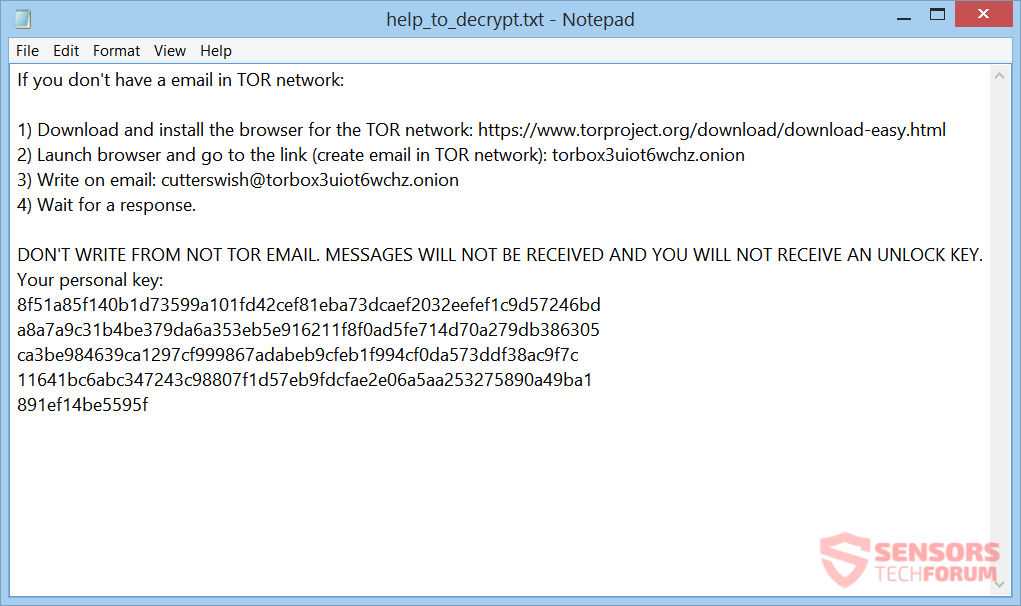
This article will aid you in removing the Yyto files virus efficiently. Follow the ransomware removal instructions provided at the end. .Yyto files virus is how a ransomware cryptovirus is called. The extension it places to all files after encrypting…

AOL web developer Ran Bar-Zik has uncovered a Google Chrome bug that allows websites to record audio and video without the user’s knowledge or any signs of the activity. Google however doesn’t consider the bug to be a critical security…

Article created to explain how to remove AES-NI ransomware from your computer and decrypt AES_NI encrypted files for free. Update May 2017! A decrypter has been developed for a ransomware virus, known by many as AES-NI ransomware. The infection aims…
Article created to show you how to remove the Gomme Ransom virus from your computer and restore files encrypted with .gommemode file extension. A new ransomware virus has appeared at the end of March 2017. The virus encrypts the files…
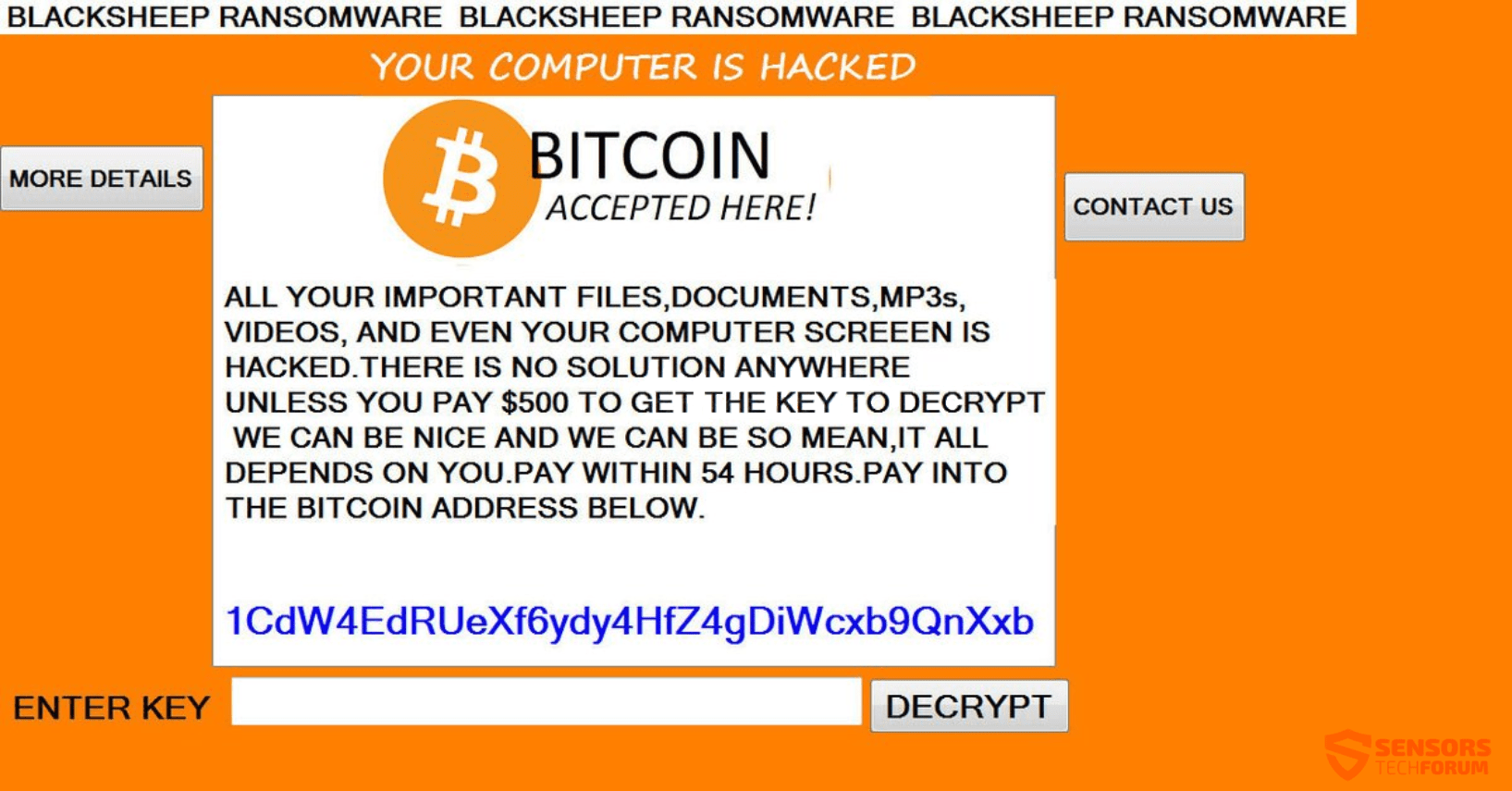
This article will help you remove BlackSheep ransomware efficiently. Follow the ransomware removal instructions at the end of the article. BlackSheep is a ransomware cryptovirus that displays a fake Windows Update screen, while it encrypts your files. The ransomware will…
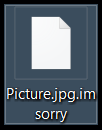
This article has been created in order to show you how to remove ImSorry ransomware and restore AES encrypted files with the .imsorry file extension. A ransomware virus encrypting files via the AES algorithm and demanding $500 ransom payoff in…

The Android operating system has a restriction to block the installation of applications outside Play Store. Switching to “unknown sources” is a very bad idea regarding the security of the device, and any many security experts would confirm this. Interestingly,…
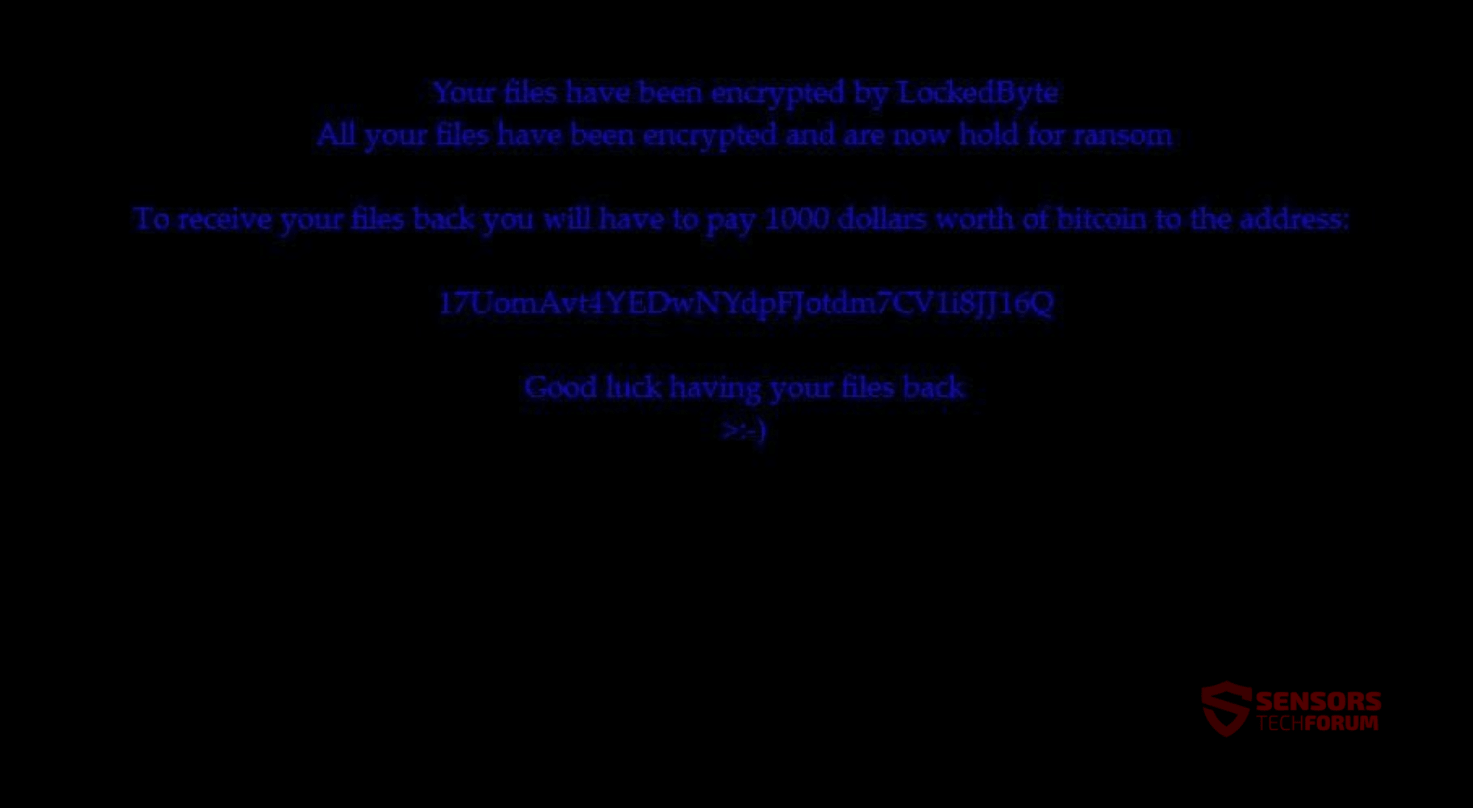
This article will help you remove LockedByte ransomware absolutely. Follow the ransomware removal instructions at the end of the article. LockedByte is how a new ransomware threat is called. More precisely, this threat is a virus that encrypts files. It…

This article will explain what is .wtdi ransomware and help you remove the .NET CryptoWall.exe ransomware plus restore encrypted files on your computer. A ransomware virus believed to imitate the notorious CryptoWall and is written in .NET has appeared in…
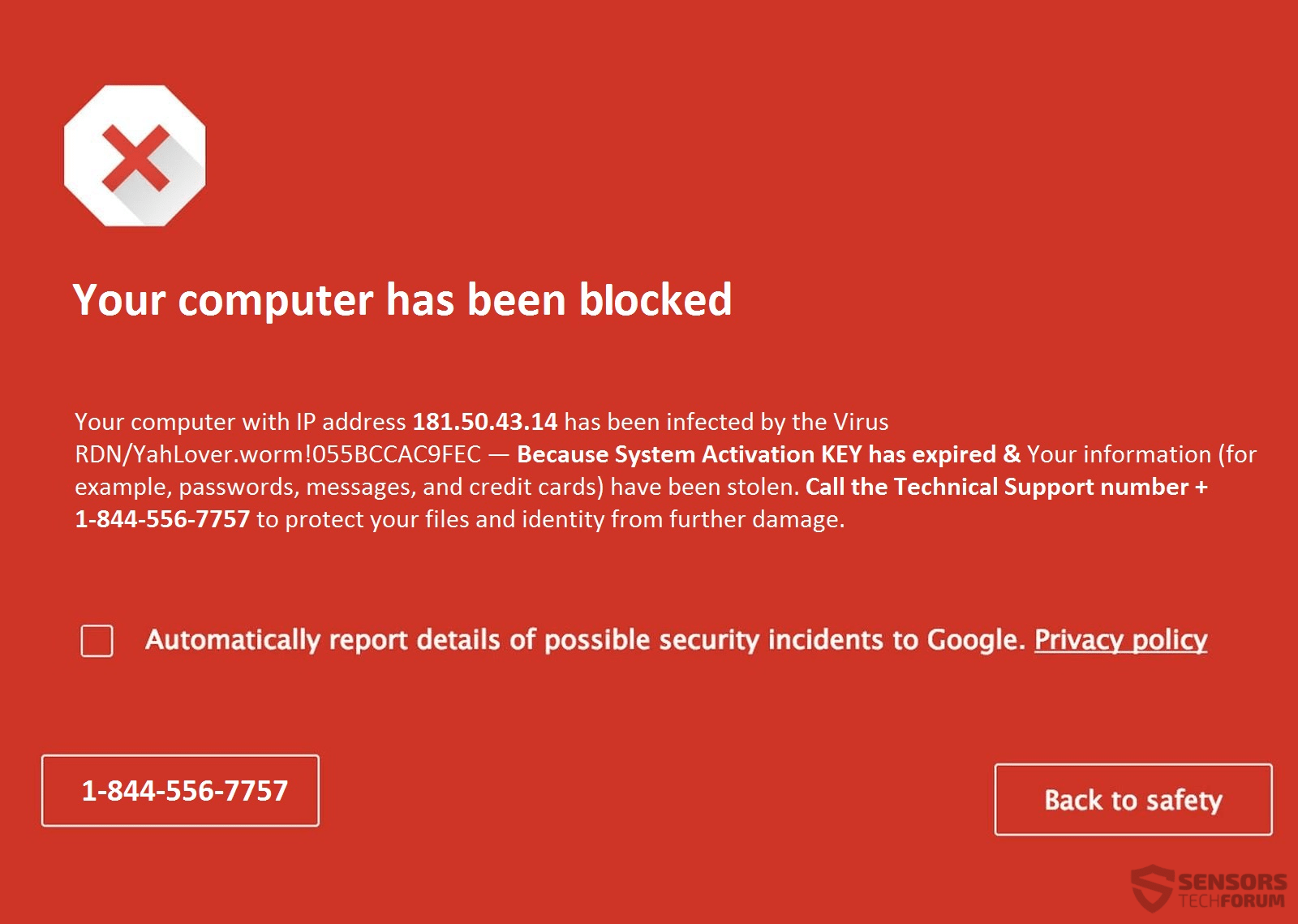
Your Windows Computer Has Been Blocked is a message which is used often in a lot of fake technical support sites. These websites involve a scam and almost always leave a phone number on their page, including on the inside…
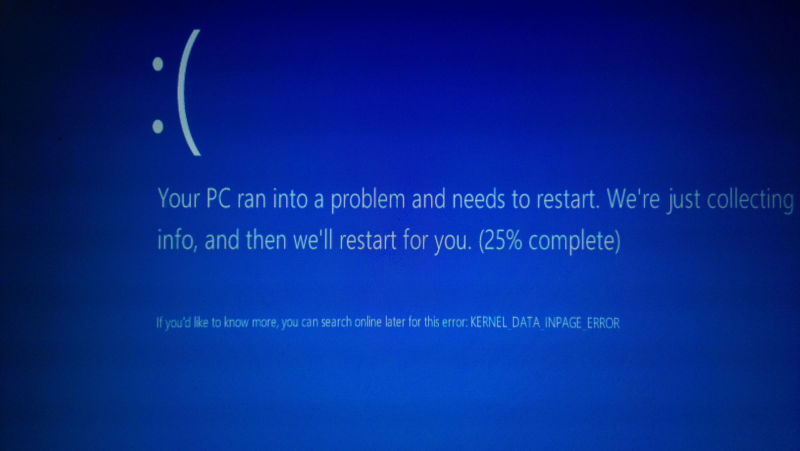
A new Windows flaw, affecting almost all versions of the OS, Windows 10 excluded has been unearthed. More specifically, Windows 7 and Windows 8.1 are prone to the same bug where certain bad filenames make the system lock up or…

Article created to show you how to remove SmartRansom Chinese ransomware virus and restore files encrypted by it. A ransomware virus, that has a QR scanning code embedded in it’s ransom note so that a payoff in BitCoin can be…
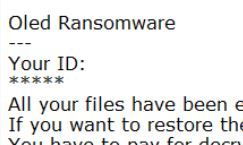
This article aims to help you remove the Oled ransomware virus completely from your computer and restore files encrypted with .oled file extension added. A ransomware virus, believed to be a part of the BTCWare ransomware family has been reported…

Have you heard of the Samba project? It’s a popular open source project that is used on Linux and Unix machines so that they work with Windows file and print services. The project lets you work as a client that…

This article aims to help you remove the LightningCrypt ransomware virus from your computer and restore the files encrypted with .LIGHTNING file extension added to them. Discovered at the end of May 2017, the LightningCrypt ransomware is a well-designed virus…

Researchers from Georgia Institute of Technology and UC Santa Barbara have uncovered a new Android exploit affecting all versions of the operating system. The exploit is dubbed Cloak and Dagger and is seen as a new class of potential attacks…