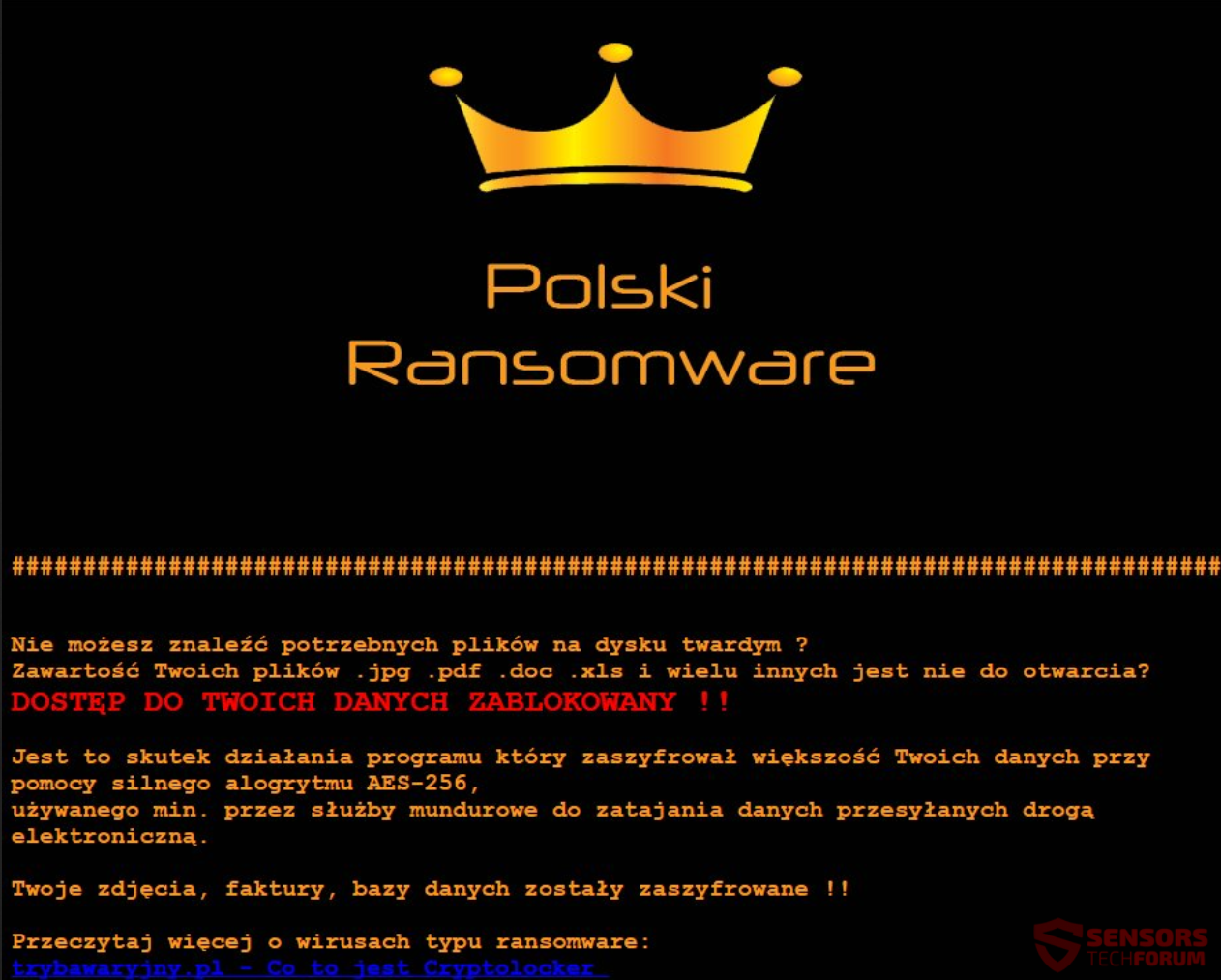
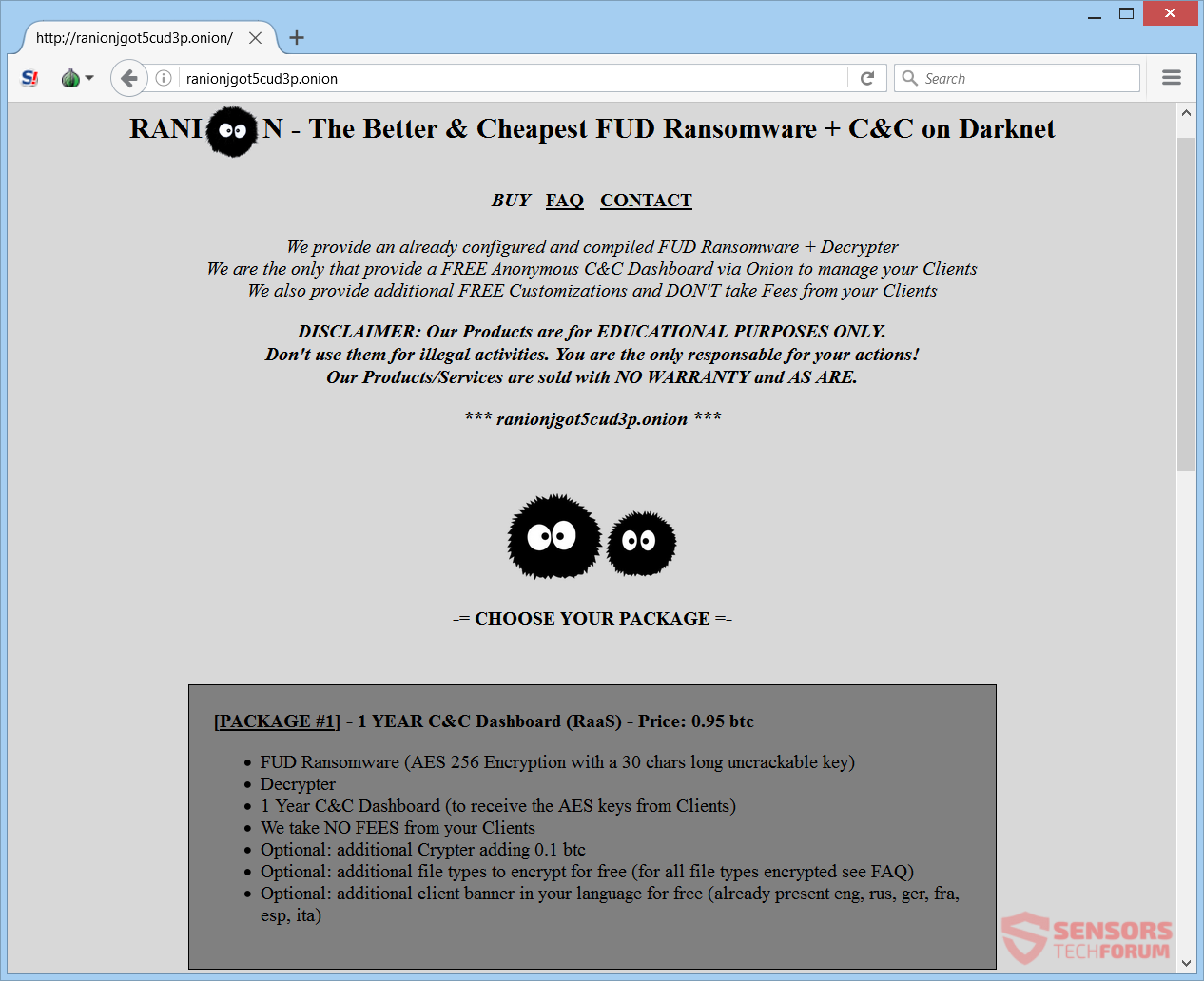
Fileless Malware Plagues 140 Banks Across 40 Countries
Previously associated with nation-sponsored attacks like the Stuxnet worm, fileless malware is now going mainstream. According to an upcoming Kaspersky Lab research, networks of at least 140 banks have been infected by fileless malware that relies on in-memory design to…