Another variant of the Shade Trojan ransomware has appeared lately and bears the name Files1147@gmail(.)com. That is the email provided by cybercriminals, for where the ransom money to be sent. The ransomware encrypts files with a .breaking_bad file extension. In the past, it has been given the names Trojan-Ransom.Win32.Shade and Ransom:Win32/Troldesh. It uses the same warning message as its previous variants.
| Name | Files1147@gmail(.)com |
| Type | Ransomware, Trojan |
| Short Description | This ransomware is a newer variant of the Shade ransomware family. |
| Symptoms | The Ransomware encrypts files and adds a .breaking_bad extension to them. It uses a gmail account for the ransom money to be received. |
| Distribution Method | Exploit Kits, Spam Emails. |
| Detection tool | Download Malware Removal Tool, to See If Your System Has Been Affected by malware |
| User Experience | Join our forum to discuss the Files1147@gmail(.)com ransomware. |
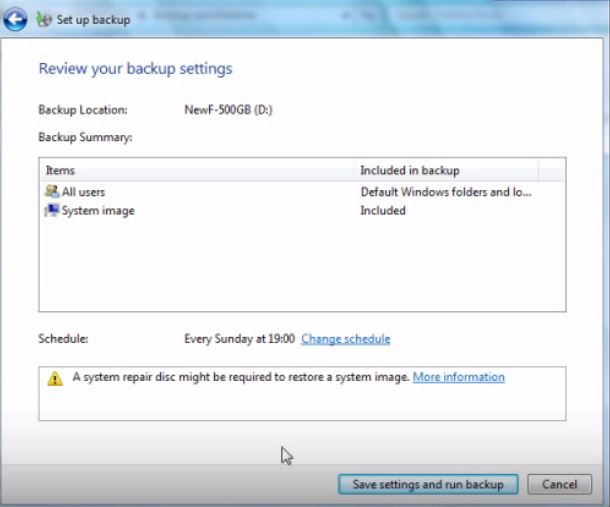
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |
Files1147@gmail(.)com Distribution Ways
Exploit Kits
One way of distribution for the Files1147@gmail(.)com ransomware is through exploit kits, mainly – the Nuclear EK. Just visiting a site with an exloit kit injected into it is enough for your computer to get infected. Cyber crooks can put malicious code inside legitimate and non-legitimate websites as well. That code exploits a vulnerability of a browser or its extensions and add-ons. After a vulnerability is found, the ransomware is secretly installed on the computer. In almost all cases you will be unaware that it even happened.
Spam Emails
Another way this ransomware distributes itself is via spam emails. You will receive a short email with a malware file attached. If you open the attachment, the malware is then spread. The Files1147@gmail(.)com ransomware has been using the files for distribution from its previous variants – namely these:
- doc_dlea podpisi.com
- doc_dlea podpisi.rar
- documenti_589965465_documenti.com
- documenti_589965465_documenti.rar
- documenti_589965465_doc.scr
- doc_dlea podpisi.rar
- неподтвержден 308853.scr
- documenti dlea podpisi 05.08.2015.scr.exe
- akt sverki za 17082015.scr
Although, be aware that the file names can have different variations, so that they can trick you.
Files1147@gmail(.)com Technical Details
The Files1147@gmail(.)com ransomware seems to behave very similarly as its other known variants. The technical name of the first Shade ransomware variant is labeled as Trojan-Ransom.Win32.Shade by some researchers and Ransom:Win32/Troldesh by others.
Once the ransomware is on a compromised computer, it connects to a remote command & control (C&C) server in the Tor network. From there, it notifies the server and requests an RSA-3072 algorithm key so it can use it to encrypt files. Encrypted files have the extension .breaking_bad. However, if the connection is unsuccessful, the Files1147@gmail(.)com ransomware will choose 1 of 100 keys, stored within its code.
When the process is complete, files with the following extensions will be encrypted:
→.3ds .3fr .3g2 .3gp .7z .accda .accdb .accdc .accde .accdt .accdw .adb .adp .ai .ai3 .ai4 .ai5 .ai6 .ai7 .ai8 .anim .arw .as .asa .asc .ascx .asm .asmx .asp .aspx .asr .asx .avi .avs .backup .bak .bay .bd .bin .bmp .bz2 .c .cdr .cer .cf .cfc .cfm .cfml .cfu .chm .cin .class .clx .config .cpp .cr2 .crt .crw .cs .css .csv .cub .dae .dat .db .dbf .dbx .dc3 .dcm .dcr .der .dib .dic .dif .divx .djvu .dng .doc .docm .docx .dot .dotm .dotx .dpx .dqy .dsn .dt .dtd .dwg .dwt .dx .dxf .edml .efd .elf .emf .emz .epf .eps .epsf .epsp .erf .exr .f4v .fido .flm .flv .frm .fxg .geo .gif .grs .gz .h .hdr .hpp .hta .htc .htm .html .icb .ics .iff .inc .indd .ini .iqy .j2c .j2k .java .jp2 .jpc .jpe .jpeg .jpf .jpg .jpx .js .jsf .json .jsp .kdc .kmz .kwm .lasso .lbi .lgf .lgp .log .m1v .m4a .m4v .max .md .mda .mdb .mde .mdf .mdw .mef .mft .mfw .mht .mhtml .mka .mkidx .mkv .mos .mov .mp3 .mp4 .mpeg .mpg .mpv .mrw .msg .mxl .myd .myi .nef .nrw .obj .odb .odc .odm .odp .ods .oft .one .onepkg .onetoc2 .opt .oqy .orf .p12 .p7b .p7c .pam .pbm .pct .pcx .pdd .pdf .pdp .pef .pem .pff .pfm .pfx .pgm .php .php3 .php4 .php5 .phtml .pict .pl .pls .pm .png .pnm .pot .potm .potx .ppa .ppam .ppm .pps .ppsm .ppt .pptm .pptx .prn .ps .psb .psd .pst .ptx .pub .pwm .pxr .py .qt .r3d .raf .rar .raw .rdf .rgbe .rle .rqy .rss .rtf .rw2 .rwl .safe .sct .sdpx .shtm .shtml .slk .sln .sql .sr2 .srf .srw .ssi .st .stm .svg .svgz .swf .tab .tar .tbb .tbi .tbk .tdi .tga .thmx .tif .tiff .tld .torrent .tpl .txt .u3d .udl .uxdc .vb .vbs .vcs .vda .vdr .vdw .vdx .vrp .vsd .vss .vst .vsw .vsx .vtm .vtml .vtx .wb2 .wav .wbm .wbmp .wim .wmf .wml .wmv .wpd .wps .x3f .xl .xla .xlam .xlk .xlm .xls .xlsb .xlsm .xlsx .xlt .xltm .xltx .xlw .xml .xps .xsd .xsf .xsl .xslt .xsn .xtp .xtp2 .xyze .xz .zip
After the files are encrypted, the following message will be left as a desktop image:
All the important files on your computer were encrypted.
The details can be found in README.txt files
which you can find on any of your disks.
The ransom request will be left in 10 README.txt documents. All of them contain one and the same text inside, such as the following example:
Ваши файлы были зашифрованы.
Чтобы расшифровать их, Вам необходимо отправить код:
667EBB7E9D12BE9C733C|0
на электронный адрес files1147@gmail.com .
Далее вы получите все необходимые инструкции.
Попытки расшифровать самостоятельно не приведут ни к чему, кроме безвозвратной потери информации.All the important files on your computer were encrypted.
To decrypt the files you should send the following code:
667EBB7E9D12BE9C733C|0
to e-mail address files1147@gmail.com .
Then you will receive all necessary instructions.
All the attempts of decryption by yourself will result only in irrevocable loss of your data.
Important!
It is essential to note the attacks of Files1147@gmail(.)com don’t stop here. Its process creates an infinite loop of malware infections by contacting the C&C server and obtains a list of malicious URLs. This is commonly referred to as a download bot.
According to malware researchers, malware of the following families is frequently downloaded:
- Trojan.Win32.CMSBrute
- Trojan.Win32.Miuref
- Trojan.Win32.Kovter
- Trojan-Downloader.Win32.Zemot
Judging by the extension and that it is working in collaboration with other malware, it can be assumed it also works together with the Los Pollos Hermanos ransomware.
Files1147@gmail(.)com Removal
If you have been infected by the Files1147@gmail(.)com ransomware, you should have at least some experience in removing viruses. The Trojan is made to download malware of different families, so it is highly recommended that you carefully follow the instructions provided below:
- Step 1
- Step 2
- Step 3
- Step 4
- Step 5
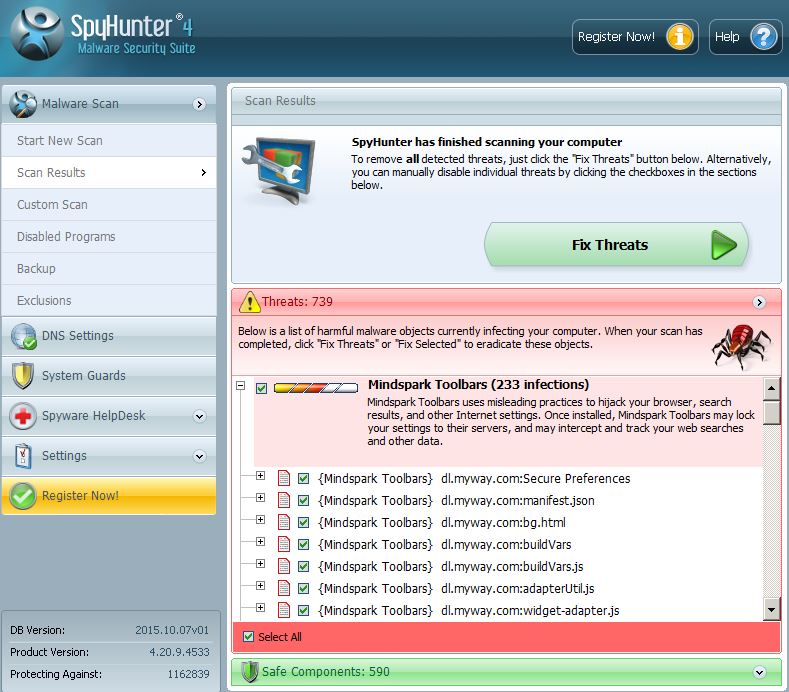
Step 1: Scan for Files1147@gmail(.)com with SpyHunter Anti-Malware Tool



Ransomware Automatic Removal - Video Guide
Step 2: Uninstall Files1147@gmail(.)com and related malware from Windows
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Step 3: Clean any registries, created by Files1147@gmail(.)com on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Files1147@gmail(.)com there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
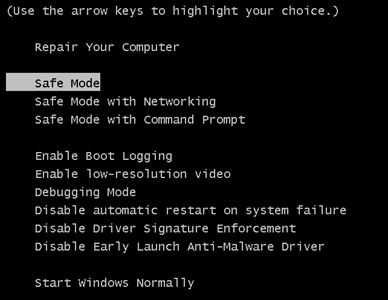
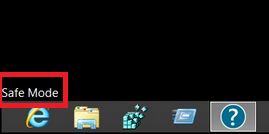
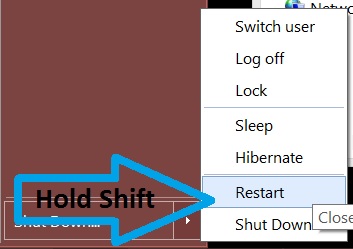
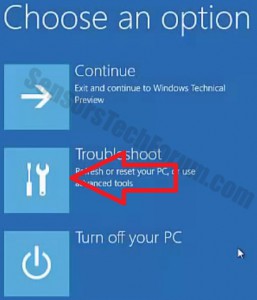
Before starting "Step 4", please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
Step 4: Boot Your PC In Safe Mode to isolate and remove Files1147@gmail(.)com





Step 5: Try to Restore Files Encrypted by Files1147@gmail(.)com.
Method 1: Use STOP Decrypter by Emsisoft.
Not all variants of this ransomware can be decrypted for free, but we have added the decryptor used by researchers that is often updated with the variants which become eventually decrypted. You can try and decrypt your files using the instructions below, but if they do not work, then unfortunately your variant of the ransomware virus is not decryptable.
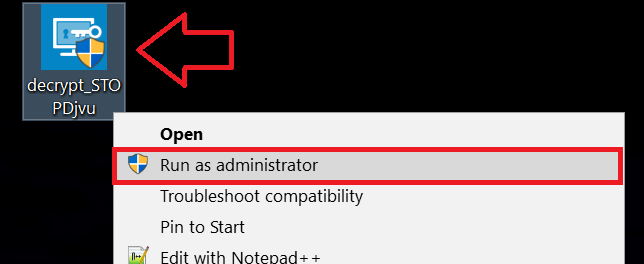
Follow the instructions below to use the Emsisoft decrypter and decrypt your files for free. You can download the Emsisoft decryption tool linked here and then follow the steps provided below:
1 Right-click on the decrypter and click on Run as Administrator as shown below:
2. Agree with the license terms:
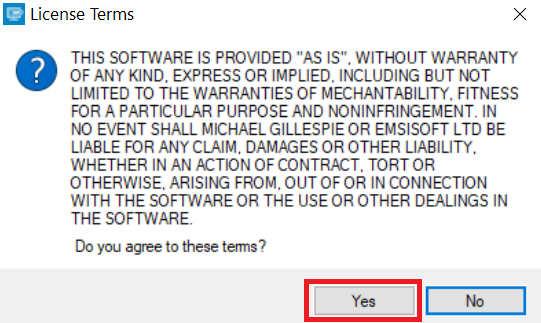
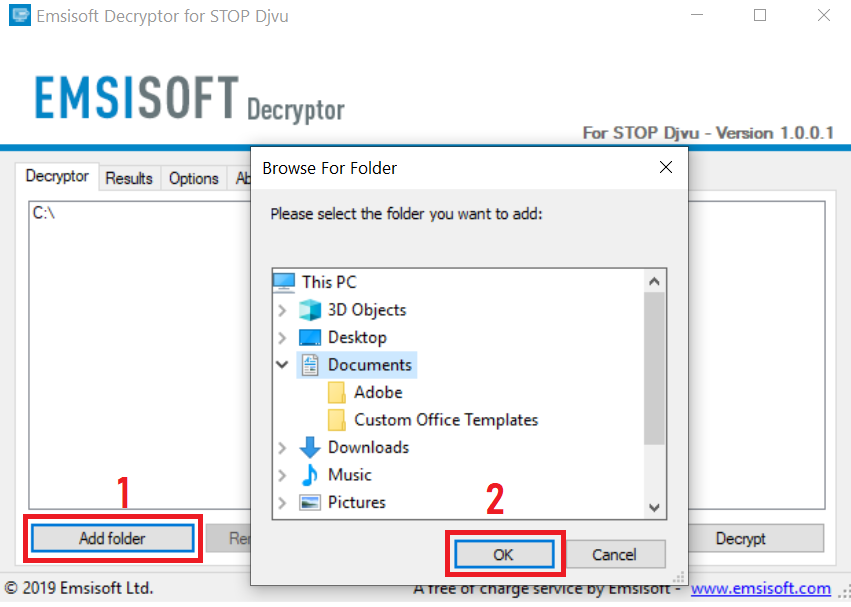
3. Click on "Add Folder" and then add the folders where you want files decrypted as shown underneath:
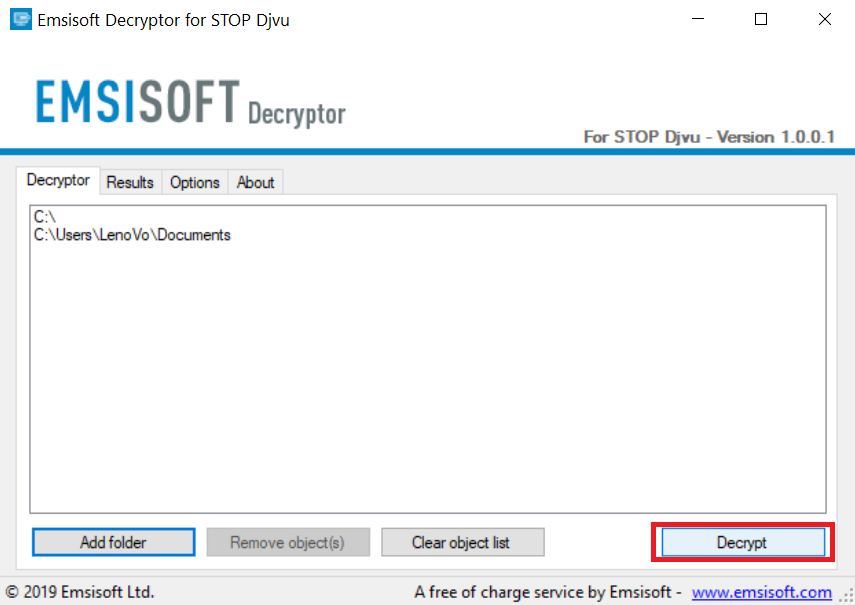
4. Click on "Decrypt" and wait for your files to be decoded.
Note: Credit for the decryptor goes to Emsisoft researchers who have made the breakthrough with this virus.
Method 2: Use data recovery software
Ransomware infections and Files1147@gmail(.)com aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested a data recovery method that may help you go around direct decryption and try to restore your files. Bear in mind that this method may not be 100% effective but may also help you a little or a lot in different situations.
Simply click on the link and on the website menus on the top, choose Data Recovery - Data Recovery Wizard for Windows or Mac (depending on your OS), and then download and run the tool.
Files1147@gmail(.)com-FAQ
What is Files1147@gmail(.)com Ransomware?
Files1147@gmail(.)com is a ransomware infection - the malicious software that enters your computer silently and blocks either access to the computer itself or encrypt your files.
Many ransomware viruses use sophisticated encryption algorithms to make your files inaccessible. The goal of ransomware infections is to demand that you pay a ransom payment to get access to your files back.
What Does Files1147@gmail(.)com Ransomware Do?
Ransomware in general is a malicious software that is designed to block access to your computer or files until a ransom is paid.
Ransomware viruses can also damage your system, corrupt data and delete files, resulting in the permanent loss of important files.
How Does Files1147@gmail(.)com Infect?
Via several ways.Files1147@gmail(.)com Ransomware infects computers by being sent via phishing emails, containing virus attachment. This attachment is usually masked as an important document, like an invoice, bank document or even a plane ticket and it looks very convincing to users.
Another way you may become a victim of Files1147@gmail(.)com is if you download a fake installer, crack or patch from a low reputation website or if you click on a virus link. Many users report getting a ransomware infection by downloading torrents.
How to Open .Files1147@gmail(.)com files?
You can't without a decryptor. At this point, the .Files1147@gmail(.)com files are encrypted. You can only open them once they are decrypted using a specific decryption key for the particular algorithm.
What to Do If a Decryptor Does Not Work?
Do not panic, and backup the files. If a decryptor did not decrypt your .Files1147@gmail(.)com files successfully, then do not despair, because this virus is still new.
Can I Restore ".Files1147@gmail(.)com" Files?
Yes, sometimes files can be restored. We have suggested several file recovery methods that could work if you want to restore .Files1147@gmail(.)com files.
These methods are in no way 100% guaranteed that you will be able to get your files back. But if you have a backup, your chances of success are much greater.
How To Get Rid of Files1147@gmail(.)com Virus?
The safest way and the most efficient one for the removal of this ransomware infection is the use a professional anti-malware program.
It will scan for and locate Files1147@gmail(.)com ransomware and then remove it without causing any additional harm to your important .Files1147@gmail(.)com files.
Can I Report Ransomware to Authorities?
In case your computer got infected with a ransomware infection, you can report it to the local Police departments. It can help authorities worldwide track and determine the perpetrators behind the virus that has infected your computer.
Below, we have prepared a list with government websites, where you can file a report in case you are a victim of a cybercrime:
Cyber-security authorities, responsible for handling ransomware attack reports in different regions all over the world:
Germany - Offizielles Portal der deutschen Polizei
United States - IC3 Internet Crime Complaint Centre
United Kingdom - Action Fraud Police
France - Ministère de l'Intérieur
Italy - Polizia Di Stato
Spain - Policía Nacional
Netherlands - Politie
Poland - Policja
Portugal - Polícia Judiciária
Greece - Cyber Crime Unit (Hellenic Police)
India - Mumbai Police - CyberCrime Investigation Cell
Australia - Australian High Tech Crime Center
Reports may be responded to in different timeframes, depending on your local authorities.
Can You Stop Ransomware from Encrypting Your Files?
Yes, you can prevent ransomware. The best way to do this is to ensure your computer system is updated with the latest security patches, use a reputable anti-malware program and firewall, backup your important files frequently, and avoid clicking on malicious links or downloading unknown files.
Can Files1147@gmail(.)com Ransomware Steal Your Data?
Yes, in most cases ransomware will steal your information. It is a form of malware that steals data from a user's computer, encrypts it, and then demands a ransom in order to decrypt it.
In many cases, the malware authors or attackers will threaten to delete the data or publish it online unless the ransom is paid.
Can Ransomware Infect WiFi?
Yes, ransomware can infect WiFi networks, as malicious actors can use it to gain control of the network, steal confidential data, and lock out users. If a ransomware attack is successful, it could lead to a loss of service and/or data, and in some cases, financial losses.
Should I Pay Ransomware?
No, you should not pay ransomware extortionists. Paying them only encourages criminals and does not guarantee that the files or data will be restored. The better approach is to have a secure backup of important data and be vigilant about security in the first place.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, the hackers may still have access to your computer, data, or files and may continue to threaten to expose or delete them, or even use them to commit cybercrimes. In some cases, they may even continue to demand additional ransom payments.
Can a Ransomware Attack Be Detected?
Yes, ransomware can be detected. Anti-malware software and other advanced security tools can detect ransomware and alert the user when it is present on a machine.
It is important to stay up-to-date on the latest security measures and to keep security software updated to ensure ransomware can be detected and prevented.
Do Ransomware Criminals Get Caught?
Yes, ransomware criminals do get caught. Law enforcement agencies, such as the FBI, Interpol and others have been successful in tracking down and prosecuting ransomware criminals in the US and other countries. As ransomware threats continue to increase, so does the enforcement activity.
About the Files1147@gmail(.)com Research
The content we publish on SensorsTechForum.com, this Files1147@gmail(.)com how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific malware and restore your encrypted files.
How did we conduct the research on this ransomware?
Our research is based on an independent investigation. We are in contact with independent security researchers, and as such, we receive daily updates on the latest malware and ransomware definitions.
Furthermore, the research behind the Files1147@gmail(.)com ransomware threat is backed with VirusTotal and the NoMoreRansom project.
To better understand the ransomware threat, please refer to the following articles which provide knowledgeable details.
As a site that has been dedicated to providing free removal instructions for ransomware and malware since 2014, SensorsTechForum’s recommendation is to only pay attention to trustworthy sources.
How to recognize trustworthy sources:
- Always check "About Us" web page.
- Profile of the content creator.
- Make sure that real people are behind the site and not fake names and profiles.
- Verify Facebook, LinkedIn and Twitter personal profiles.



 1. For Windows 7,XP and Vista.
1. For Windows 7,XP and Vista. 2. For Windows 8, 8.1 and 10.
2. For Windows 8, 8.1 and 10.
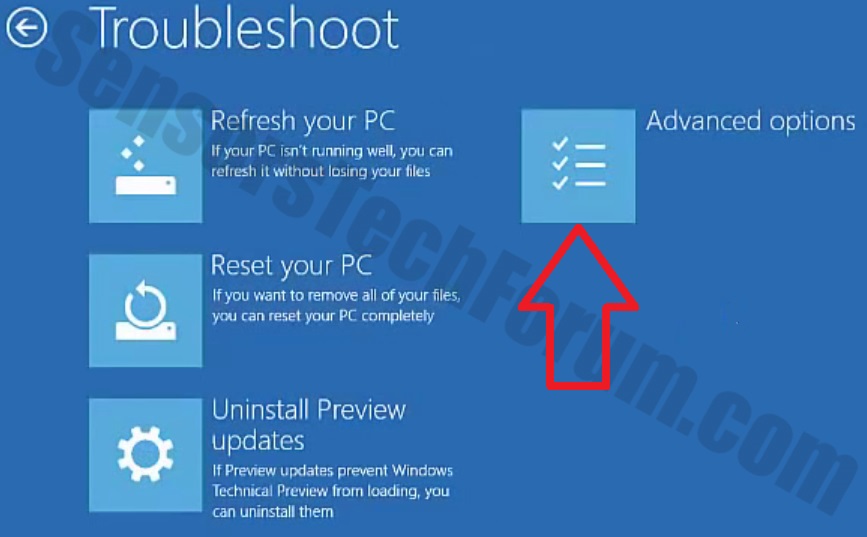
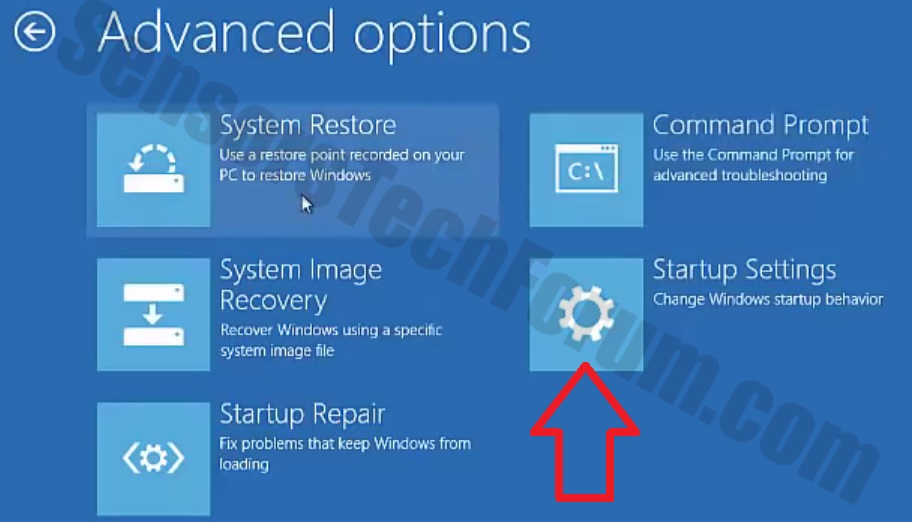

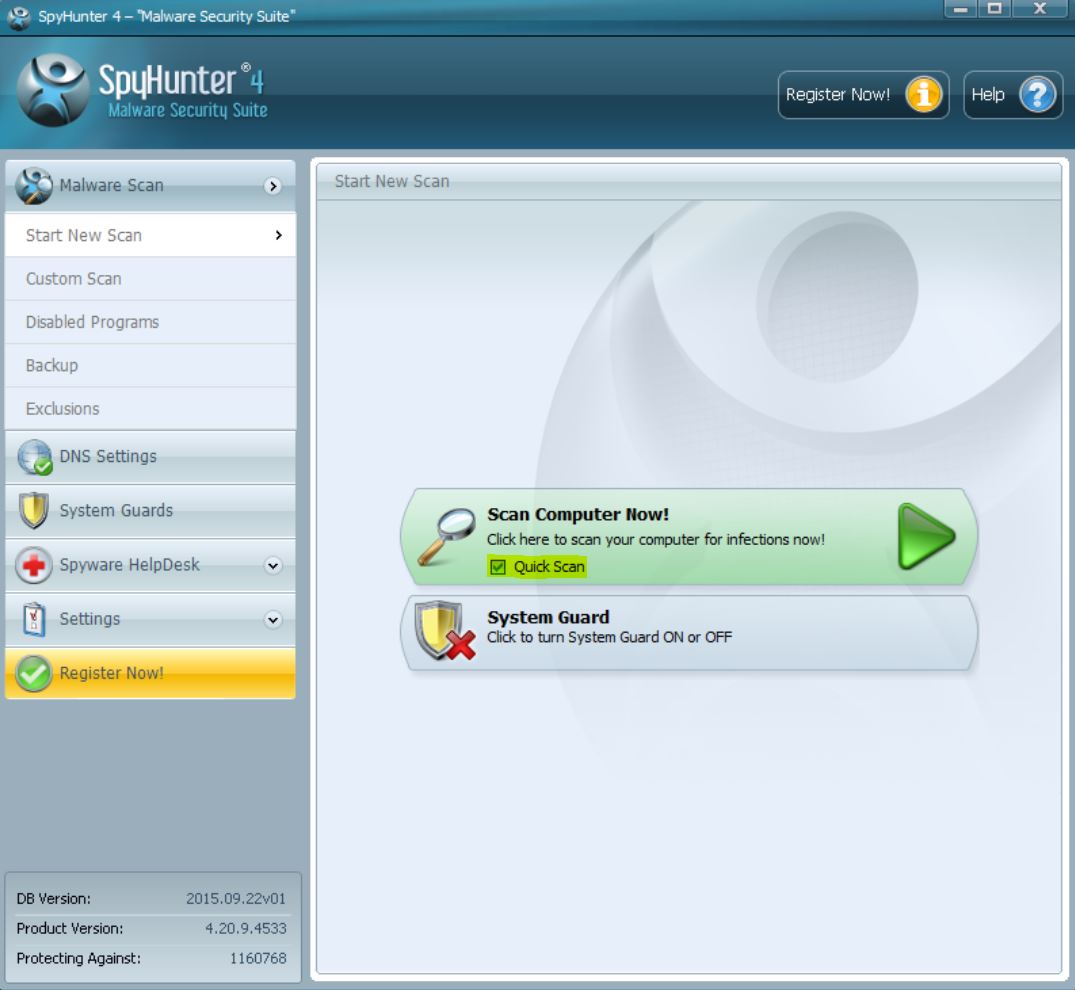
 1. Install SpyHunter to scan for and remove Files1147@gmail(.)com.
1. Install SpyHunter to scan for and remove Files1147@gmail(.)com.
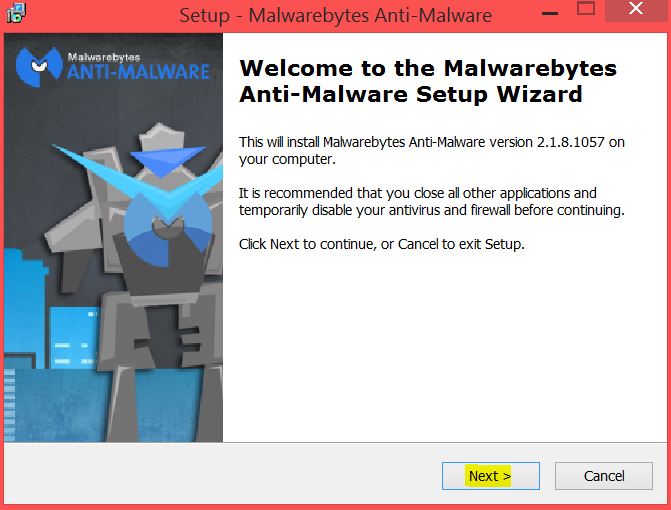
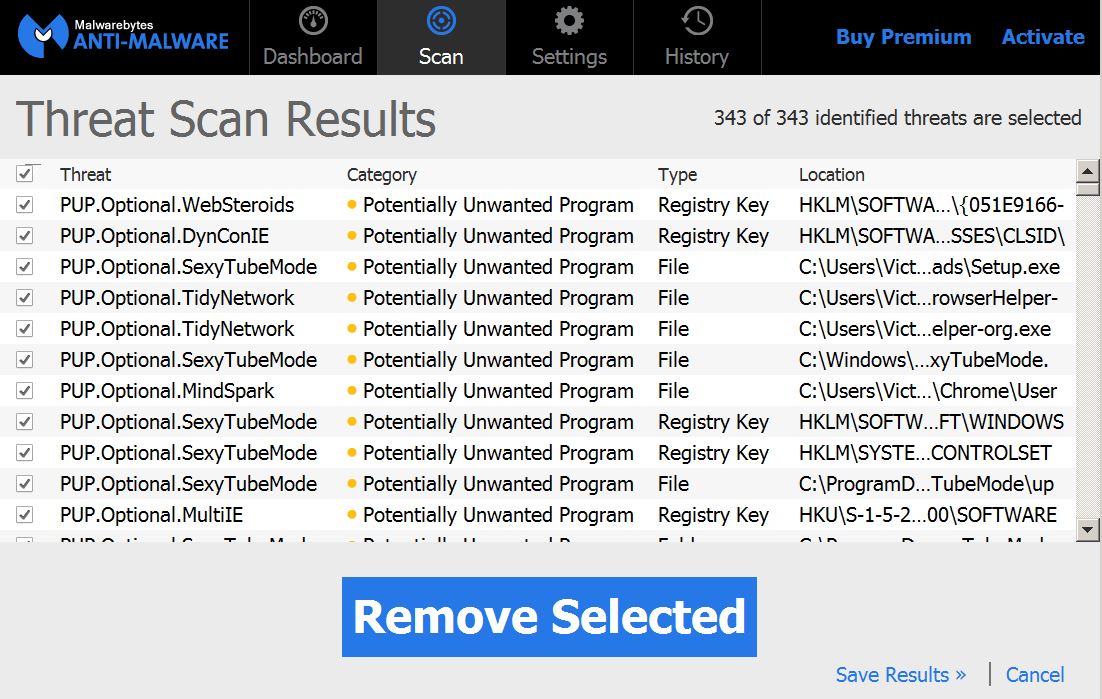
 1. Install Malwarebytes Anti-Malware to scan for and remove Files1147@gmail(.)com.
1. Install Malwarebytes Anti-Malware to scan for and remove Files1147@gmail(.)com.
 1. Install STOPZilla Anti Malware to scan for and remove Files1147@gmail(.)com.
1. Install STOPZilla Anti Malware to scan for and remove Files1147@gmail(.)com.